This section explains the preparations for setting up the network environment.
Conditions | Necessary Preparations |
|---|---|
When automatically configuring the network | Create network resources |
When using IBP | Create an IBP uplink set |
When using an iSCSI LAN for iSCSI boot | Create a network definition file for iSCSI boot |
When using Link Aggregation | Pre-configure link aggregation for LAN switch blades and L2 switches |
When using NICs other than those in the default configuration of the automatic network configuration used when using blade servers | Create a server NIC definition |
When using VMware on rack mount or tower servers to use automatic virtual switch configuration | Create a server NIC definition |
When deploying L-Servers even if the service console and port group is the same, when VMware is being used for server virtualization software | Create the VMware excluded port group definition file |
When registering network devices as resources | Create network resources |
When using the automatic configuration function for network devices registered as network device resources | Create model definitions for the network devices |
Create a folder for registering rulesets | |
Register sample scripts |
By connecting the NIC for an L-Server to a network resource, the following settings are automatically configured.
Automatic configuration for LAN switch blades (physical/virtual L-Servers)
Network configuration for blade servers (physical/virtual L-Servers)
Configuration for rack mount or tower servers (physical/virtual L-Servers)
IP address auto-configuration (virtual L-Servers)
Automatic configuration for L2 switches
Automatic VLAN Configuration for LAN Switch Blades (Physical/Virtual L-Servers)
VLANs are automatically configured on LAN switch blades.
There are the following three types of firmware for LAN switch blades:
Switch Firmware
Provides layer 2 switch functions.
End-Host Firmware
This provides the layer 2 switch functionality and pin connection functionality.
IBP Firmware
Delivers virtualization.
In Resource Orchestrator, operation of a LAN switch blade using Switch firmware is called Switch mode, operation using end-host firmware is called end-host mode, and operation using IBP firmware is called IBP mode.
For details, refer to the manual of the LAN switch blade.
Switch Mode/End-Host Mode
VLANs are automatically configured for a LAN switch blade port.
Automatic configuration for an internal connection port
Automatic configuration of tagged VLANs and port VLANs for server blade internal connection ports is performed.
Automatic configuration for an uplink port
Automatic configuration of tagged VLANs that connect to network devices, such as access switches out of chassis, is performed.
Information
Automatic configuration of tagged VLANs for uplink ports is triggered by the creation or modification of network resources. Modifying network resources here means the addition of uplink ports.
Note
When automatically configuring tagged VLANs for uplink ports, the following functions must be enabled:
Automatic network configuration
Automatic configuration for uplink ports
Set the link aggregation in advance if the VLAN auto-configuration of the external ports making up the link aggregation is to be enabled.
When configuring the port VLAN for an uplink port, manually configure the settings from the server resource tree on the ROR console.
Creating the following network resources may generate network loops.
Automatically configuring VLAN for an uplink port
Specifying multiple uplink ports on a single LAN switch blade
In these cases, take actions to prevent network loops, such as disconnecting the cables for uplink ports, and then create network resources.
Untagged VLAN 1 cannot be used as an external port that is the target of VLAN auto-configuration.
If untagged VLAN 1 is to be used, disable VLAN auto-configuration and set the VLAN manually.
The VLAN set for external ports by VLAN auto-configuration will not be automatically deleted even if the relevant network resource is deleted.
The infrastructure administrator should check the network configuration, and if the VLAN settings of the external ports are deemed unnecessary, then they should be deleted from the VLAN settings for LAN switch blades in the ROR console.
VLAN auto-configuration for external ports that compose link aggregations can be used for LAN switch blades in the following blade servers where the mode is switch or end host.
Blade Servers
PRIMERGY BX400
PRIMERGY BX900
Switch blade
PY CB Eth switch/IBP 10Gb 18/8
See
For details on how to create network resources which automatically configure VLANs for LAN switch blade uplink ports, refer to "3.5.2 Changing VLANs Set for External Connection Ports of LAN Switch Blades" in the "User's Guide for Infrastructure Administrators (Resource Management) CE".
IBP Mode
Connect to the port group that was created beforehand. Automatic configuration of VLANs is not supported.
Network Configuration for Blade Servers (Physical/Virtual L-Servers)
Automatic Network Configuration
When the NIC for an L-Server and a network resource are connected, the network is automatically configured.
The explanation given here is for a non-redundant configuration of a LAN switch blade. For automatic configuration items including redundant configuration, refer to "Table 4.1 Network Configurations for Blade Servers".
For details on the timing of automatic configuration, refer to "Table 1.5 Timing of Automatic Network Settings Execution".
For the configurations that support automatic configuration, refer to the following:
For Physical L-Servers
Refer to "Physical Server (Blade Server) Configuration to Support Automation of Network Configuration in Resource Orchestrator" in "D.6.1 Automatic Network Configuration".
For Virtual L-Servers
[VMware]
Refer to "Default Blade Server Configuration to Support Automation of Network Configuration in Resource Orchestrator" in "E.2.5 Setup".
[Hyper-V]
Refer to "Default Blade Server Configuration to Support Automation of Network Configuration in Resource Orchestrator" in "E.3.4 Setup".
See
For details on the rcxadm nicdefctl command, refer to "1.7.16 rcxadm nicdefctl" in the "Reference Guide (Resource Management) CE".
For details on the server NIC definitions, refer to "2.11 Server NIC Definition" of the "Reference Guide (Resource Management) CE".
Figure 4.17 Automatic Network Configuration for Blade Servers
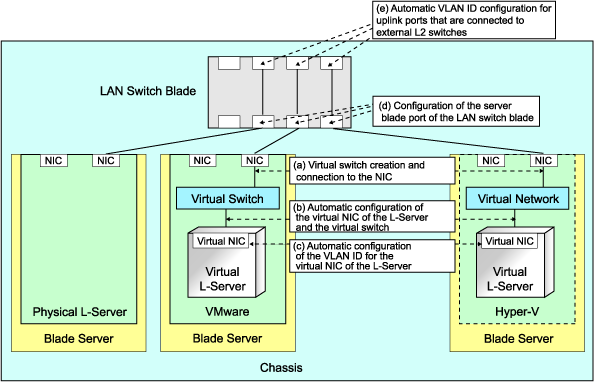
Physical L-Server | Virtual L-Server | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
VMware | Hyper-V | RHEL5-Xen | RHEL-KVM | Oracle VM | |||||||||
Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | ||||||||
Without | With | Without | With | Without | With | Without | With | Without | With | Without | With | ||
A | Creating virtual switches and connecting to NICs (*2) | - | - | Yes (*3) | Yes | Yes (*3) | Yes (*4) | No | No | No | No | No | No |
B | Automatic connection between L-Server virtual NICs and virtual switches (*5) | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
C | Automatic VLAN ID configuration for L-Server virtual NICs | - | - | Yes | Yes | Yes | Yes | No | No | No | No | No | No |
D | Configurations for the server blade ports of LAN switch blades | Yes (*6) | Yes | Yes (*3, *7) | Yes (*7) | Yes (*3, *7) | Yes (*4, *7) | No | No | No | No | No | No |
E | Automatic VLAN ID configuration for uplink ports that are connected to external L2 switches (*7) | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
Yes: Configured in Resource Orchestrator
No: Not configured in Resource Orchestrator
-: None
*1: LAN redundancy.
For physical L-Servers, the NIC of the physical L-Server is the target of LAN redundancy.
For virtual L-Servers, the NIC connected to the virtual switch is the target of LAN redundancy.
*2: Replace as follows for each server virtualization software.
VMware | Creating virtual switches and port groups |
Hyper-V | Creating a virtual network |
RHEL5-Xen | Creating a virtual bridge |
Information
When using VMware as server virtualization software, the following configurations are automatically performed:
Virtual switch creation
VLAN configuration for virtual switches
Teaming connection of virtual switches and NICs
When using Hyper-V as server virtualization software, the following configurations are automatically performed:
Virtual network creation
VLAN configuration for virtual networks
Teaming connections of virtual networks and NICs are automatic if teaming settings are configured for NICs in advance.
*3: In order to configure the network automatically, it is necessary to create a server NIC definition suitable for the server to be configured, and then reflect the definition on the manager using the rcxadm nicdefctl commit command in advance.
For details on the server NIC definitions, refer to "2.11 Server NIC Definition" of the "Reference Guide (Resource Management) CE".
For details on the rcxadm nicdefctl command, refer to "1.7.16 rcxadm nicdefctl" of the "Reference Guide (Resource Management) CE".
When not using server NIC definitions, manually configure the network.
*4: Automatic configuration is possible for redundancy configurations with Intel PROSet or PRIMECLUSTER GLS.
*5: Replace as follows for each server virtualization software.
VMware | Connections Virtual NICs of L-Servers and Port Groups of Virtual Switches |
Hyper-V | Connections Virtual NICs of L-Servers and Virtual Networks |
RHEL5-Xen | VLAN ID configuration for the L-Server virtual network interface and connection with virtual bridges which have been created manually in advance |
Information
If VMware is used as the server virtualization software and the same VLAN ID is used for the service console and port group, the port group and L-Server can be connected by creating a VMware excluded port group definition file.
For details on VMware excluded port group definition files, refer to "2.12 VMware Excluded Port Group Definition File" in the "Reference Guide (Resource Management) CE".
*6: Configure a port VLAN or a tagged VLAN. For details on how to configure VLANs, refer to "2.4.6 Configuring VLANs on Internal Connection Ports" in the "User's Guide for Infrastructure Administrators (Resource Management) CE".
*7: Configure a tagged VLAN.
In Resource Orchestrator, when a virtual L-Server is connected to the admin LAN that has the same subnet address as the admin server, to preserve security, virtual switches are not automatically created.
Ensure the network security of the communication route between the admin server and the virtual L-Server, and then create virtual switches.
Manual Network Configuration
For configurations other than the default blade server configuration that supports automatic network configuration, manually configure the network, referring to the following:
For Physical L-Servers
Refer to "D.6.2 Manual Network Configuration".
For Virtual L-Servers
[VMware]
Refer to "Manual Network Configuration" in "E.2.5 Setup".
[Hyper-V]
Refer to "Manual Network Configuration" in "E.3.4 Setup".
Network Configuration for Rack Mount or Tower Servers (Physical/Virtual L-Servers)
For rack mount or tower servers, make connections between L-Server virtual NICs and virtual switches.
Figure 4.18 Network Configuration for Rack Mount or Tower Servers
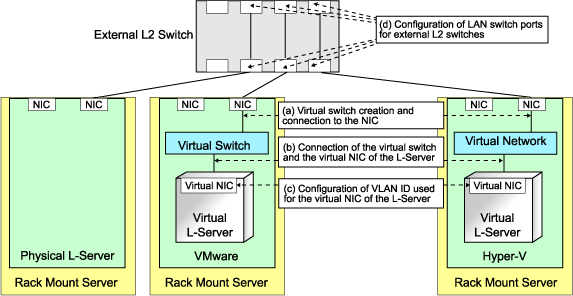
Physical L-Server | Virtual L-Server | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
VMware | Hyper-V | RHEL5-Xen | RHEL-KVM | Oracle VM | |||||||||
Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | Redundancy (*1) | ||||||||
Without | With | Without | With | Without | With | Without | With | Without | With | Without | With | ||
A | Creating virtual switches and connecting to NICs (*2) | - | - | Yes | Yes | No | No | No | No | No | No | No | No |
B | Connection between L-Server virtual NICs and virtual switches (*3) | - | - | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
C | Configuration of VLAN IDs used by L-Server virtual NICs | - | - | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
D | Configuration of LAN switch ports for external L2 switches (*4) | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
Yes: Configured in Resource Orchestrator
No: Not configured in Resource Orchestrator
*1: LAN redundancy.
For physical L-Servers, the NIC of the physical L-Server is the target of LAN redundancy.
For virtual L-Servers, the NIC connected to the virtual switch is the target of LAN redundancy.
*2: In order to configure the network automatically, it is necessary to create a server NIC definition suitable for the server to be configured, and then reflect the definition on the manager using the rcxadm nicdefctl commit command in advance.
For details on the server NIC definitions, refer to "2.11 Server NIC Definition" of the "Reference Guide (Resource Management) CE".
For details on the rcxadm nicdefctl command, refer to "1.7.16 rcxadm nicdefctl" of the "Reference Guide (Resource Management) CE".
Replace as follows for each server virtualization software.
VMware | Creating virtual switches and port groups |
Hyper-V | Creating a virtual network |
RHEL5-Xen | Creating a virtual bridge |
Information
When using VMware as server virtualization software, the following configurations are automatically performed:
Virtual switch creation
VLAN configuration for virtual switches
Teaming connection of virtual switches and NICs
The model names of rack mount or tower servers that can perform virtual switch creation, VLAN configuration, and teaming connection are as follows:
RX100 S5/S6
RX200 S4/S5/S6
RX300 S4/S5/S6
RX600 S4/S5
RX900 S1
TX150 S6/S7
TX200 S5/S6
TX300 S4/S5/S6
*3: Replace as follows for each server virtualization software.
VMware | Connections Virtual NICs of L-Servers and Port Groups of Virtual Switches |
Hyper-V | Connections Virtual NICs of L-Servers and Virtual Networks |
RHEL5-Xen | VLAN ID configuration for the L-Server virtual network interface and connection with virtual bridges which have been created manually in advance |
Information
If VMware is used as the server virtualization software and the same VLAN ID is used for the service console and port group, the port group and L-Server can be connected by creating a VMware excluded port group definition file.
See
For details on VMware excluded port group definition files, refer to "2.12 VMware Excluded Port Group Definition File" in the "Reference Guide (Resource Management) CE".
*4: Configured by network device automatic configuration.
IP Address Auto-Configuration (Virtual L-Servers)
[Windows/Linux] [VMware] [Hyper-V] [KVM]
If a subnet address has been set for the network resource, the IP address can be automatically set when deploying an image to an L-Server.
The settings for the IP address, subnet mask and default gateway are configured according to DHCP settings.
[Hyper-V]
IP addresses can be automatically configured, on the following guest OS's on which the integrated services are installed.
Microsoft(R) Windows Server(R) 2008 R2
Microsoft(R) Windows Server(R) 2008
Microsoft(R) Windows Server(R) 2003 R2
Microsoft(R) Windows Server(R) 2003
Microsoft(R) Windows(R) 7
Microsoft(R) Windows Vista(R)
Microsoft(R) Windows(R) XP
[KVM]
When the guest OS type is Linux, IP addresses can be automatically configured.
[Xen] [Oracle VM]
Automatic configuration of IP addresses is not supported.
If a subnet address is set for a network resource, set an IP address manually after deploying an image to an L-Server (Also set an IP address manually on the DNS server).
For details on how to check IP addresses, refer to the Note of "10.3.4 [Network] Tab" in the "User's Guide for Infrastructure Administrators (Resource Management) CE".
If no subnet address has been set, manually set a subnet address for operation on the DHCP server after deploying an image to an L-Server.
Automatic Configuration for L2 Switches
When an L-Server or a firewall resource is deployed on an L-Platform, definitions such as interfaces can be automatically configured on the L2 switch on the communication route, using a script created in advance.
Available Network Configurations
Available network configurations and configuration methods in Resource Orchestrator are given below.
Non-Redundant Configuration
For Physical L-Servers
Refer to "D.6.2 Manual Network Configuration".
For Virtual L-Servers
Settings differ according to the server virtualization software being used.
[VMware]
Refer to "Manual Network Configuration" in "E.2.5 Setup".
[Hyper-V]
Refer to "Manual Network Configuration" in "E.3.4 Setup".
[Xen]
Refer to "Manual Network Configuration" in "E.4.4 Setup".
[KVM]
Refer to "Manual Network Configuration" in "E.6.4 Setup".
[Oracle VM]
Refer to "Manual Network Configuration" in "E.5.4 Setup".
Redundant Configuration
For Physical L-Servers
Refer to "D.6.1 Automatic Network Configuration" and "D.7.4 Network Redundancy and VLAN Settings of L-Servers".
For Virtual L-Servers
Settings differ according to the server virtualization software being used.
[VMware]
Refer to "Automatic Network Configuration" in "E.2.5 Setup".
[Hyper-V]
Refer to "Automatic Network Configuration for Blade Servers" in "E.3.4 Setup".
[Xen]
Refer to "Manual Network Configuration" in "E.4.4 Setup".
[KVM]
Refer to "Manual Network Configuration" in "E.6.4 Setup".
[Oracle VM]
Refer to "Manual Network Configuration" in "E.5.4 Setup".
Non-Redundant Configuration
For Physical L-Servers
Refer to "D.6.2 Manual Network Configuration".
For Virtual L-Servers
Settings differ according to the server virtualization software being used.
[VMware]
Refer to "Manual Network Configuration" in "E.2.5 Setup".
[Hyper-V]
Refer to "Manual Network Configuration" in "E.3.4 Setup".
[Xen]
Refer to "Manual Network Configuration" in "E.4.4 Setup".
[KVM]
Refer to "Manual Network Configuration" in "E.6.4 Setup".
[Oracle VM]
Refer to "Manual Network Configuration" in "E.5.4 Setup".
Redundant Configuration
For Physical L-Servers
Refer to "D.6.1 Automatic Network Configuration".
For Virtual L-Servers
Settings differ according to the server virtualization software being used.
[VMware]
Refer to "Automatic Network Configuration" in "E.2.5 Setup".
[Hyper-V]
Refer to "Manual Network Configuration" in "E.3.4 Setup".
[Xen]
Refer to "Manual Network Configuration" in "E.4.4 Setup".
[KVM]
Refer to "Manual Network Configuration" in "E.6.4 Setup".
[Oracle VM]
Refer to "Manual Network Configuration" in "E.5.4 Setup".
Point
When Creating Physical L-Servers
For details on the network configuration example, refer to "Appendix D Design and Configuration when Creating a Physical L-Server".
When Creating Virtual L-Servers
For details on the network configuration example, refer to "Appendix E Design and Configuration for Creating Virtual L-Servers".
Network Settings for Physical L-Servers
When configuring NIC redundancy and tagged VLANs, or specifying a Red Hat Enterprise Linux image, the network on the OS is not automatically configured.
Collect an image with the preset script that configures the network at initial OS startup, and then create an L-Server using that image.
Physical L-Server network information (such as IP address, NIC redundancy, and tagged VLAN settings) is transferred to the OS as a network information file when the image is deployed to the OS.
For details on how to configure a network using a network information file, refer to "D.7.4 Network Redundancy and VLAN Settings of L-Servers".
When network configuration is not performed on the OS, create the L-Server then connect to it via the admin LAN or using the console, and configure the network on the OS on the L-Server.
Note
Depending on operating conditions of the network configuration script, a communication error may occur on the business application that is installed on the server.
Since this error cannot be detected by Resource Orchestrator, please check any network errors that occur on user applications to detect it.
When those errors occur, the server or the application must be restarted.
Restart the server using the network configuration script.
Modifying Network Resource Specifications
The following network resource specifications can be modified.
Basic information (network resource names, etc.)
Connection information (LAN segments, etc.)
Subnet information (subnet addresses, etc.)
For details on how to modify network specifications, refer to "3.6 Changing Network Resource Settings" in the "User's Guide for Infrastructure Administrators (Resource Management) CE", and "2.5.2 Modification" in the "Reference Guide (Resource Management) CE".
When using IBP, it is necessary to create an IBP uplink set for the public LAN and the admin LAN in advance.
For Physical L-Servers
Refer to "D.4 Pre-setup Preparations (Network)".
For Virtual L-Servers
When using virtual L-Servers, connect the IBP uplink sets used for the public LAN and admin LAN to the VM host regardless of VIOM, after creating each IBP uplink set.
It is not necessary to combine the name of the uplink set and the name of the network resource.
[Windows/Linux]
Create the following file in advance to define the network information used for iSCSI boot.
The network information is linked with the iSCSI boot information that is registered using the iSCSI boot operation command (rcxadm iscsictl). Refer to "2.4.2 iSCSI Boot Information" in the "Reference Guide (Resource Management) CE" beforehand.
[Windows]
Installation_folder\Manager\etc\customize_data
[Linux]
/etc/opt/FJSVrcvmr/customize_data
User Groups
iscsi_user_group_name.rcxprop
Common on System
iscsi.rcxprop
In the definition file, an item to define is entered on each line. Enter the items in the following format.
Variable = Value |
When adding comments, start the line with a number sign ("#").
Variable | Meaning | Value |
|---|---|---|
server_model.model_name.boot_nic | Specify the server model name and NIC to be booted using iSCSI. The following models can be specified:
When setting the default, specify an asterisk ("*"). | Specify the items in the following format. NIC[index] index is an integer starting from 1. |
Example
#Server Section |
The entries are evaluated in the order they are added. When the same entry is found, the evaluation will be performed on the first one.
When setting the default, specify an asterisk ("*").
When using link aggregation, configure link aggregation on the LAN switch blade and L2 switch in advance. For details on configuration of link aggregation, refer to the manual of the LAN switch blade and L2 switch.
When creating a network resource, specify the link aggregation group name as the external connection port of the network resource.
For details, refer to "C.3 Using Link Aggregation".
When using blade servers, NICs other than those in the default configuration of automatic network configuration can be used by creating and registering a server NIC definition with the manager in advance.
The created server NIC definition can be enabled by executing the rcxadm nicdefctl commit command. In the server NIC definition, define the relationship between the NICs of the managed blade servers and a physical LAN segment. By specifying this physical LAN segment from the network resource, it is possible to specify the NIC used by the network resource.
For details on the server NIC definitions, refer to "2.11 Server NIC Definition" of the "Reference Guide (Resource Management) CE".
For details on the rcxadm nicdefctl commit command, refer to "1.7.16 rcxadm nicdefctl" in the "Reference Guide (Resource Management) CE".
When using VMware on managed rack mount or tower servers, virtual switches and port groups can be automatically configured. In this case, it is necessary to create a server NIC definition and register it with the manager.
Use the rcxadm nicdefctl commit command to register the server NIC definition with the manager.
For details on the server NIC definitions, refer to "2.11 Server NIC Definition" of the "Reference Guide (Resource Management) CE".
For details on the rcxadm nicdefctl commit command, refer to "1.7.16 rcxadm nicdefctl" in the "Reference Guide (Resource Management) CE".
When using VMware as the server virtualization software, in order to deploy L-Servers even if the service console and port group is the same, it is necessary to create a VMware excluded port group definition file.
For details on VMware excluded port group definition files, refer to "2.12 VMware Excluded Port Group Definition File" in the "Reference Guide (Resource Management) CE".
The infrastructure administrator creates network configuration information (XML definition files) for registering network devices based on the network device information (admin IP address, account information, connection information) obtained from the network device administrator.
About the information to be confirmed beforehand
When specifying the ifName for a network device as the "unit connection port name" of link information
Check the ifname of a network device using the snmpwalk command.
Example
snmpwalk -v 1 -c [SNMP_community_name] [IP_address] ifName
If the information is available from the manual or vendor of the destination device, obtain it from there.
Necessary definitions based on the number of devices to be registered.
When registering each network device individually
The Netdevice element must be the first.
When registering all network devices at once
Starting with the Netconfig element, define the settings for each network device under the Netdevices element. When registering multiple network devices at once, connection information can be also defined under the Links element.
When connection information has been registered, and the connection information (in the Links element) has been specified in the network configuration information used for registering multiple network devices at the same time, all registered connection information is deleted and then the specified connection information is registered, regardless of whether registration mode (the Mode element) is specified.
When Adding Connection Information
Specify it including already registered connection information.
When not Changing Connection Information
Do not specify connection information.
Already registered connection information can be retrieved using the rcxadm netconfig export command.
When registering network devices as network devices before installing them
When a network device is registered as a network device, the monitoring function starts monitoring that device. To avoid unnecessary monitoring, specify "true" for the Maintenance element when registering devices.
This setting enables the maintenance mode, excluding that device from monitored devices. After installing a network device and making it a monitoring target, release the maintenance mode.
The Maintenance element can be specified on individual network devices (individual Netdevice elements) to be registered.
When checking account information on registration or modification of a network device as a network device
When performing network device automatic configuration, Resource Orchestrator logs in to the network device using the registered account information. For this reason, if incorrect account information is specified, automatic configuration of the network device cannot be performed.
To check in advance whether the specified account information is correct, specify "check=true" for the LoginInfo element. This allows the login process to be performed using the specified account to check that login is possible.
The LoginInfo element can be specified on individual network devices (individual Netdevice tags) to be registered.
Only account information for network devices satisfying the following conditions can be confirmed.
Vendor | Unit Name | Prompt Type | Prompt Character |
|---|---|---|---|
Fujitsu | SR-X | Login prompt | Login: |
Password prompt | Password: | ||
Command prompt (*1) | Arbitrary string# | ||
Arbitrary string> | |||
Cisco | Catalyst | Login prompt | Username: |
Password prompt | Password: | ||
Command prompt (*1) | Arbitrary string# | ||
Arbitrary string> |
*1: The "#" or ">" following arbitrary string is used as a prompt character for the command prompt.
When registering a network device that provides a Web interface for management
When a problem occurs on the system, sometimes investigation may be performed using the Web interface provided by the network device. In such cases, it was necessary to start the web interface of the network device from another Web browser. However, specifying a URL for opening the web interface of the network device for the MgmtURL element when registering the network device makes it be possible to quickly open the web interface of the network device from the ROR console.
The MgmtURL element can be specified on individual network devices (individual Netdevice tags) to be registered.
When registering redundant network devices as network devices
Network devices that have the same "vendor name" and "device name" can be registered for redundant configurations. When registering a network device that has the same vendor name and device name, specify the same value as the registered network device for "Group_ID" of the Redundancy group_id element to treat that device as being in a redundant configuration.
For the "vendor name" and "device name" of a network device, collect MIB information from the network device when registering it, and confirm that the "vendor name" and "device name" are same as the ones of the registered device.
When registering information about connections with rack mount servers
When using a rack mount server with Resource Orchestrator, it is necessary to align the NIC number of the rack mount server with the subscript of the interface name of the server OS in advance. Also, use NIC1 and NIC2 for the admin LAN.
As NIC numbers used for the public LAN are 3 or a higher number, be careful when specifying connection information.
Example
[Windows]
NIC number = the subscript of the OS interface name
The first NIC: Local Area Connection 1
The second NIC: Local Area Connection 2
[Linux]
NIC number -1 = the subscript of the OS interface name
The first NIC: eth0
The second NIC: eth1
When registering an L2 switch
When registering an L2 switch as a network device, omit the Tenant element.
When registering models other than those with model definitions for network devices
Add the model of the network device to be registered to the model definition for network devices, and register the network device after updating the model definition file.
When regularly monitoring network devices registered as network device resources
When the workload of the network or network devices is temporarily increased, the response to the communication of regular monitoring may be delayed. When this delay exceeds the time-out period, the communication for regular monitoring will be executed again.
Therefore, if the monitoring interval (Interval element) or timeout period (Timeout element) specified during registration is short, the number of communications for regular monitoring may increase. It is recommended to use the default values in order to avoid increasing the load on the network and network devices.
See
For details on network configuration information (XML definitions), refer to "2.6 Network Configuration Information" in the "Reference Guide (Resource Management) CE".
For details on the rcxadm netconfig command, refer to "1.3.7 rcxadm netconfig" in the "Reference Guide (Resource Management) CE".
For details on releasing maintenance mode, refer to "14.1 Switchover of Maintenance Mode" in the "User's Guide for Infrastructure Administrators (Resource Management) CE".
For details on model definitions for network devices, refer to "2.13 Network Device Model Definition" in the "Reference Guide (Resource Management) CE".
This section explains how to prepare to use the function for automatically configuring network devices.
Information
Automatic configuration of firewalls is not possible if they are not registered in a network pool.
Creating Model Definitions for Network Devices
Rulesets used for the function that automatically configures network devices are registered by network device model. Therefore, it is necessary to create model definitions for determining the models of network devices.
The created model definitions are enabled by registering the following XML definition file:
[Windows]
Installation_folder\Manager\etc\customize_data\network_device_model.xml
[Linux]
/etc/opt/FJSVrcvmr/customize_data/network_device_model.xml
Newly-added models can be supported by editing the model definitions.
The network device model definitions provided with sample scripts for automatic configuration of network devices are registered in the above folder when Resource Orchestrator is installed.
Information
When editing a model definition, check the sysObjectID of the network device using the snmpwalk command.
Example
snmpwalk -v 1 -c [SNMP_community_name] [IP_address] sysObjectID
If the information is available from the manual or vendor of the destination device, obtain it from there.
See
For details on model definitions for network devices, refer to "2.13 Network Device Model Definition" in the "Reference Guide (Resource Management) CE".
Note
Use the specified OID string as the SysObjectId element in the Model element to specify the model name of the network device.
The model definition file of network devices is searched from the start, and the first sysObjectID that matches will be used as the model name of the name attribute of the Model element.
When there is no matching OID string in the model definition file, the model name is not specified.
Creating a Folder for Registering Rulesets
The function for automatically configuring network devices is used by executing the scripts prepared by the infrastructure administrator for each network device.
When it is necessary to specify settings that differ according to the provided service, register these patterns as separate rules to manage them. This management is performed by the ruleset.
Create a folder for registering scripts, etc. for each ruleset.
There are two types of folders for registering rulesets; folders for L-Platform templates and folders for network resources.
Create the folders for registering rulesets for L-Platform templates with the following name:
[Windows]
Installation_folder\Manager\etc\scripts\vendor_name\unit_name or model_name\rulesets\ruleset_name\
[Linux]
/etc/opt/FJSVrcvmr/scripts/vendor_name/unit_name or model_name/rulesets/ruleset_name/
Create the folders for registering rulesets for network resources with the following name:
[Windows]
Installation_folder\Manager\etc\scripts\network_resource\ruleset_name\
[Linux]
/etc/opt/FJSVrcvmr/scripts/network_resource/ruleset_name/
Information
For "vendor_name", "unit_name", and "model_name", specify the "vendor name", "unit name", and "model name" of the target network device for script execution, respectively.
The "Vendor name", "unit name", and "model name" of a network device can be confirmed by checking the model definition (XML file) for that device.
For details on model definitions for network devices, refer to "2.13 Network Device Model Definition" in the "Reference Guide (Resource Management) CE".
Specify the folder name of "ruleset name" using up to 32 characters, including alphanumeric characters, underscores ("_"), and hyphens ("-"). This name should start with an alphabetical character.
Set a unique name for the folder name of "ruleset name", excluding the following folders in which sample scripts are registered.
[Windows]
Installation_folder\Manager\etc\scripts\
[Linux]
/etc/opt/FJSVrcvmr/scripts/
Sample Scripts
Sample scripts to be used for automatic configuration of network devices are registered in the following folder when Resource Orchestrator is installed.
[Windows]
Installation_folder\Manager\etc\scripts\original\vendor_name\unit_name\rulesets\ruleset_name\
Installation_folder\Manager\etc\scripts\original\network_resource\ruleset_name\
[Linux]
/etc/opt/FJSVrcvmr/scripts/original/vendor_name/unit_name/rulesets/ruleset_name/
/etc/opt/FJSVrcvmr/scripts/original/network_resource/ruleset_name/
The following table lists the unit names supported by the sample scripts provided by Resource Orchestrator:
Vendor | Unit Name | Type | Setting Details |
|---|---|---|---|
Fujitsu | SR-X500 | L2 switch |
|
SR-X300 | |||
IPCOMEXSC | Firewall (*1) |
| |
IPCOMEXIN | |||
Cisco | Catalyst | L2 switch |
|
ASA5500 | Firewall (*1) |
|
*1: Configure Firewall rules for the VLAN interfaces of LAN ports to use as public LANs.
The default model configuration assumed by a sample script is given below:
Figure 4.19 Default Model Configuration for a Sample Script
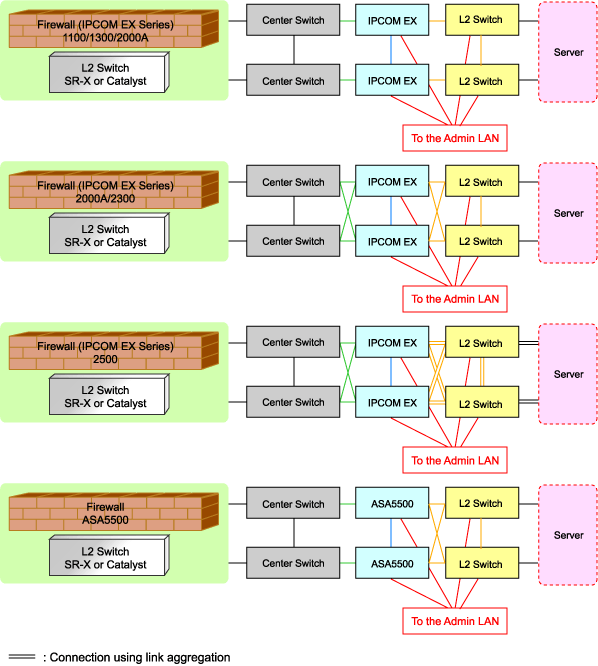
Listed below are sample ruleset names provided by Resource Orchestrator:
For the systems that configure tagged VLANs on the LAN ports connected with firewalls and servers
For the systems that configure port VLANs on the LAN ports connected with firewalls and servers
For the systems that configure tagged VLAN networks
For the systems that configure untagged VLAN networks
n: Number of "2" or larger
For the systems that configure tagged VLANs on the LAN ports connected with firewalls and servers
For the systems that configure port VLANs on the LAN ports connected with firewalls and servers
For the systems that configure tagged VLAN networks
For the systems that configure untagged VLAN networks
n: Number of "2" or larger
For the systems that use IPCOMEX1100_SC/1300_SC/2000A_SC as an IPCOM EX SC series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
LAN0.0
For Public LANs (L2 Switch Side)
LAN0.1
For the Admin LAN
LAN0.3
For Unit Synchronization
LAN0.2
For the systems that use IPCOMEX2000A_SC/2300_SC as an IPCOM EX SC series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
bnd0: Redundant LAN Channels
LAN0.0
LAN1.0
For Public LANs (L2 Switch Side)
bnd1: Redundant LAN Channels
LAN0.1
LAN1.1
For the Admin LAN
LAN0.3
For Unit Synchronization
LAN1.3
For the systems that use IPCOMEX2500_SC as an IPCOM EX SC series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
bnd0: Redundant LAN Channels
LAN0.0
LAN1.0
For Public LANs (L2 Switch Side)
bnd1: Redundant LAN Channels
LAN0.1 and LAN0.2
LAN1.1 and LAN1.2
Connection using Link aggregation
For the Admin LAN
LAN0.3
For Unit Synchronization
LAN1.3
For the systems that use IPCOMEX2000A_IN/2300_IN as an IPCOM EX IN series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
bnd0: Redundant LAN Channels
LAN0.0
LAN1.0
For Public LANs (L2 Switch Side)
bnd1: Redundant LAN Channels
LAN0.1
LAN1.1
For the Admin LAN
LAN0.3
For Unit Synchronization
LAN1.3
For the systems that use IPCOMEX2500_IN as an IPCOM EX IN series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
bnd0: Redundant LAN Channels
LAN0.0
LAN1.0
For Public LANs (L2 Switch Side)
bnd1: Redundant LAN Channels
LAN0.1 and LAN0.2
LAN1.1 and LAN1.2
Connection using Link aggregation
For the Admin LAN
LAN0.3
For Unit Synchronization
LAN1.3
For the systems that configure tagged VLANs on the LAN ports connected with firewalls and servers
For the systems that configure port VLANs on the LAN ports connected with firewalls and servers
For the systems that configure tagged VLAN networks
For the systems that configure untagged VLAN networks
n: Number of "2" or larger
For the systems that use ASA5510 as an ASA5500 series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
redundant1: Redundant LAN Channels
ethernet0/0
ethernet0/1
For Public LANs (L2 Switch Side)
redundant2: Redundant LAN Channels
ethernet0/2
ethernet0/3
For the Admin LAN
management0/0
For the systems that use ASA5520/5540/5550 as an ASA5500 series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
redundant1: Redundant LAN Channels
gigabitethernet0/0
gigabitethernet0/1
For Public LANs (L2 Switch Side)
redundant2: Redundant LAN Channels
gigabitethernet0/2
gigabitethernet0/3
For the Admin LAN
management0/0
For the systems that use ASA5580 as an ASA5500 series model for three-tier models
LAN Ports to be Used
For Public LANs (Center Switch Side)
redundant1: Redundant LAN Channels
gigabitethernet3/0
gigabitethernet3/1
For Public LANs (L2 Switch Side)
redundant2: Redundant LAN Channels
gigabitethernet3/2
gigabitethernet3/3
For the Admin LAN
management0/0
The following script lists are also provided as samples for each ruleset:
create.lst
Sample script list for additional configuration
modify.lst
Sample script list for configuration modification
delete.lst
Sample script list for configuration deletion
create_recovery.lst
Sample script list for recovery from errors detected during addition of settings
modify_recovery.lst
Sample script list for recovery from errors detected during modification of settings
connect.lst
Sample script list for configuration of interfaces adjacent to servers (only for L2 switches)
disconnect.lst
Sample script list for deletion of interfaces adjacent to servers (only for L2 switches)
connect_recovery.lst
Sample script list for recovery from errors detected during configuration of adjacent servers (only for L2 switches)
Note
The sample scripts provided by Resource Orchestrator may be added or deleted when the software is updated.
When using the sample scripts, confirm the directory on the admin server in which the sample scripts are registered beforehand.
Copy Destination of Sample Script Rulesets
Rulesets in which sample scripts are registered are copied to the folder for ruleset registration during installation and made available for use.
For example, when using an SR-X300 as an L2 switch, and an IPCOM EX1300 SC, rulesets are copied as follows:
For SR-X300
When an admin server operates on Windows
For Port Configuration
Source Folder:
Installation_folder\Manager\etc\scripts\original\Fujitsu\SR-X300\rulesets\xxx_vlan_port--SR-X300
Destination Folder
Installation_folder\Manager\etc\scripts\Fujitsu\SR-X300\rulesets\xxx_vlan_port--SR-X300
For Network Configuration
Source Folder:
Installation_folder\Manager\etc\scripts\original\network_resource\xxx_vlan_net--SR-X300
Destination Folder
Installation_folder\Manager\etc\scripts\network_resource\xxx_vlan_net--SR-X300
xxx: "tag" or "untag"
When an admin server operates on Linux
For Port Configuration
Source directory
/etc/opt/FJSVrcvmr/scripts/original/Fujitsu/SR-X300/rulesets/xxx_vlan_port--SR-X300
Destination directory
/etc/opt/FJSVrcvmr/scripts/Fujitsu/SR-X300/rulesets/xxx_vlan_port--SR-X300
For Network Configuration
Source directory
/etc/opt/FJSVrcvmr/scripts/original/network_resource/xxx_vlan_net--SR-X300
Destination directory
/etc/opt/FJSVrcvmr/scripts/network_resource/xxx_vlan_net--SR-X300
xxx: "tag" or "untag"
For IPCOM EX1300 SC
When an admin server operates on Windows
Source Folder
Installation_folder\Manager\etc\scripts\original\Fujitsu\IPCOMEXSC\rulesets\3Tier_system_firewall--IPCOMSC1
Destination Folder
Installation_folder\Manager\etc\scripts\Fujitsu\IPCOMEXSC\rulesets\3Tier_system_firewall--IPCOMSC1
When an admin server operates on Linux
Source Folder
/etc/opt/FJSVrcvmr/scripts/original/Fujitsu/IPCOMEXSC/rulesets/3Tier_system_firewall--IPCOMSC1
Destination Folder
/etc/opt/FJSVrcvmr/scripts/Fujitsu/IPCOMEXSC/rulesets/3Tier_system_firewall--IPCOMSC1