The following describes the network configuration required to operate smart workload recovery. Design the network based on the network configuration.
VPC and Subnet Design
Ensuring Connectivity with API Endpoints
Identifying Mount Targets for EFS
Network takeover
Designing Security Groups
Note
Because the smart workload recovery feature creates an instance when you switch, the switch can be interrupted if your AWS environment runs out of AZ resources.
Because AZ resource exhaustion cannot be predicted in advance, we recommend that you design the following items with all availability zones in the region in mind, rather than limiting the switched to only one availability zone.
Subnet Design
Ensuring Connectivity with API Endpoints
Identifying Mount Targets for EFS
Network Inheritance
In the event of AZ resource exhaustion, it is necessary to take measures to add a new switching destination AZ in accordance with "A.3.2.3 Changing the settings of the switch destination AZ".
Prepare a VPC and create a subnet for each AZ that you want to switch.
Configure your VPC to use DNS. When you create a VPC, you specify the following options. For more information, see the official AWS documentation.
Setting item | Value |
|---|---|
DNS hostname | Enabled |
DNS resolution | Enabled |
Figure A.3 Creating Subnets per AZ
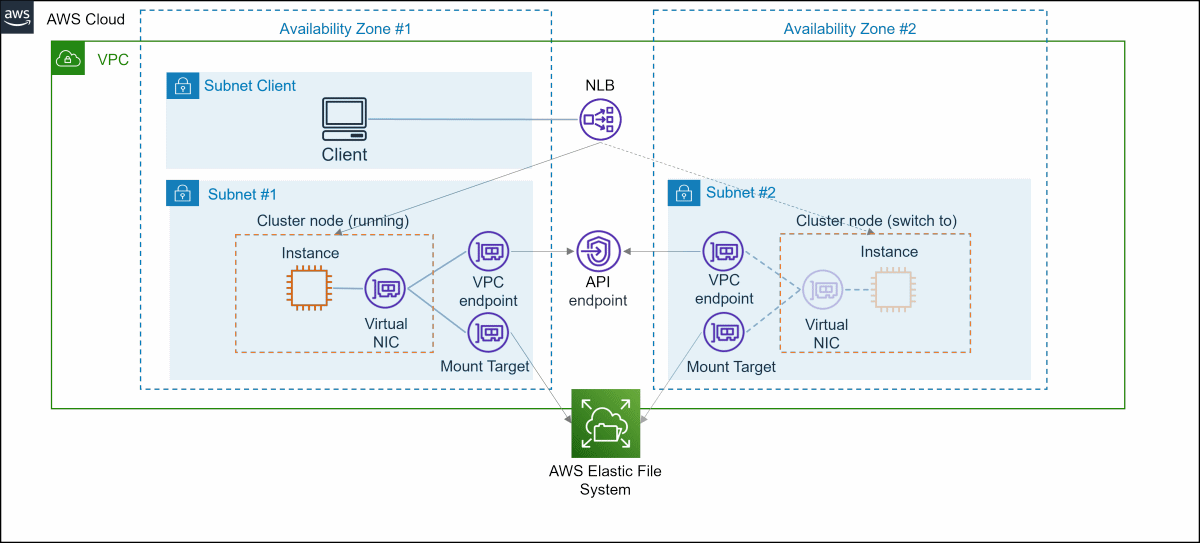
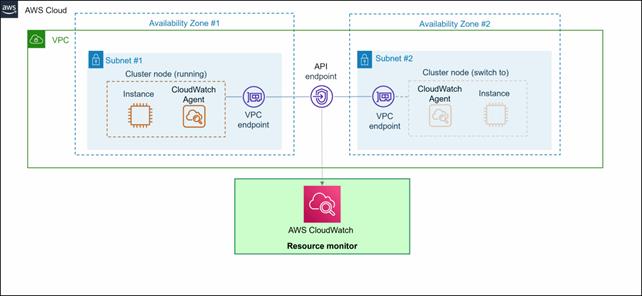
To access the API endpoint, deploy the AWS PrivateLink VPC endpoint in all AZ where you deploy cluster nodes.
CloudWatch Agent installed on your instance forwards metrics and logs to the Amazon CloudWatch API endpoint.
If you are creating a VPC endpoint for PrivateLink, specify the following options. For more information, see the official AWS documentation.
Setting item | Value | Description |
|---|---|---|
Service name | monitoring ec2 logs | Specifies the service that the CloudWatch agent uses. |
Private DNS names enabled | Enable | Configure DNS for use. |
Figure A.4 Ensuring Connectivity with AWS PrivateLink
To use EFS from an instance on a cluster node, you must have an EFS mount target on the subnet of all AZ where you deploy the cluster node.
Ensure that you have an EFS mount target for each EFS file system that is required to operate smart workload recovery. For information about EFS file systems required to operate smart workload recovery, see "A.1.4 Disk Design".
Use ELB NLB or ALB for network takeover.
Switcher terminates the instance and launches the instance in a different AZ when failure occurs. At that time, we removed the instances in the target group and added the newly launched instances.
Client access NLB and ALB based on AWS specifications. In the event of a cluster node failure, the instance to which NLB or ALB is forwarded is automatically switched for continued access. For more information on how to access it, see the official AWS documentation.
Figure A.5 ELB Network takeover
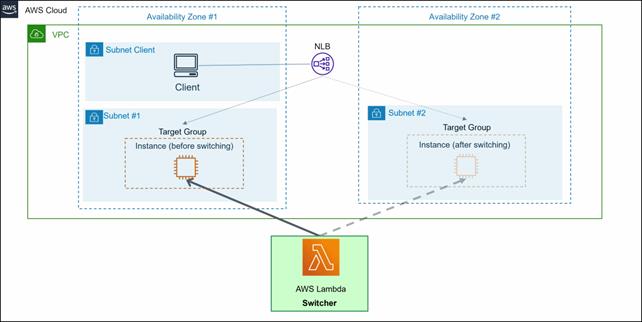
An example of NLB is shown above, but it can also be configured with ALB. When configuring with ALB, configure the network, security groups, etc. appropriately to meet your security requirements.
The target group for an ELB or ALB must be an instance. When you create a target group, you specify the following options.
Setting item | Value |
|---|---|
Target type | Instance |
Note
When handling multiple instances for switching, separate ELBs (NLB or ALB) for each instance and set up network takeover for each instance.
Describes the security group rule settings.
In addition to the rules listed here, design your security group by adding rules according to your security requirements.
Design the security rules that you want to apply to the cluster nodes.
Add the rules required for the application to work, as well as the following rules.
Allow access from NLB or ALB. For more information, see the official AWS documentation.
Destination | Protocol | Port Range | Description |
|---|---|---|---|
Security groups for VPC endpoints | tcp | 443 | Used by the CloudWatch Agent to access API endpoints. Specify the "A.1.3.5.2 Rules That Apply to VPC Endpoints" security group as the destination. |
Reserved IP address for Route 53 Resolver | tcp | 53 | Used to access DNS servers for AWS resources. |
EFS mount target security group | tcp | 2049 | Use to access an EFS mount target. |
Design the security rules that you want to apply to your VPC endpoint.
Add the following rules to your security group.
Destination | Protocol | Port Range | Description |
|---|---|---|---|
Security groups that you configure for instances on cluster nodes | tcp | 443 | Allow access from instances on cluster nodes. Specify the "A.1.3.5.1 Rules for Instances" security group as the destination. |
None
Design the security rules to apply to mount targets for EFS.
Add the following rules to your security group.
Destination | Protocol | Port Range | Description |
|---|---|---|---|
Security groups that you configure for instances on cluster nodes | tcp | 2049 | Allow access from instances on cluster nodes. Specify the "A.1.3.5.1 Rules for Instances" security group as the destination. |
None
Blackhole security group is a security group that blocks all traffic. Blackhole security groups are used by switcher.
Create blackhole security group with the following rules.
None
None