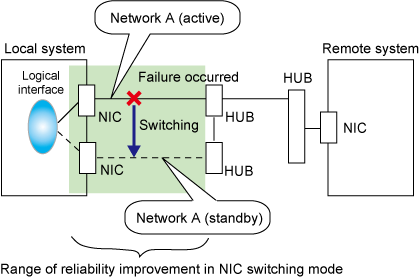
In this mode, duplicated NICs are connected to the same network and switching control of lines is performed based on the exclusive use (During normal operation, one NIC is made to go "up" for communication). A TCP/IP application can conduct communication with the remote system, irrespective of NIC switching, by using an IP address set in this "up" physical interface as its own local system IP address.
Figure 2.6 Example of duplicated operation in NIC switching mode
Information
The NIC switching mode handles the logical interface as a takeover interface. Note that it is possible to take over the physical interface without using the logical interface. For details, see "2.1.2.2 Switching function".
When using the physical interfaces eth0 and eth1, the takeover interfaces are displayed as the secondary addresses of eth0 and eth1 by the ip command.
Duplicated NICs are connected to the same network. The remote system with which communication is to be carried out can be connected to either the same network or a different network via routers.
If each network device (such as the HUB and routers) has the duplicating function in a multi-vendor environment, this mode is effective when improving overall reliability in combination with these devices. In this case, the range of duplication is defined for each vendor.
This mode is appropriate, for example, to communications in a multi-vendor environment in which UNIX servers and PC servers of other companies are mixed.
Figure 2.7 System configuration in NIC switching mode shows a system configuration for NIC switching mode:
Figure 2.7 System configuration in NIC switching mode
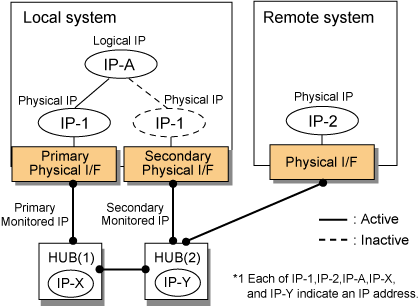
The following explains each component and its meaning:
Indicates, of the duplicated NICs, the physical interface to be used first by activating it.
Indicates the physical interface to be used after switching when a line failure is detected in the Primary physical interface.
Indicates an IP address attached to the Primary or Secondary physical interface. This IP address is always active. IPv4 address can be used for a physical interface. In case of IPv6, a link local address is automatically set as a physical IP address.
Indicates the IP address of a monitored device (HUB) obtained when the Primary physical interface is used. In NIC switching mode, it is possible to use both IPv4 and IPv6 addresses as an address form.
Indicates the IP address of a monitored device (HUB) obtained when the Secondary physical interface is used. In NIC switching mode, it is possible to use both IPv4 and IPv6 addresses as an address form.
Indicates a local IP address for communication with the remote device. In NIC switching mode, it is possible to use both IPv4 and IPv6 addresses as an address form. When using a physical IP address takeover function, it is not activated. Please refer to "2.1.2.2 Switching function" about a physical IP address takeover function.
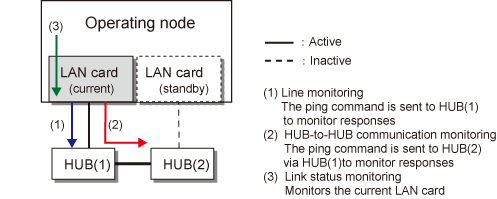
In the NIC switching mode, the transmission route is monitored in the following two functions.
Ping response monitoring
The ping command is issued periodically to the HUB connected to the NIC currently operating and its response is monitored. Optionally, HUB-to-HUB communication can be monitored (For details, see "2.4.1 HUB monitoring function").
Link status monitoring
Monitors the link status for the NIC currently operating.
If a failure is detected in the NIC currently operating, the system switches to the standby NIC and monitoring similarly starts from the standby NIC side. Then, if a failure is also detected with the standby NIC, line monitoring stops.
When using a standby patrol function, monitoring starts automatically at the recovery of all transfer routes.
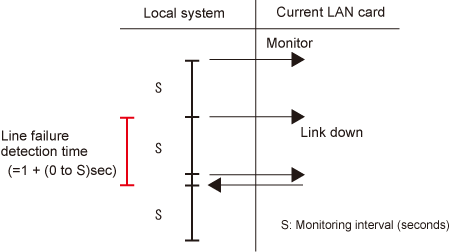
Figure 2.8 Monitoring method in NIC switching mode
The fault detection time will be one of the following:
The fault detection time by ping response monitoring
[monitoring interval (sec) x monitoring count (count)]
The fault detection time by link status monitoring
[1 (sec) + (0 to monitoring interval (sec))]
The monitoring interval can be set in the range of 1 to 300 seconds and the monitoring count can be set in the range of 1 to 300 times. By default, they are 5 seconds and 5 times respectively.
Even if the HUB monitoring function detects failure immediately after started monitoring, it does not regard as a communication line failure until the waiting time (sec) for the Ethernet linkup passed. It is possible to set the waiting time for linkup in a range of 1 to 300 seconds and a default value is 60 seconds. However, if a value is smaller than [monitoring interval (sec) x monitoring count (count)], the time set for linkup is ignored and the time set by this [monitoring interval (sec) x monitoring count (count)] is adopted.
Figure 2.9 Fault detection time by ping response monitoring for NIC switching mode
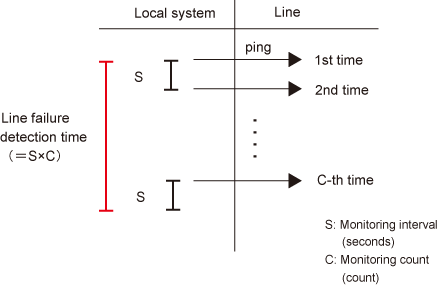
Figure 2.10 Fault detection time by link status monitoring for NIC switching mode
The following failures can be detected:
Figure 2.11 Effective monitoring range in NIC switching mode
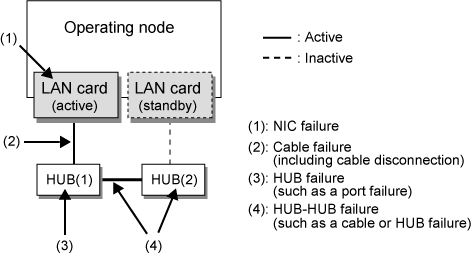
Because the failures (1) - (3) appear to be the same failure, a type of the failure cannot be specified. Each device has to be checked to make this determination.
(4) is the monitoring range only when HUB-HUB monitoring is enabled.
The line monitoring in NIC switching mode is automatically started when the system is activated and is automatically stopped when the system is stopped. In cluster operation, the line monitoring of each node is started and stopped independently. It is also possible to start or stop the line monitoring manually using the operational command (hanetpoll command).
Switching operation changes the status of an active NIC into "inactive" state and then changes the status of standby NIC to "active" so that standby NIC can run as a new active device. At this point, the MAC address and IP addresses (physical IP and logical IP) are taken over and then an ARP request packet is broadcast, in which the MAC address/IP addresses of the local node are set as the source.
It is possible to choose either a logical IP address takeover function or a physical IP address takeover function as an IP takeover mode.
Both a logical IP address and a physical IP address are taking over at the time of logical IP address takeover function use. Only a physical IP address is taking over at the time of physical IP address takeover function use, without activating a logical IP address.
When using an IPv6 address, it is not possible to use a physical IP address takeover function.
Figure 2.12 Outline of switching operation performed when a failure occurs in NIC switching mode shows an example of node internal switching.
When a failure is detected, a message to notify a failure to the system log is output. If a failure occurs when HUB-to-HUB communication monitoring is enabled, a message to notify a failure to the system log is output when a failure occurs between HUBs.
Figure 2.12 Outline of switching operation performed when a failure occurs in NIC switching mode
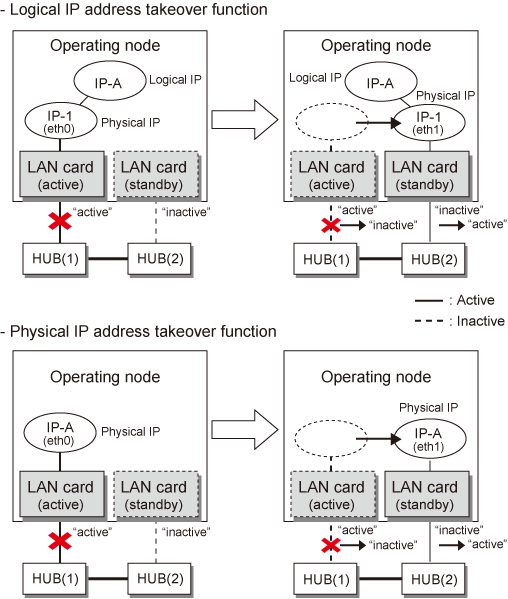
If a relevant NIC recovers after NIC switching occurs due to failure detection, you must switch it back manually via hanetnic change command.
This command recovers the system and NIC to operate as an active NIC. In addition, if you setup a Standby Patrol Function, it automatically fails back the defective NIC without manually executing hanetnic change command.
Furthermore, if in any case entire redundant NIC encounters failure, the monitoring process terminates. In such case, you must switch the NIC via hanetnic change command or restart the process via hanetpoll off/on command after recovering the network as required.
See
For details on these commands, see the following:
Any system can be connected.
The requirement for user applications that can be operated in this mode is as follows:
Application using the TCP or UDP.
Applications must be operational on a system to which multiple NICs are connected and on which multiple IP addresses are defined. (This system is called a multi-home host.) For example, a socket application needs to operate with its local IP address fixed with the bind function or set to any value. (Remote party applications do not check the IP address.)
If assigning IPv4 address to the virtual interface, physical IP address must be assigned to the redundant primary interface.
No multi-cast IP address can be used.
If a UDP application uses a virtual IP address of GLS, you have to be cautious about the following points.
If, when switching NICs, data communication for the superior application fails due to any of the following symptoms:
Loss of the transmitted packet
The "sendto(2)" function for data communication returned an "ENETUNREACH" error number, or "bind(2)" returned an "EADDRNOTAVAIL" error number
Retry the operation when an error of the superior application occurs.