View logs
This department describes how to view logs in CT Operation Log.
The procedure is as follows:
Start Log Viewer to display the CT Operation Log window.
To change the database whose operation logs will be browsed, select the desired database.
Refer to "Change the database to be viewed" for details.
Set the following items in Select Section
Select the Management Server that manages the client (CT) and smart device (agent) from Target server.
In Range of display > Sub-level contained, select whether to display only the clients (CTs) and smart devices (agents) directly under the selected group, or all clients (CTs) and smart devices (agents).
In Range settings > The violation CT is displayed only, select whether to display only the clients (CTs) and smart devices (agents) for which prohibition logs are generated, or all clients (CTs).
From the CT group tree of Select Section, select the CT group to which the client (CT) and smart device (agent) for viewing logs belong.
Logs on the client (CT) and smart device (agent) can be searched and viewed with different ranges depending on the location selected in the group tree.
When selecting server name: Logs can be searched and viewed on all clients (CTs) and smart devices (agents) belonging to the Management Server. (*)
When selecting domain name: Logs can be searched and viewed on all clients (CTs) belonging to the domain selected during Active Directory Linkage. (*)
When selecting Local group: Logs can be searched and viewed on all clients (CTs) and smart devices (agents) belonging to local groups during Active Directory Linkage.
When selecting CT group: Logs can be searched and viewed on all clients (CTs) and smart devices (agents) belonging to the CT group during Active Directory Linkage.
*) The Sub-level contained check box in Range of display must be selected.
The clients (CTs) and smart devices (agents) belonging to the CT group will be displayed in List of searched CT.
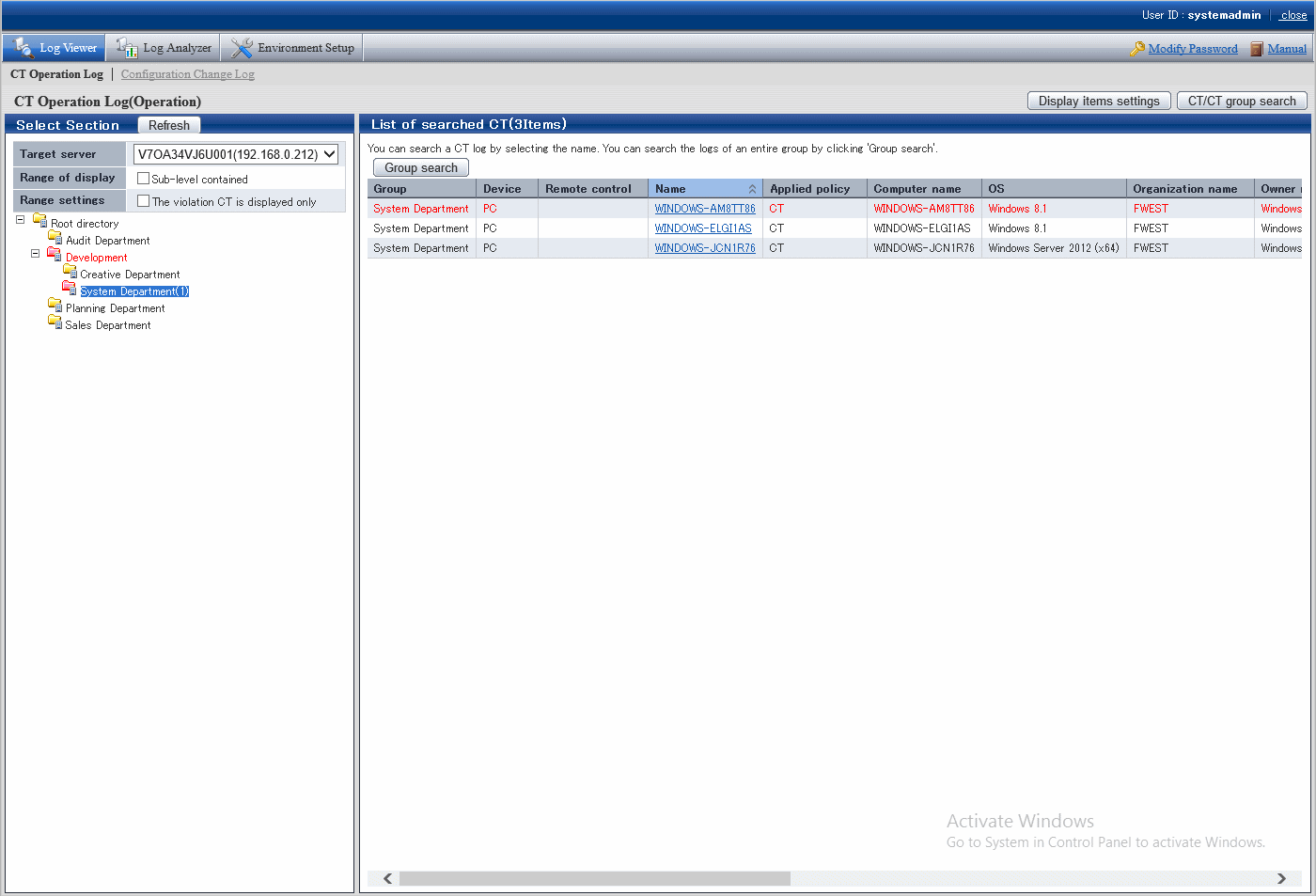
The client (CT), smart device (agent), and CT groups with prohibition logs will be displayed in red. Refer to "Display the group or client (CT) and smart device (agent) that have generated prohibition logs in red" for details.
Note
Update information of CT group and CT list in following cases
When the Log Viewer performs the following operations, the information of the CT group and CT list of the Management Server displayed in the window will not be updated to the latest status.
When the CT group tree has been modified via the Management Console
When Active Directory Linkage is performed and the group tree is modified
When adding a new client (CT) to the CT group of the Management Console using the automatic allocation file during CT registration
When Log Viewer has been started one day before (violation information has been modified)
When the applied policy is changed due to a policy change or emergency procedure request
To update to the latest information, click the Refresh button in the display area of Select Section window, and the latest information of the server selected in Target server can be displayed.
Perform any of the following operations according to the purpose of viewing CT Operation Logs:
View logs by client (CT) and smart device (agent)
Click Name of client (CT) and smart device (agent) for viewing logs in List of searched CT.
View client (CT) and smart device (agent) logs within the selected range in CT group tree
Click the Group search button in List of searched CT.
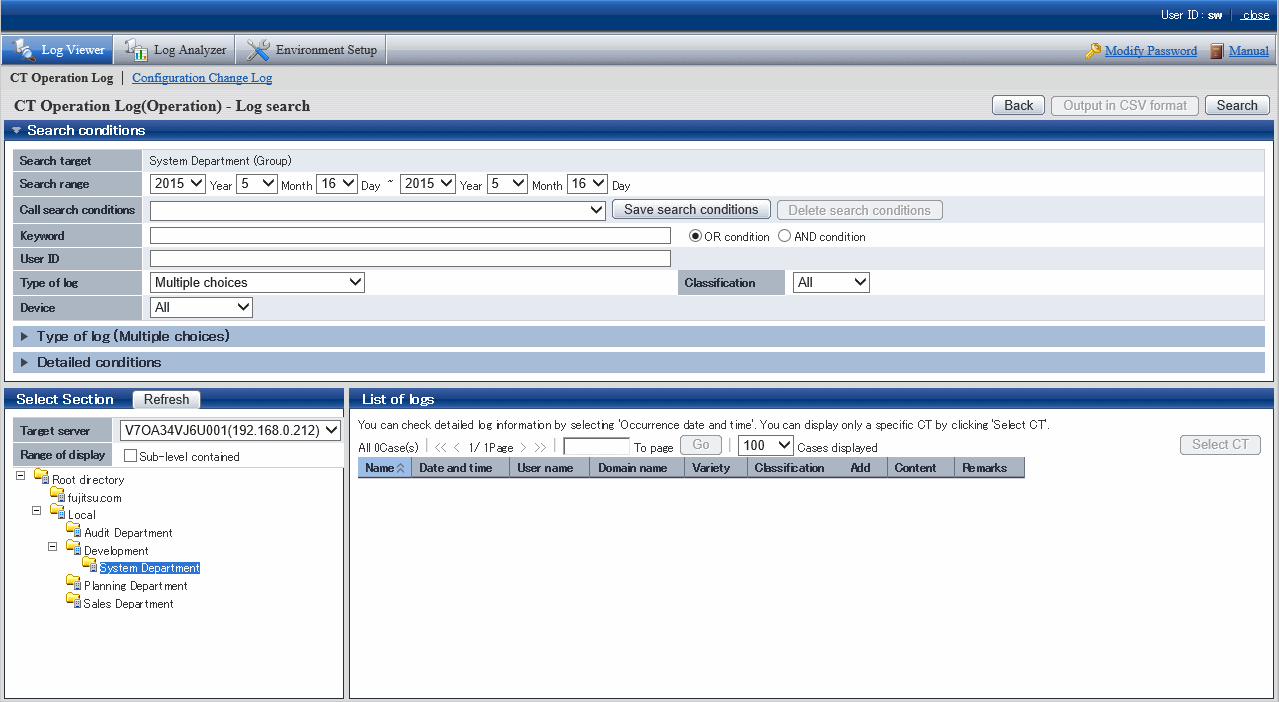
The CT Operation Log(Operation) - Log search window is displayed.
Search conditions, Type of log (Multiple choices) and Detailed conditions can be opened or closed.
After clicking Search conditions, Type of log (Multiple choices) and Detailed conditions (rightward triangle symbol), the Search conditions window will be opened.
After clicking ![]() Search conditions,
Search conditions, ![]() Type of log (Multiple choices) and
Type of log (Multiple choices) and ![]() Detailed conditions, the Search conditions window will be closed.
Detailed conditions, the Search conditions window will be closed.
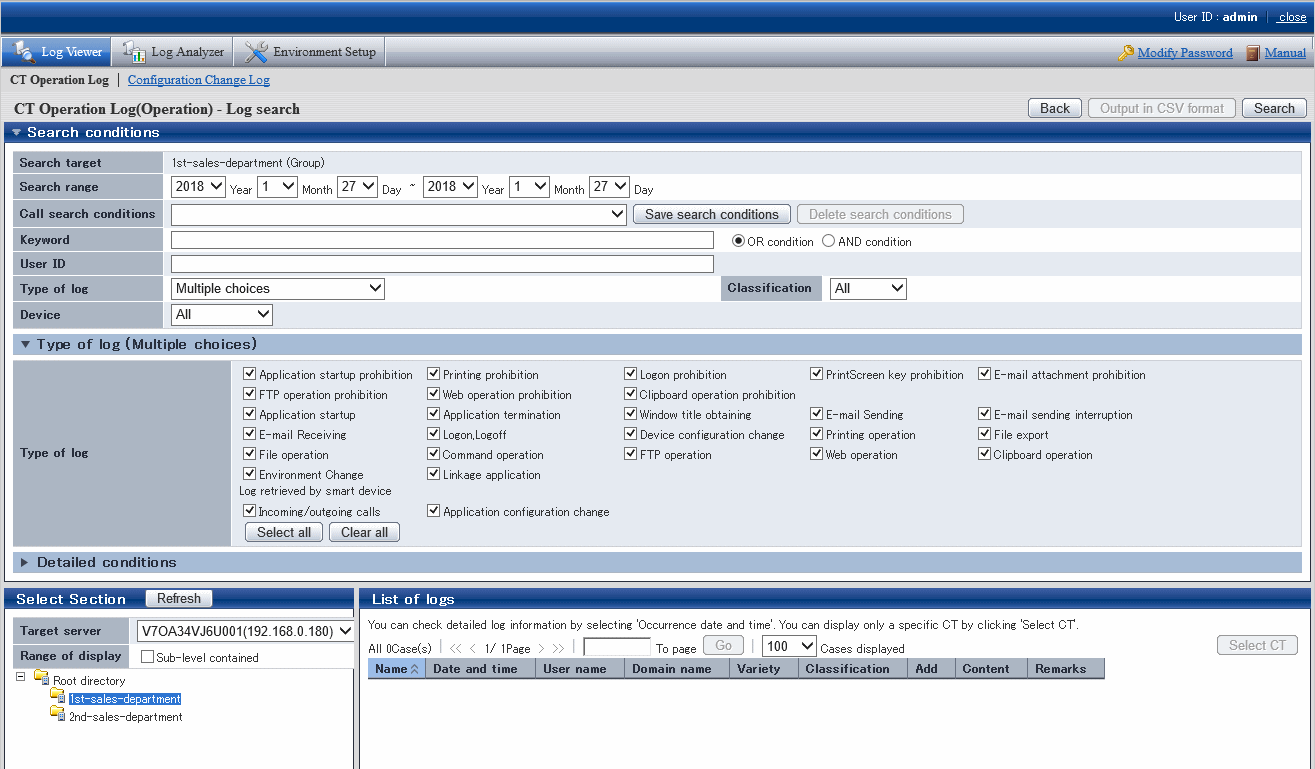
Set Search conditions
Click Detailed conditions to set detailed conditions such as drive type and log collection time, etc.
Item Name | Description |
|---|---|
Search target | The name of the client (CT) or smart device (agent) in which the search logs are collected or the CT group name will be displayed. |
Search range | Search in the specified time range. If the start time and end time of Search range are not specified, search may be performed in all periods
If no end month or day is specified, search till the end of the specified year (Dec 31).
If the specified year is omitted, the specified month and day should be omitted. As initial values, the start date and end date will be displayed as the date on the CT Operation Log - Search Log window. When selecting the The violation CT is displayed only check box of Range settings and clicking the Group search button: |
Call search conditions | This item can invoke the saved search conditions. The methods for saving/deleting search conditions are as follows:
|
Keyword | Keywords of logs can be used for searching. In addition, when specifying multiple keywords, the single-byte or double-byte space should be entered between keywords. Enter up to 128 halfwidth and fullwidth characters. Up to 10 keywords can be specified. Select OR or AND Condition if multiple keywords are specified. In the information displayed in the content column and notes column of logs, the content marked with [ ] can be set as the keyword |
User ID | Search according to user name. Only one user name can be entered. |
Type of log | Search by log type. When two or more log types are set as the search condition, select Multiple Selection. The Type of log (Multiple Selection) right under it will be opened, select the corresponding log type. |
Classification | The operations allowed or not allowed can be selected in policy setting. Select Normal to search the operations allowed and select Violation to search the operations not allowed. After All has been selected, both Normal and Violation will be selected. When selecting the The violation CT is displayed only check box of Range settings and clicking the Group Search button: |
Device | Search by device type. |
Type of log (Multiple choices)
Item Name | Descriptions |
|---|---|
Type of log | Select the type of log to be displayed in List of logs. Refer to "Types of log that can be viewed" for information about log types. Select All : Select all log types. |
Detailed Conditions
Item Name | Descriptions |
|---|---|
Type of drive | Search according to the type of drive.
The following four types can be specified and multiple specifications at the same time are allowed:
Relationship between settings of Type of log and Type of drive and searched log:
|
Time |
If Day of the Week is specified at the same time, the search will become the "AND Search" including all of the multiple conditions. |
Day of the Week | Select All: Select all check boxes in Day of a Week. Clear All: Cancel all selected check boxes in the Day of a Week menu. Day of a Week check box: When the day of the week for log collection is set as a search condition, select the correspondent day. When multiple days of the week are selected, the search will become the "OR Search" including more than one day of the week. When none are selected, it means that all are selected. If Time is specified at the same time, the search will become the "AND Search" including all of the multiple conditions. |
Click the Search button.
Note
If you specify a large number of CTs or a long search period in the search conditions, the following message may be displayed:
[LWSV-SEL003] A search may not be possible due to the large amount of data targeted for search. Continue processing?
If the conditions do not need to be reviewed, continue with processing.
If the search takes a long time, a timeout may occur. Alternatively, if there is a large number of search results, the search may be canceled and one of the following messages may be displayed:
[LVSY-ERR015] Processing will be canceled because the number of log items will exceed %d. Review the conditions.
[LWSV-ERR011] Processing will be canceled because the number of log data items (%d) was exceeded. Review the conditions.
In this case, refine the search conditions before performing the search again.
Example of Refining Search Condition:
Reduce search time
Reduce the Number of sets as search target
Set to search keyword condition
Set to search user name
View logs by CT or smart device (agent)
The CT operation log corresponding to the client (CT) will be displayed in List of logs.
View logs of client (CT) and smart device (agent) under the selected range in CT group tree
CT operation logs of all clients (CTs) and smart devices (agents) under the CT group will be displayed in List of logs.
Click the Select CT button.
The CT list under the group is displayed in Select CT.
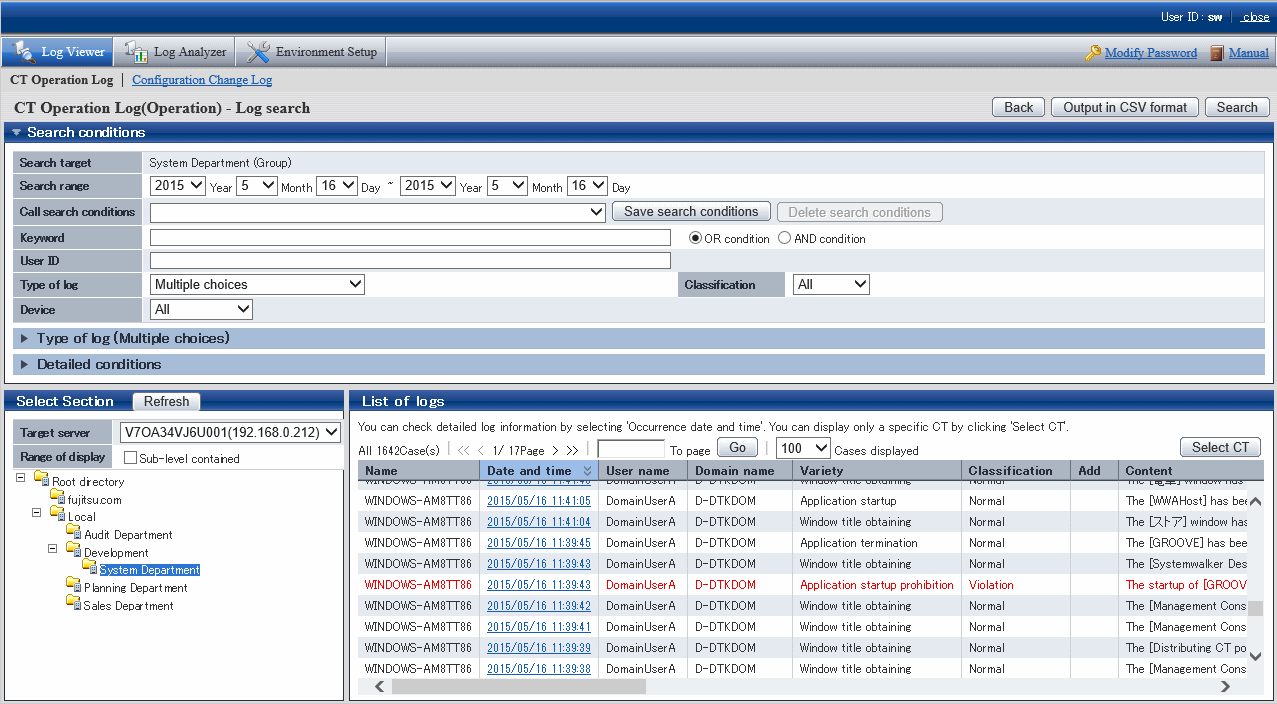
The client (CT), smart device (agent), and CT group that have generated prohibition logs will be displayed in red. Refer to "Display the group or client (CT) and smart device (agent) that have generated prohibition logs in red" for details.
When clicking Name of the client (CT) and smart device (agent) to view logs, only the CT operation log of the correspondent client (CT) and smart device (agent) will be displayed.
When clicking Number of prohibition logs of the client (CT) and smart device (agent) to view logs, only the prohibition log of the correspondent client (CT) and smart device (agent) will be displayed.
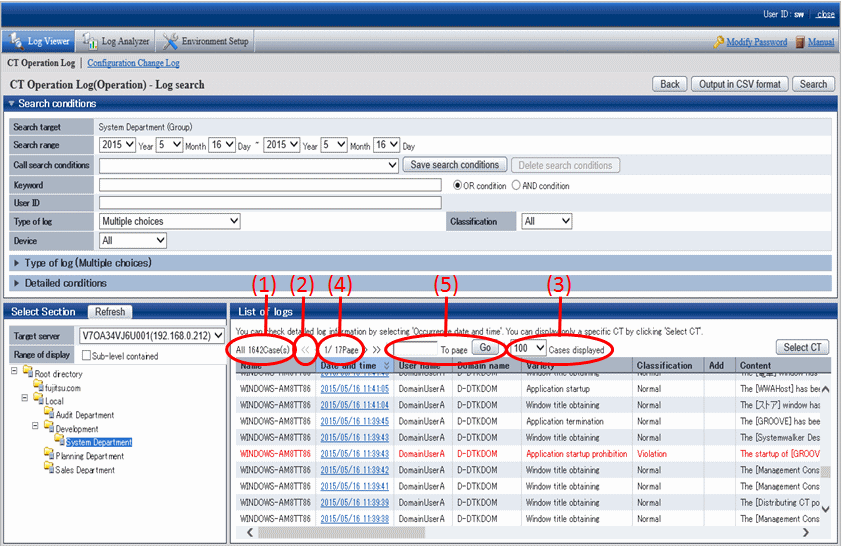
Content displayed in List of logs
(1) The number of logs corresponding to the search condition.
(2) Click the"<" to go to the previous page. Click ">" to go to the next page. Click "<<" to return to the home page. Click ">>" to go to the last page.
(3) Select the number of logs to be displayed in Window 1.
(4) Display the page of logs being viewed currently.
(5) To view logs of other pages, enter the page number and then click the Go button.
The information will be sorted after clicking the name of following items (Name, Occurrence Date and Time, User Name, etc.).
Item Name | Description | |
|---|---|---|
Client (CT) | Smart device (agent) | |
Name | This is the name that can be attached to the client (CT). Its initial value is the computer name. | This is a name that can be given to a smart device (agent). Its initial value is a telephone number, or a model name if the telephone number cannot be obtained. |
When modifying, refer to "Modify CT Policy". | ||
Date and time | This is the date and time when logs are collected in the client (CT) and smart device (agent). | |
User name | This is the user name entered when logging on the client (CT). If nobody logs on (when executing a program according to the task scheduler), the user name will be displayed as "System" when the following operation logs are collected:
If a user logs on using a Microsoft account, up to 40 halfwidth characters (20 fullwidth characters) from the start of the Microsoft account information preceding @ will be displayed. | This is the telephone number of a smart device (agent), or blank if the telephone number cannot be obtained. |
Domain name | This is the client domain name entered when logging on to a domain. It is also the computer name of the client (T) when logging on to the local computer. But it is blank when the system is Windows 98 or Windows ME (when connecting to the client (CT) of V12). If nobody logs on (when executing program according to task scheduler), the domain name will be displayed as the computer name of the client (CT) when the following operation logs are collected:
If a user logs on using a Microsoft account, the Microsoft account information will be displayed. | This is the model name of the smart device (agent). |
variety | This is the type of the log. | |
*1: When the classification is Violation |
| |
Classification | According to policy settings, the operation allowed will be displayed as Normal, and the operation that is not allowed will be displayed as Violation. When Violation logs are collected, this line will be displayed in red (settings concerning display are not required). | |
Add |
| |
Content | This is the content of the log Perform the following operations to confirm all contents:
Up to 519 halfwidth characters (259 fullwidth characters) can be displayed as the path length of target file of file operation log. In the path name containing Unicode characters, part of Unicode characters will be displayed in escape format. Unicode characters can be correctly displayed when all the following conditions are satisfied.
If the above conditions are not satisfied, Unicode characters contained in the log will be displayed as "?" or in the escape format (e.g. In "ꪪ", AAAA is a hexadecimal code with 4 or 5 digits. | |
Remarks | This is the notes of the logs. | |
Click Date and time of the displayed log.
The CT operation log(Operation) - Log search - Log details window is displayed.
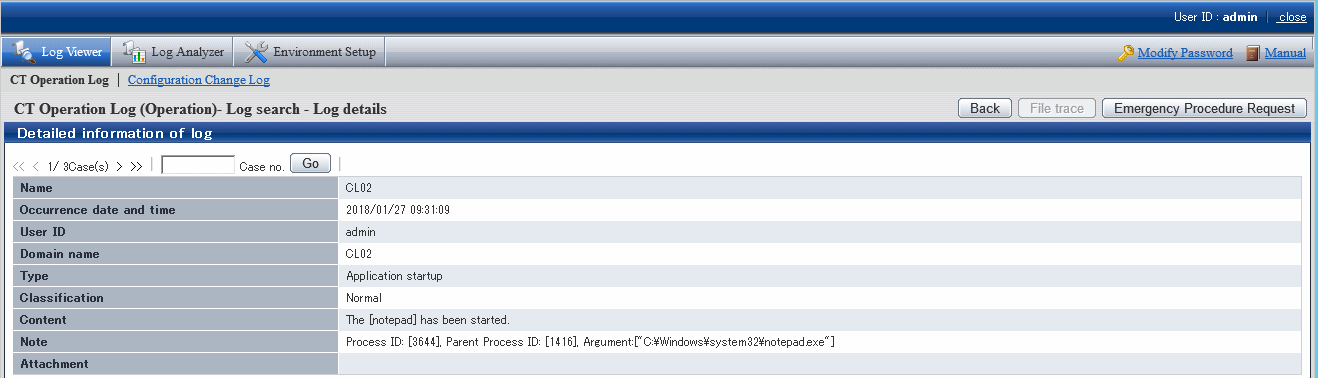
Item Name | Description | |
|---|---|---|
Client (CT) | Smart device (agent) | |
Name | For the name that can be attached to the client (CT), the initial value is the computer name. | A name that can be given to a smart device (agent). The initial value is a telephone number, or a model name if the telephone number cannot be obtained. |
When modifying, refer to "Modify CT Policy". | ||
Occurrence date and time | This is the date and time when logs are collected from the client (CT) and smart device (agent). | |
User name | This is the user name entered when logging on the client (CT). If nobody logs on (when executing program according to task scheduler), the user name will be displayed as "System" when the following operation logs are collected:
If a user logs on using a Microsoft account, up to 40 halfwidth characters (20 fullwidth characters) from the start of the Microsoft account information preceding @ will be displayed. | This is the telephone number of a smart device (agent), or blank if the telephone number cannot be obtained. |
Domain name | This is the client domain name entered when logging on to a domain. It is also the computer name of client (T) when logging on to the local computer. But it is blank when the system is Windows 98 or Windows ME (when connecting to the client (CT) of V12). If nobody logs on (when executing program according to task scheduler), the domain name will be displayed as the computer name of client (CT) when the following operation logs are collected:
If a user logs on using a Microsoft account, the Microsoft account information will be displayed. | This is the model name of the smart device (agent). |
Type | This is the type of the log. | |
*1: When the classification is Violation |
| |
Classification | According to policy settings, the operation allowed will be displayed as Normal, and the operation that is not allowed will be displayed as Violation. | |
Content | This is the content of the log Up to 519 halfwidth characters (259 fullwidth characters) can be displayed as the path length of target file of file operation log. In the path name containing Unicode characters, part of Unicode characters will be displayed in escape format. Unicode characters can be correctly displayed when all the following conditions are satisfied.
If the above conditions are not satisfied, Unicode characters contained in the log will be displayed as "?" or in the escape format (e.g. In "ꪪ", AAAA is a hexadecimal code with 4 or 5 digits). | |
Note (*1) | This is the notes of the logs. | |
Attachment (*1) | The displayed information is as follows:
| |
Session ID (*2) | This is the ID indicating the command execute in command prompt of client (CT) and the result of command execution | |
Download Content (*2) | The message displayed in Content can be downloaded in text format. | |
*1: This cannot be displayed in case of command log.
*2: This will be displayed in case of command log.
View attached data
When window title logs, file export log, clipboard operation logs and clipboard operation prohibition logs are being collected, the captured screen data, original file data of exported files and text, image, and copy (move) source file path data via clipboard can be saved simultaneously.
When collecting e-mail sending logs, the content of the sent emails and attachments can be saved.
When collecting e-mail receiving logs, the content of the received emails can be saved (attachments are not saved).
By viewing these data, the actual content of displayed windows, exported files, sent E-mails and attachment can be known.
If the View/save attached information check box is selected in Detail authority of the Administrator Information Settings window of Server Settings Tool, the captured screen data, original file data of exported files, and text, image and copy (move) source file path data via clipboard can be viewed and saved.
If the Save E-mail contents check box is selected in Detail authority of the Administrator Information Settings window of the Server Settings Tool, the content of sent E-mails and attachments can be viewed.
If the file as attached data exists, it is possible to Save original file backup
In addition, if screen capture data exists, it is possible to View/Save screen capture data.
When screen capture data exists in window title logs and PrintScreen key prohibition log", the captured screen can be viewed after clicking the link of the item value link of Attachment in the CT operation Log(Operation) - Log Search - Log Details window.
If two captured screens exist, there will be 2 links.
If one screen capture of window exists in the Attachment item of log list, the window title log with screen capture data existed will be displayed as 1; when screen capture of two windows exists, the window title log will be displayed as 2.
If screen capture data exists in PrintScreen key prohibition log, 1 will be displayed in the Attachment item of the log list.
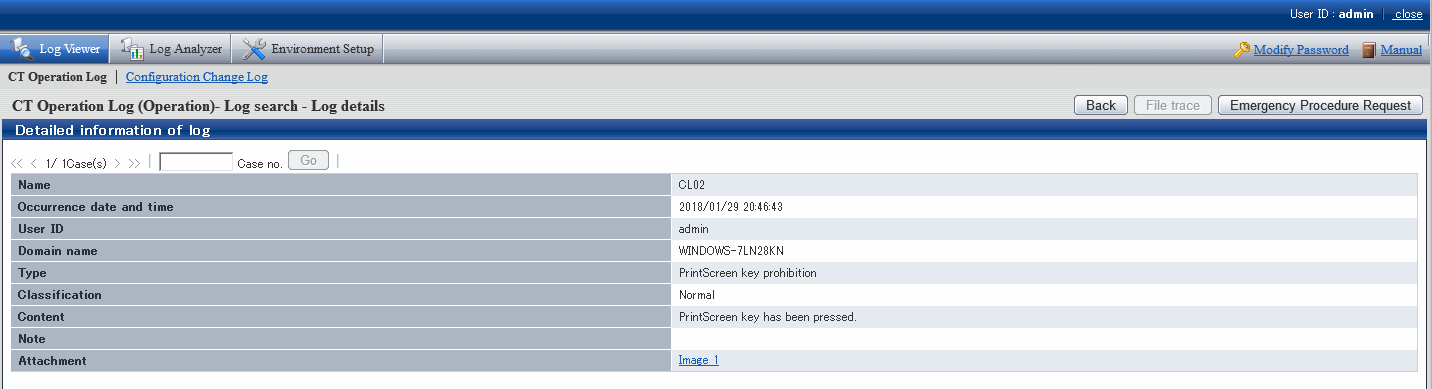
Click the link of item value of Attachment
The image of screen capture is displayed.
Note
When screen capture data cannot be displayed
The following message will be displayed after clicking the Display Image button.
[LWSV-ERR007] screen data cannot be displayed because it has not been transferred to server.
It will be displayed when the screen capture data has not been sent from the client (CT) to the Management Server, or "Save screen capture data to CT" has been set. When screen capture data has not sent from the client (CT) to the Management Server, view later after clicking the OK button. If "Save screen capture data to CT" has been set, the saving location must be modified. The location for saving and timing of sending screen capture data can be set in Terminal Operation Settings window of the Management Console. Confirm the settings and modify them according to the execution situation. For the confirmation of Terminal Operation Settings, refer to "2.4.3 Perform Terminal Operation Settings".
Click the File Saving button.
In the Saved as window that is displayed, select the location for saving, and click the Save button. The image will be saved to the specified location in the png format with default file name.
The file name of screen capture data: "CT name" + "-" + "Log occurrence date and time (yyymmdhhmnss)" + "-" + Page number (1or 2) + "-" + "Extension"
Example: PC382686-20131215203412-1.png
Click the Close button.
When the file export log, E-mail sending log, e-mail receiving log, linkage application log, clipboard operation log and clipboard operation prohibition log contain original file backups, after clicking the link of item value of Attachment in the CT Operation Log - Log Search - Log Details window, original file backups can be saved to any location. The file export log, E-mail sending log, linkage application log, clipboard operation log and clipboard operation prohibition log that contain original file backup will be displayed as 1 in the Add item of List of logs.
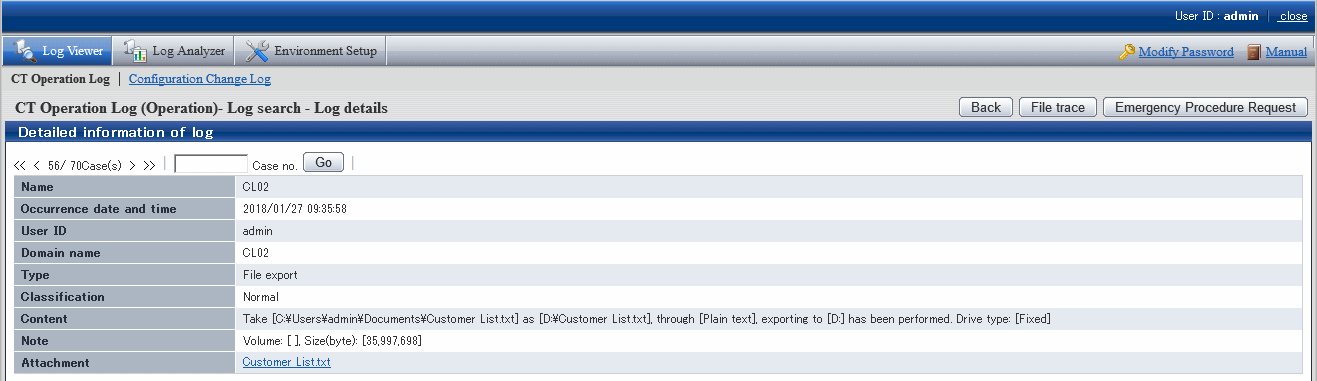
Click the link of item value in Attachment.
In the Saved as window that is displayed, select the location for saving, and click the File saving button.
The file name when backing up original files is displayed as the default value. Modify the file name and save it if necessary. If original file backups have been split in the file export log, do not change their names. Otherwise, it will no longer be possible to merge the parts to the original file.
The original file backup name of file export log:
If the original file has not been split: "Export source file name"
If the original file has been split: "AAAAA" + "_#merge.bat" or "AAAAA" + "_" + "number" + ".bin"
"AAAAA" is "Export source file name" without the extension.
"number" is the number of parts that the file has been split into.
The original file backup name of linkage application log: "CT name" + "-" + "Log occurrence date and time (yyyymmddhhmnss)" + "." + "Extension"
Example: PC382686-20131226132137.wmf
The original file backup name of E-mail sending log and e-mail receiving logs: "CT name" + "-" + "Log occurrence date and time (yyyymmddhhmnss)" + "." + "Extension"
Example:
E-mail sending log: PC382686-20130826132137.eml
E-mail receiving log: PC382686-20130826132137.txt
The original file backup name of clipboard operation log and clipboard operation prohibition log": "CT name" + "-" + "Log occurrence date and time (yyyymmddhhmnss)" + "." + "Extension"
Example:
In case of text or file: PC382686-20131226132137.txt
In case of image: PC382686-20131226132137.png
If the original file has been split in the file export log, the file will be restored to its original state.
Saves all files displayed in the Add information to the same folder.
"AAAAA" + "_#merge.bat" is executed.
"AAAAA_0001.bin" to "AAAAA" + "_" + "number" + ".bin" are merged to restore "AAAAA" + "." + "Extension".
"Extension" is the extension of the original file.
Note
The following message will be displayed after clicking the File saving button.
[LWSV-ERR010] The original file backup cannot be displayed because it has not been transferred to server.
It will be displayed when the original file backup has not been sent from the client (CT) to the Management Server, or "Save Original File Backup in CT" has been set. When the original file backup has not sent from the client (CT) to the Management Server, view later after clicking the OK button. If "Save Original File Backup to CT" has been set, the saving location must be modified. The location for saving and timing of sending original file backup can be set in Terminal Operation Settings window of the Management Console. Confirm the settings and modify them according to the execution situation. For the confirmation of Terminal Operation Settings, refer to "2.4.3 Perform Terminal Operation Settings".
When the file with no extension has a halfwidth space or "%" in its file name
The file name is displayed with halfwidth space encoded to "%20" and "%" encoded to "%25".
Change the file name to the name in Attachments and download the file, or modify the file name after downloading.
When the original file is split, the split file cannot be restored to the original one with the encoded file name.
The command prompt application may select the font which is not suitable for the displayed language. In this case, change the font on Properties of the command prompt.
Export contents displayed in [List of logs] to CSV file
After the Save CSV file check box is selected in Detailed authority in the Administrator Information Settings window of the Server Settings Tool, the content displayed in List of logs will be exported to a CSV file and saved.
In the status of displaying the logs to be exported to CSV file in List of logs, click the Output in CSV format button.
In the file download window that is displayed, click the Save button.
After selecting the folder for saving and entering the file name, click the Save button.
When a file with same name exists in the export destination, the option window indicating whether to overwrite will be displayed. Select the desired option.
For the item name and description of an exported CSV file, refer to "Log List" of Reference Manual.
When file download is not successful
When the download of CSV file, original file backup and command operation file is not successful, refer to "Preparation of Using Web Browser in PC" of Installation Guide to modify the settings of Internet Explorer.
Link with Systemwalker Desktop Patrol
When linking with Systemwalker Desktop Patrol, assets management information (Systemwalker Desktop Patrol information) of the correspondent PC can be viewed.
Select the client (CT) that displays Systemwalker Desktop Patrol assets management information.
Select Assets Management.
The asset information of Systemwalker Desktop Patrol will be displayed in other windows.