This department describes the range of logs that can be viewed by the System Administrator and department administrators, the types of logs that can be viewed and how to view logs.
Range of logs can be viewed
The System Administrator may view, search and perform CSV export of logs for all CTs/CT groups through Log Viewer.
A department administrator may view, search and perform CSV export of logs for the CT group that has been set as the department administrator itself and its subordinate groups through Log Viewer.
When viewing the operation logs of the terminal specified during remote connection via remote desktop, etc., the remote connection source terminal or remote connection target terminal can also be viewed.
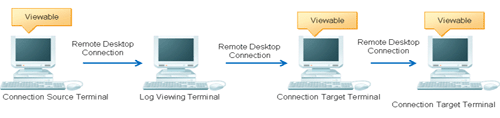
The following settings are required using this function:
Install the client (CT) in both the connection source terminal and connection target terminal
Set System settings > Connection Information between terminals of Server Settings Tool to Manage.
Set Log search settings of the Display items settings window of Log Viewer to Logs of connection source terminal and connection target terminal of the specified terminal are also searched.
Types of log that can be viewed
The logs that can be viewed in Log Viewer are shown in the following list.
Policy needs be set and reflected in the Management Console for viewing logs. For details on policy setting and reflection, refer to "2.4.1 Perform Terminal Initial Settings", "Modify CT Policy" or "3.4.2 Modify User Policy".
For details on the method of viewing logs, refer to "5.2.1 View Logs in the CT Operation Log Window", "5.2.3 View Logs in the Configuration Change Log Window".
Types of log that can be viewed | Log description | |
|---|---|---|
Client (CT) | Smart device (agent) | |
Application Startup Log | This is the log when starting an application in the client (CT). When linking with Citrix XenApp, the application startup operation performed in Citrix XenApp client will be recorded. | - |
Application Termination Log | This is the log when terminating an application in the client (CT). When linking with Citrix XenApp, the application termination in Citrix XenApp client will be recorded. | - |
Application Startup Prohibition Log | This is the log when starting a prohibited application in client (CT). | - |
Window Title Obtaining Log | This is the log when an application started in the client (CT) is displayed in the window. When linking with Citrix XenApp, the window title of the application started in the Citrix XenApp client will be recorded. | This is the log collected when the following operations are performed on a smart device (agent):
*1: Displayed in red in List of logs |
E-mail Sending Log | This is the log when E-mails have been sent in the client. | - |
Device Configuration Change Log | This is the log when device configuration has been changed in the client (CT). | This is the log collected when the following operations are performed on a smart device (agent):
*2: Displayed in red in List of logs |
Printing Operation Log | This is the log when Printing operation has been performed in the client (CT). When linking with Citrix XenApp, the printing performed in the Citrix XenApp Client will be recorded. | - |
Printing Prohibition Log | This is the log when printing is performed by an application that is not allowed to print in the client (CT). (Displayed in red in List of logs) | - |
Logon Prohibition Log | This is the log when logging on with a prohibited group in the client (CT). | - |
File Export Log | This is the log when exporting files with the File Export Utility in client (CT). | - |
PrintScreen Key Operation Log | This is the log when operating the PrintScreen key in the client (CT). When linking with Citrix XenApp, PrintScreen operations performed in the Citrix XenApp Client will be recorded. | - |
PrintScreen Key Prohibition Log | This is the log when the prohibited PrintScreen key is used in the client (CT). | - |
Web Operation Log | This is the log when the following operation is performed in client (CT):
When linking with Citrix XenApp, Web operations performed in the Citrix XenApp Client will be recorded. | - |
Web Operation Prohibition Log | This is the log when the following operation is performed in the client (CT).
| - |
FTP Operation Log | This is the log when the following operation is performed in client (CT):
When linking with Citrix XenApp, FTP operations performed in the Citrix XenApp Client will be recorded. | - |
FTP Operation Prohibition Log | This is the log when connecting to a prohibited FTP server from the client (CT). | - |
Clipboard Operation Log | This is the log when copying information (text, image) from the virtual environment to the physical environment or from the physical environment to the virtual environment via the clipboard. When linking with Citrix XenApp, clipboard operations between the Citrix XenApp Server and Citrix XenApp client will be recorded. | - |
Clipboard Operation Prohibition Log | This is the log when copying a message (text, image) from the virtual environment to the physical environment or from the physical environment to the virtual environment via the clipboard is prohibited. | - |
File Operation Log | This is the log when a file operation is performed in the client (CT). | - |
Logon/Logoff | This is the log when the following operations are performed in the client (CT):
When linking with the Citrix XenApp, connection/disconnection from the Citrix XenApp Client to Citrix XenApp Server will be recorded. | - |
Linkage Application Log | This is the log of applications linked with the client (CT). | - |
Incoming/outgoing calls log | - | This is the log of telephone numbers of incoming and outgoing calls used by a standard Android telephone on a smart device (agent). |
Application configuration change log | - | This log is collected when an application is installed or uninstalled on a smart device (agent). |
Point
How to distinguish "PrintScreen Key Operation Log" from "PrintScreen Key Prohibition Log"
"PrintScreen Key Operation Log" and "PrintScreen Key Prohibition Log" are managed as the same log type. (Managed as log type of "PrintScreen Key Prohibition Log")
Therefore, by displaying "PrintScreen Key Operation Log" as "Normal" and "PrintScreen Key Prohibition Log" as "Violation", the logs can be distinguished. When it is displayed as "Violation", it is displayed in red in List of logs.
"Configuration Change Log" refers to the logs of operation on the Management Console (modify the configuration information of CT policy/user policy and perform CSV export, etc.) and operation in Log Viewer (log search and file trace, etc.). Policy setting is not required for the purpose of log collection.
The following 4 types of logs can be viewed in the Configuration Change Log window of the Log Viewer:
Terminal Settings: Record of modified client (CT) and smart device (agent) policy.
Level composition settings: Record of modification of CT group tree such as moving a CT and smart device (agent) in the group tree.
Services Control: Record of controlled service of client (CT).
Process Control: Record of controlled process of client (CT).
For configuration change logs apart from the above, execute the DTKSTCV.EXE (export configuration change log) command, and view the logs after exporting them as CSV files. Refer to "DTKSTCV.EXE (export configuration change log)" in Systemwalker Desktop Keeper Reference Manual for details.
Note
After refreshing the tree, the window will return to status after logon
Press F5 to refresh the tree. At this time, the window will return to the status right after logon.