Set the conditions of prohibiting client (CT) and smart device (agent) operation and collected logs in the terminal initial settings.
In a 3-level system structure, perform terminal initial settings in each the Management Server. Even if the terminal initial settings is performed in the Master Management Server, it cannot be reflected to a Management Server.
The procedure is as follows:
Start Management Console
Select Terminal Initial Settings from the Operation Settings menu.
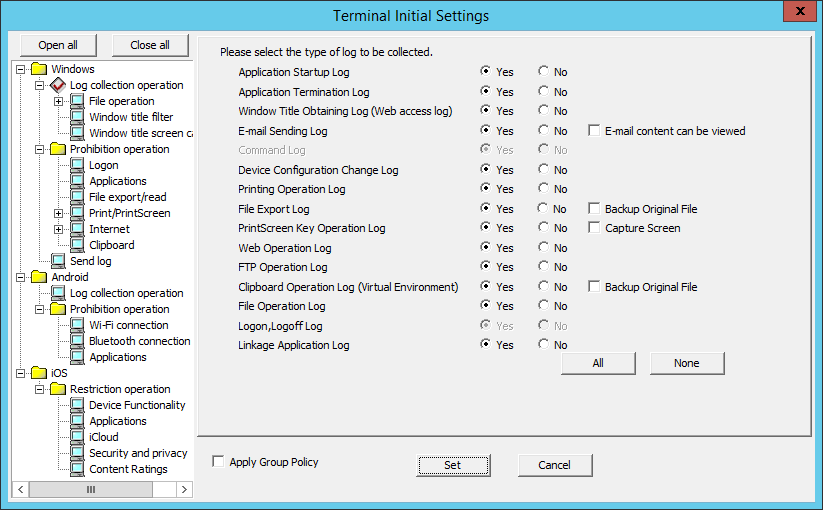
The Terminal Initial Settings window is displayed.
Item Name | Description |
|---|---|
Apply Group Policy | When registering a new CT or creating a user, set whether to apply the policy of the group to which it belongs as its CT policy or user policy . When it is selected: When it is not selected: (Initial Value) For the CT or user under the Root directory, the settings are invalid. |
After setting each policy, click the Set button.
Select a policy to be set from the tree.
When modifying the set terminal initial settings value (when setting the policy item added because of version upgrade/edition upgrade, or modifying the terminal initial settings value in the operation process), the policy should be updated for the CT after clicking the Set button.
Refer to "Modify CT Policy" or "3.4.2 Modify User Policy" for the policy reflection operation.
The following section describes the settings for each policy.
Specify the type of the log to be collected on the client (CT) in Windows > Log collection operation. When it is set to "Yes", the operation logs in the client (CT) will be collected.
The settings to be specified in Windows > Log collection operation are described below.

Item Name | Description | |
|---|---|---|
Application Startup Log | Application startup logs will be collected. | |
Application Termination Log | Application termination logs will be collected. | |
Window Title Obtaining Log(Web access log) | Window title logs at startup of window application will be collected. | |
E-mail Sending Log | E-mail sending logs will be collected. | |
E-mail content can be viewed | This can be set when E-mail Sending Log is "Yes". When it is selected: When it is not selected: (Initial Value) | |
Device Configuration Change Log | Device configuration change logs will be collected. | |
Printing Operation Log | Printing logs will be collected. When "Yes" is selected, input can be performed in the following policy:
| |
File Export Log | Logs during file export with File Export Utility will be collected. | |
Backup Original File | This can be set when the File Export Utility option is "Yes". When it is selected: When it is not selected: (Initial Value) | |
PrintScreen Key Operation Log | PrintScreen key operation logs will be collected. | |
Capture Screen | This can be set when PrintScreen Key Operation Log is "Yes". When it is selected: When it is not selected: (Initial Value) | |
Web Operation Log | The following log will be collected:
Initial Value: Yes is selected. (1*) | |
FTP Operation Log | The following logs will be collected:
Initial Value: Yes is selected. (*1) | |
Clipboard Operation Log(Virtual Environment) | Clipboard operation logs will be collected. This can be set when Do not prohibit is selected for Clipboard > Prohibition of clipboard operation between different environments.
| |
Backup Original File | This can be set when the Clipboard Operation Log (Virtual Environment) is set to "Yes". When it is selected: When it is not selected: (Initial Value) | |
File Operation Log | File operation logs will be collected. When "Yes" is selected, input can be performed in the following policies:
| |
Logon,Logoff Log | The following logs will be collected:
Initial Value: "Yes" is selected, and it cannot be modified. In the Server Settings Tool, when Not Manage is selected in the Connection information between Terminals of System Settings, the item can be Modified to Yes or No. | |
Linkage Application Log | Linkage application logs will be collected. | |
All | Select to collect all logs. | |
None | Select not to collect all logs. | |
*1: If the client (CT) was installed using custom installation, No is selected by default.
Note
About settings of Printing Operation Log
During the installation of the client (CT), when Monitoring the printing of local printer only is selected, it is assumed that the printing operation of the client (CT) is performed via the printer servers that are registered to the same Master Management Server or Management Server. (The client (CT) should also be installed on the printer sever.)
At the moment, printing logs will be collected from the printer server. Therefore, in the client (CT) that is not the printer server, even if the Printing Operation Log is set to Yes, the printing log will not be collected. However, if Printing Operation log] in the print server is set to Yes, the printing operation log can be collected.
The screening conditions for obtaining file operation logs can be set in File operation. Set the file location for log collection during access, and the process of log collection during startup. As the file operation logs can be selected and collected according to objectives, the search efficiency after collection can be improved.
The items in File operation can be set when Yes is selected in Windows > Log collection operation > File Operation Log.
Note
Do not register the software with many disk accesses.
Since the output of a large amount of logs will cause insufficient database capacity, do not register software that has significant access to disks such as antivirus software, disk check and repair software, etc.
In addition, as the software related to the OS may also output too many logs, register after confirming the performance and OS operation state on the test machine.
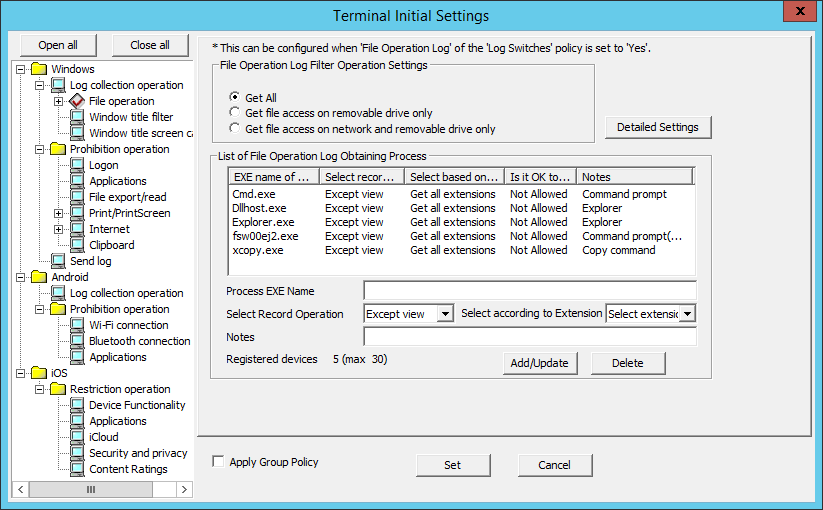
EXE Name of Process | Select Record Operation | Select based on extension | Is it OK to delete? | Notes |
|---|---|---|---|---|
Cmd.exe | Except view | Get all extensions | Not Allowed | Command Prompt |
Explorer.exe | Except view | Get all extensions | Not Allowed | Explorer |
fsw00ej2.exe | Except view | Get all extensions | Not Allowed | Command Prompt (DTK) |
xcopy.exe | Except view | Get all extensions | Not Allowed | Copy Command |
dllhost.exe | Except view | Get all extensions | Not Allowed | Explorer |
Item Name | Description | |
|---|---|---|
File Operation Log Filter Operation Settings | Select the drive type as the targets for collection of file and folder operation logs can be selected. | |
Get All | Record the operations of all drives. | |
Get file access on removable drives only.] | Record the operation for the drive, the drive type of which is removable disk. | |
Get file access on network and removable drive only | Record the operation for the drive, the drive type of which is network and removable disk. | |
Detailed Settings | The File Operation Process - Detailed Settings window will be displayed. (This item cannot be set if No is selected in Windows > Log collection operation > File Operation Log.) | |
Item Name | Description |
|---|---|
List of File Operation Log Obtaining Process | The processes and conditions during the obtaining of file operation logs are displayed in lists. |
Process EXE Name | Enter the EXE name of a process regarded as the target for the collection of file and folder operation logs. Up to 254 single-byte characters can be entered. In addition, ".com", ".exe", or ".bin" can be entered in the extension of a process. However, if double-byte characters or the following symbols are used, error will occur. Initial Value: Not Specified. |
Select Record Operation | Select the operation that is recorded as a log.
|
Select according to Extension | Select the extension of the file name that is recorded as a log.
* When operating the process (application of files or folders in the similar way as Explorer and Get all extensions is selected, a large amount of View logs will be collected. |
Notes | Enter the memo information of process name. |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. |
Add/Update | Add the entered information to the list. In addition, the changed information shall also be set. |
Delete | Delete the selected information of List of File Operation Log Obtaining Processes. |
When adding a process
Enter the above set items and click the Add/Update button.
Up to 30 cases of information can be registered including the number of processes that are preset in the system.
When updating the existing information
Select the lines to be updated from the List of File Operation Log Obtaining Processes, modify the following information and click the Add/Update button.
The EXE Name of Process cannot be updated. If the Can be Deleted or Not of a certain line is set to No, the Select Record Operation cannot be set to Get All.
Select Record Operation
Select according to Extension
Notes
When deleting information
Select the lines to be deleted from the List of File Operation Log Obtaining Processes, and click the Delete button.
But If the Is it OK to delete? of a certain line is set to No, the line cannot be deleted.
File Operation Process - Detailed Settings window
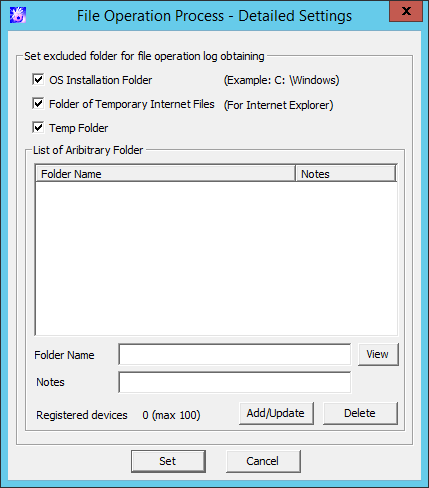
Item Name | Description | |
|---|---|---|
OS Installation Folder | Select this check box when accessing the files on the OS installation folder but when the file operation logs are not to be obtained. | |
Folder of Temporary Internet Files | Select this check box when accessing the files on the folder of Temporary Internet Files, but when the file operation logs are not to be obtained. | |
Temp Folder | Select this check box when accessing to the files on the following folders, but the file operation logs are not to be collected.
(Initial Value): Selected (*) | |
List of Arbitrary Folder | The fixed disk folder excluded from the acquisition of file operation logs can be set and deleted. | |
Folder Name | Specify the fixed disk folder excluded from the acquisition of file operation logs with full path. Specify up to 254 halfwidth (127 fullwidth) characters. Specify the folder by adding "\" or "/" after the drive's name + colon (:), When the drive specified in this window is the network drive or removable drive in the client (CT), it cannot become an excluded folder for obtaining file operation log. Example:
The same folder name cannot be registered more than once. "D:\aaa" and "D:\aaa\bbb" can be registered at the same time. The folder with an extension should be distinguished from the folder without extension. When "d:\data" is specified as the excluded folder, "d:\data.tmp" will not become the excluded folder. To make "d:\data.tmp" into the excluded folder, register "d:\data.tmp". Initial Value: Not Specified. | |
Notes | Enter the memo information, etc. | |
View | The folder structure of the PC with the Management Console installed can be viewed. | |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. | |
Add/Update | Add the folder excluding the acquisition of file operation log to the list. In addition, update the notes of the registered folder. The folder name cannot be updated. | |
Delete | Delete the folder excluding the acquisition of the file operation log from the list. | |
Set | Confirm the input content and return to the previous window. | |
Cancel | Do not save the set information and close the window. | |
*)When it is upgraded from the version earlier than Systemwalker Desktop Keeper V13.2.0, all the items are unselected.
For the file (extension) accessed by the process set in File operation, when the file operation log is collected, the extension can be set in Extension.
The items in Extension can be set when Yes is selected in Windows > Log collection operation > File Operation Log.
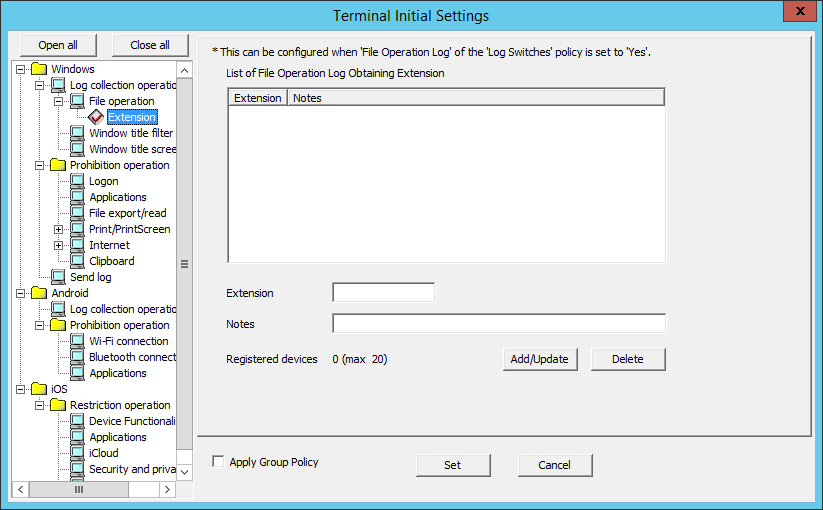
Item Name | Description |
|---|---|
List of File Operation Log Obtaining Extension | Display the extension of the registered and obtained file operation log. Initial Value: Not Specified. |
Extension | Enter the extension as the target for the collection of file and folder operation logs. The "." of extension is not required. (It cannot be entered.) Up to 16 single-byte characters (Alphabetic characters are not case-sensitive) can be entered. Only halfwidth alphanumeric characters, halfwidth symbols (except for the symbols mentioned below), and spaces can be entered (however, spaces cannot be specified at the beginning or the end). If the wildcard (*) is used, "*" should be put at the beginning or at the end of the extension.
The wildcard "*" cannot be entered in other locations. Initial Value: Not Specified. |
Notes | Enter the extension and memo information. |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. |
Add/Update | Add the entered information to the list. In addition, the modified information should be set. |
Delete | Delete the information selected in the List of File Operation Log Obtaining Processes. |
When adding an extension
Enter the above set items and click the Add/Update button.
Up to 20 cases can be registered.
When updating the existing information
Select the lines to be updated from List of File Operation Log Obtaining Extension, modify the Notes information and click the Add/Update button.
The Extension cannot be updated.
When deleting information
Select the lines to be deleted from List of File Operation Log Obtaining Extension, and click the Delete button.
The conditions for collecting the window title obtaining log can be set in Window title filter.
Though a large number of window title obtaining logs can be collected in order to record all operations on the PC, there will be many repeated logs. Therefore, to avoid collecting the repeated logs, the filtering condition should be set.
The log filtering condition involves two aspects, and two conditions can be specified at the same time.
Settings of Repeated Log Screening:
Only the first log will be collected for the same process and same window title.
Keyword Screening:
By specifying the process names and keywords, the window title logs including the specified process names and keywords can be collected or excluded.
Window title filter can be set when Yes is selected in Windows > Log collection operation > Window Title Obtaining Log(Web access log).
The following describes the settings in Window title filter.
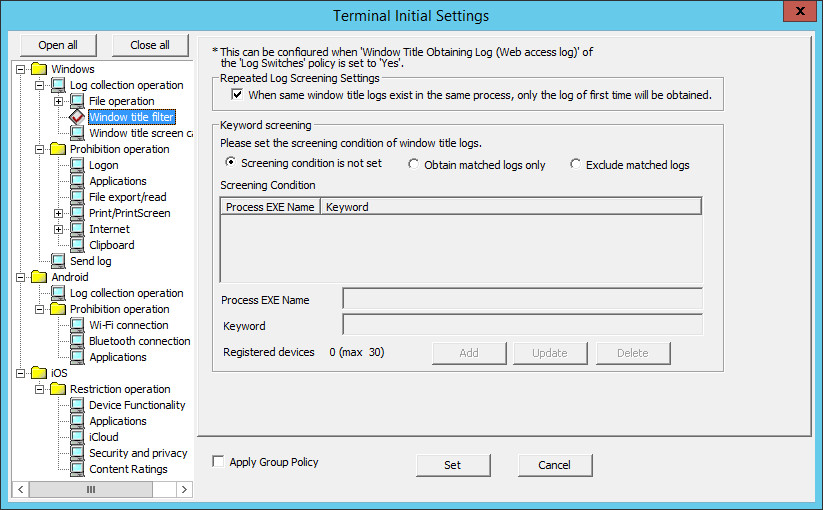
Item Name | Description |
|---|---|
Repeated Log Screening Settings | Select the method of obtaining repeated logs.
|
Item Name | Description |
|---|---|
Screening condition is not set (Initial Value) | The window title logs will not be screened according to process name and keyword. |
Obtain matched logs only | Only the logs belong to the specified process name and the window title log partially matches with the keyword specified in screening conditions will be collected. |
Exclude matched Logs | The logs belong to the specified process name, and the window title log that partially matches with the keyword specified in screening conditions will not be collected. |
Screening Condition | Display the set conditions in a list. |
Process EXE Name | Enter the EXE name of process that collects window title logs. Up to 254 single-byte characters (127 double-byte characters) can be entered. Spaces can only be used in-between characters. When it is not specified, logs of all processes will be collected (or excluded). Initial Value: Not Specified. |
Keyword | Enter the keyword for collecting window title obtaining logs. (When the window title includes(partially match)/does not include (partially match) the keyword specified here, window title logs will be collected.) Example:
Specify up to 254 bytes (can be a combination of fullwidth and halfwidth characters and symbols, kanji, hiragana and katakana characters). When Keyword is not specified, all window title obtaining logs of processes specified in Process EXE Name will be collected (will not be collected). Initial Value: Not Specified. |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. |
Add | Add conditions in Screening Conditions. |
Update | After modifying the information of lines selected in the Screening Condition, the information will be updated. |
Delete | Delete the lines selected in the Screening Condition. |
In Filtering Condition, when Process EXE Name and Keyword are specified at the same time, the AND condition is used.
When Process EXE Name and Keyword are specified separately in lines, the OR condition is used.
When adding a condition
Enter the above set items and click the Add button.
Up to 30 cases can be registered.
When updating the existing information
Select the lines to be updated from the Screening Condition, modify the information and click the Update button.
When deleting information
Select the lines to be deleted from the Screening Condition, and click the Delete button.
The condition of collecting the screen capture can be set in Window title screen capture.
Set conditions in this setting to capture the window title screen at the same time as the window title obtaining the log that matches the conditions set in Window title filter is collected.
Window title screen capture can be set when Yes is selected in Windows > Log collection operation > Window Title Obtaining Log(Web access log).
The settings related to screen capture can be performed in the Terminal Operation Settings window (Settings item: Attached data condition settings). Refer to "2.4.2 Perform Terminal Operation Settings" for details.
Note
Backup or delete the screen capture data regularly.
According to the screen capture condition, storing a large amount of screen capture data on the server (the client (CT) according to terminal operation settings) will cause insufficient disk capacity. Therefore, regularly confirm the capacity and backup and delete.
The following describes the settings in the Window title screen capture.
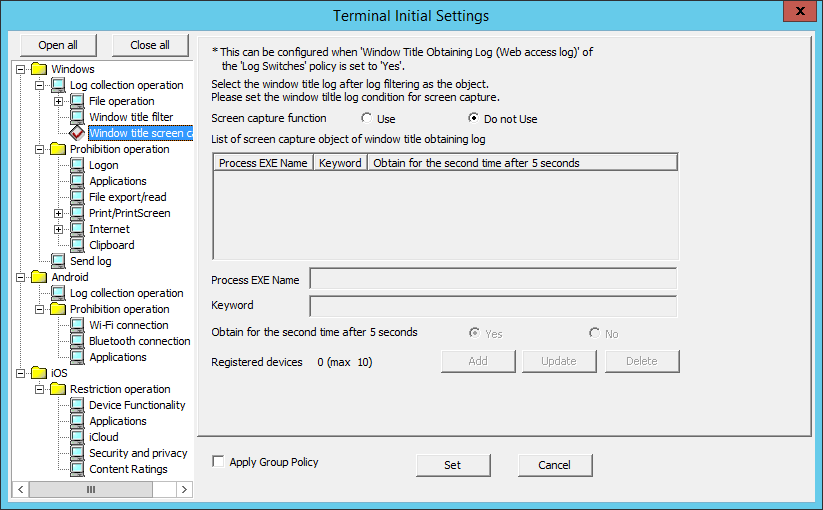
Item Name | Description |
|---|---|
Screen capture function | Select whether to obtain screen capture.
|
List of screen capture object of window title obtaining log | The conditions for obtaining screen capture are displayed in a list. Initial Value: Not Specified. |
Process EXE Name | Enter the EXE name of screen capture. Up to 254 single-byte characters (127 double-byte characters) can be entered. Alphabetic characters are not case-sensitive. ".com", ".exe", or ".bin" can be input in the process extension. Initial Value: Not Specified. |
Keyword | Enter the keyword for collecting screen capture. When the window title includes (partially match)/does not include (partially match) the keyword specified here, screen capture can be obtained.
Specify up to 254 bytes (can be a combination of fullwidth and halfwidth characters and symbols, kanji, hiragana and katakana characters). (Alphabetic characters are not case-sensitive) When the EXE name of process is entered in the EXE Name of Process, make sure to input in Keyword. Initial Value: Not Specified. |
Obtain for second time after 5 seconds | Set the second acquisition 5 seconds later after the screen capture has been obtained. When it is expected to obtain screen capture continuously to get further knowledge of operation status, select Yes.
When selecting Yes, the screen capture will be collected for the second time after 5 seconds. However, in the 5 seconds from the first collection to the second collection, even if a new window that satisfies the condition of screen capture collection exists, that screen capture will not be collected. As it is the second screen capture of the initial window, "2" which indicates two screen capture collections will be displayed in the Additional in the log list of Log Viewer. |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. |
Add | After selecting Use in the Screen Capture Function, the condition of screen capture collection will be added to the list. |
Update | After modifying the information of lines selected in the List of screen capture object of window title Log, the information will be updated. |
Delete | Delete the lines selected in the List of screen capture object of window title. |
In List of screen capture object of window title, when Process EXE Name and Keyword are specified at the same time, it is the AND condition.
When Process EXE Name and Keyword are specified separately in lines, the OR condition is used.
The settings in Window title screen capture and Window title filter are set using the AND condition. Therefore, even if the policy of obtaining screen capture is set, the log screening condition will be considered as not set when screen capture cannot be obtained.
When adding a condition
Enter the above settings items and click the Add button.
Maximum10 cases can be registered.
When updating the existing information
Select the lines to be updated from the List of screen capture object of window title, modify the information and click the Update button.
When deleting information
Select the lines to be deleted from the List of screen capture object of window title, and click the Delete button.
The group prohibited from logon can be set in Logon. After setting the Logon Prohibition, logon with the user name that belongs to the set group can be prohibited when logging on to the PC with the client (CT) installed.
The groups for which logon prohibition can be set are as follows:
Microsoft account
In addition, when one user name belongs to multiple groups, it will become a target of logon prohibition when it satisfies all the following conditions:
The user name entered during logon to the Windows PC belongs to multiple groups.
Logon prohibition is set for any one group in the multiple groups to which the user name belongs.
The set contents will be operated as CT policy.
When only one person logs on to the PC, prohibition can be performed through the settings in Logon.
When 2 or more users log on to the same PC, it will have nothing to do with the settings in Logon and it will be logged off.
The following section describes the settings of Logon.
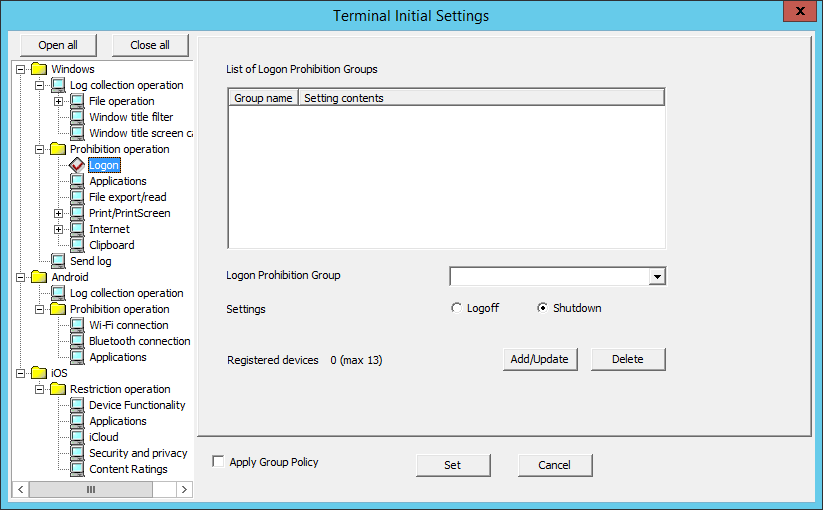
Item Name | Description |
|---|---|
List of Logon Prohibition Groups | The set logon prohibition group will be displayed. |
Logon Prohibition Group | Select the logon prohibition group from the pull-down menu. |
Settings | When prohibiting the target group from logon, the processing in the client (CT) can be specified.
The time from logon prohibition being detected from the client (CT) to logoff or shutdown can be set in the "Terminal Operation Settings". Refer to "2.4.2 Perform Terminal Operation Settings" for "Terminal Operation Settings". |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. |
Add/Update | The name of group that is prohibited from logon and the processing during logon will be added. After modifying the Set of selected lines in the List of Logon Prohibition Groups, the information will be updated (The Logon Prohibition Group cannot be updated.). |
Delete | The selected lines in the List of Logon Prohibition Groups will be deleted. |
When adding a logon prohibition group
After entering the above set items, click the Add/Update button.
When updating the existing information
Select the lines to be updated from the List of Logon Prohibition Groups, modify the Settings information and click the Add/Update button.
The Group Name cannot be updated.
When deleting information
Select the lines to be deleted from the List of Logon Prohibition Groups and click the Delete button.
In Application, the name of the application that is prohibited from startup in the PC with the client (CT) installed can be set.
The following section describes the settings of Application.
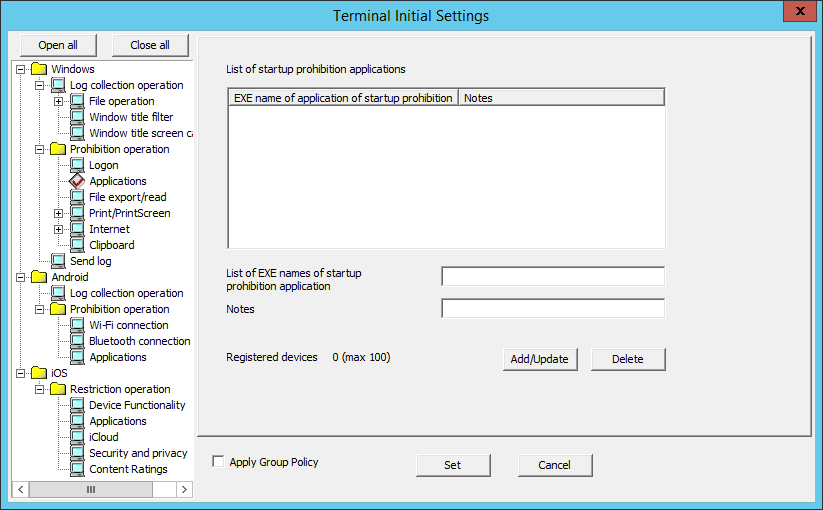
Item Name | Description |
|---|---|
List of startup prohibition applications | The set EXE name of the application prohibited from startup will be displayed. |
EXE name of application of startup prohibition | Enter the EXE name including extension of the application prohibited from startup. Up to 254 single-byte characters (127 double-byte characters) can be entered. (Alphabetic characters are not case-sensitive) However, error will occur if the following symbols are used. Initial Value: Not specified. |
Notes | Enter the application name and memo information. |
Refistered devices | The number of registered cases and the maximum number of registrations possible are displayed. |
Add/Update | The EXE name of the application prohibited from startup will be added. After modifying the Notes of the selected lines in the List of Applications Prohibited from Startup, the information will be updated (The EXE Name of Application Prohibited from Startup cannot be updated.). |
Delete | The lines selected in the List of applications of startup prohibited will be deleted. |
When adding an EXE name of the application prohibited from startup
Enter the above set items and click the Add/Update button.
Up to 100 cases can be added.
When updating the existing information
Select the lines to be updated from the List of applications of startup prohibited, modify the Notes information and click the Add/Update button.
The EXE Name of application of startup prohibited cannot be updated.
When deleting information
Select the lines to be deleted from the List of applications of startup prohibited , and click the Delete button.
In File export/read, the conditions of prohibiting the export and reading of files or folders from disk drive, removable device, DVD/CD drive or network drive of the client (CT) PC will be set.
Though the reading prohibition is effective when the Explorer is used, it will become invalid while the File Export Utility is being used.
In addition, the limiting conditions for export to the allowed USB device will be set by the administrator.
The following section describes the settings of File export/read.
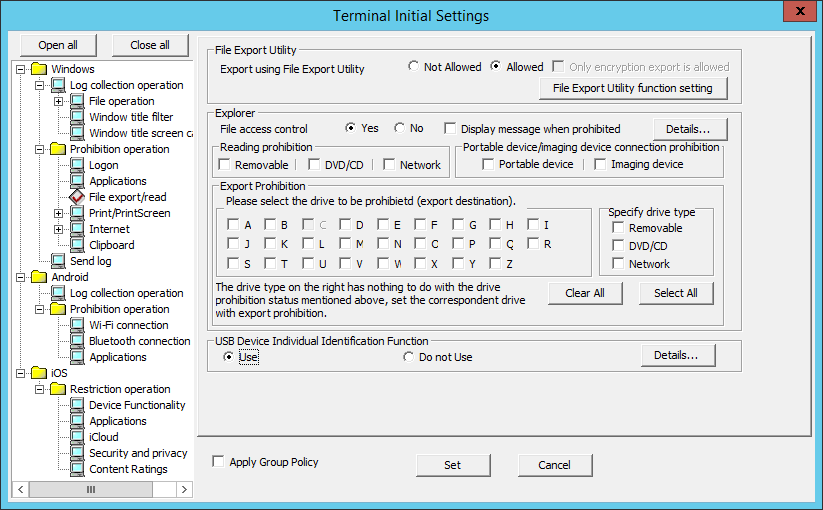
Item Name | Description | |
|---|---|---|
Export using File Export Utility | Not Allowed (Initial Value) | The File Export Utility cannot be used. |
Allowed | The File Export Utility can be used. | |
File Export Utility function setting | The Setting of File Export Utility function is displayed. | |
Set the control when operation is performed via Explorer etc.
Item Name | Description | ||||
|---|---|---|---|---|---|
File access control | Yes | Reading Prohibition and Export Prohibition can be set. The Display message when prohibition check box can be selected when this item is selected. After it is selected, messages will be displayed when the prohibition operation is performed. | |||
No | Reading of removable drive and export of files can be performed freely. Files can be accessed in the same way as if Systemwalker Desktop Keeper is not installed. | ||||
Display message when prohibited | After setting this item, the following message will be displayed when inserting the prohibited device into the client (CT). [S105-ERR001]Accessing to this drive is prohibited by system administrator. (Drive: G) The above message is output when a violation regarding an added drive is recorded in the device configuration change log. [S105-ERR002]Accessing to this drive is prohibited by system administrator. (Drive: Y-E DATA USB-FDU USB Device) The above message is output when Violation regarding an added USB device is recorded in the device configuration change log for USB devices. Initial Value: Not selected Refer to "8.2.6 Device Configuration Change Log" for "Violation" of device configuration change log. | ||||
Detailes | Settings can be performed when the File Access Control is "Yes". | ||||
Reading Prohibition | Set the targets for reading prohibition. | ||||
Removable | Reading of the following devices that are identified as drive letter are prohibited.
Compact flash memory | ||||
DVD/CD | Reading of DVD/CD is prohibited. Initial Value: Not selected | ||||
Network | Reading of network drive is prohibited. Initial Value: Not selected | ||||
Portable device/imaging device connection prohibition | Prohibits connection of portable devices and imaging devices. | ||||
Portable device | Prohibits connection of portable devices. Default value: Not selected. | ||||
Imaging device | Prohibits connection of imaging devices. Default value: Not selected. | ||||
Export Prohibition | Set the targets for exporting prohibition. | ||||
Please select the drive to be prohibited(export destination). | Select the drive that is the target for export prohibition. The drive that becomes the prohibited target by specifying the drive letter should satisfy all the following conditions.
When F drive is a removable drive, even if the Removable (not regarded as the prohibited target) is not selected, when F (regarded as prohibited target) is selected, F drive will also be prohibited. Note About network drive The network drive cannot be prohibited by specifying the drive letter. Prohibit it by selecting the Network check box. | ||||
Specify drive type | Removable | Export to the following devices that are identified as drive letter is prohibited.
| |||
DVD/CD | Export to DVD/CD is prohibited. | ||||
Network | Export to network drive is prohibited. Initial Value: Not selected | ||||
Clear All | Clear all the selections for the settings of the prohibited drive (export destination) and Specify drive type. | ||||
Select All | Select all for the settings of the prohibited drive (export destination) and Specify drive type. | ||||
Note
Do not set the target drive for saving log files.
If the target drive for saving log files set during the installation of the client (CT) is regarded as the prohibited target, logs cannot be collected from the client (CT).
Item Name | Description |
|---|---|
Use | When exporting files and folders using File Export Utility, they can only be exported to the USB device specified by the administrator among the USB devices registered in the USB Device Registration window of the Management Control. |
Do not Use | When exporting files and folders using File Export Utility, follow the policies set in File Export Utility. |
Detailes | The File Export Prohibition - USB Device Individual Identification Function - Detailed Settings window will be displayed. |
File Export Utility function setting window
The conditions of using File Export Utility can be set.
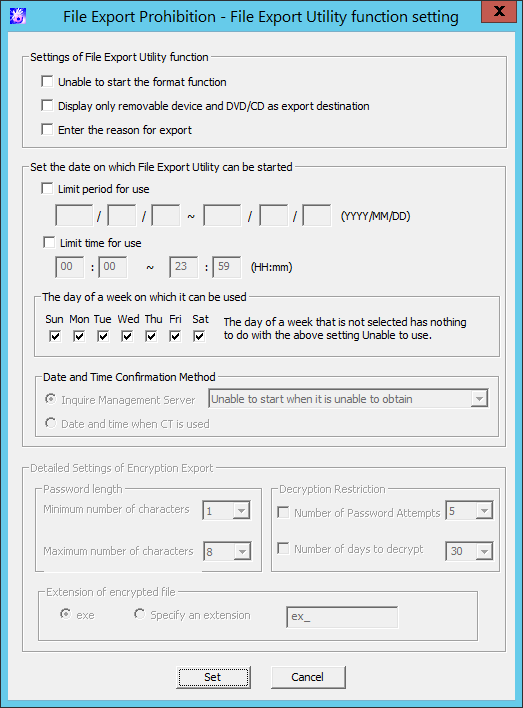
Item Name | Description |
|---|---|
Unable to start the format function | When this is selected:
When it is not selected: (Initial Value) |
Display only removable device and DVD/CD as export destination | When this is selected: When it is not selected: (Initial Value) |
Enter the reason for export | When this is selected: When it is not selected: (Initial Value) |
Item Name | Description | |
|---|---|---|
Limit period for use | When this is selected:
When it is not selected: (Initial Value): | |
Limit time for use | When this is selected: When it is not selected: (Initial Value): | |
The day of a week on which it can be used | The day in a week when the startup is allowed will be set. | |
Date and Time Confirmation Method | Inquire Management Server | The date and time when the File Export Utility can be started is based on the date and time of the Management Server. In addition, set the operations when the client is offline or the Management Server gives no response.
|
Date and Time when CT is used | The date and time when the File Export Utility can be started is based on the date and time of the CT. | |
File access control - Detailed Settings window
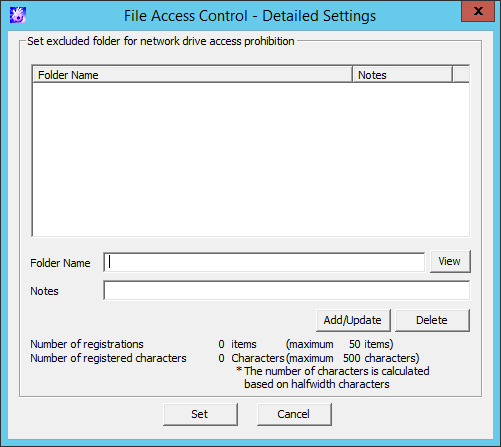
Item Name | Description | |
|---|---|---|
Set excluded folder for network drive access prohibition | The folder excluded from network drive access prohibition can be set. | |
Folder Name | The folder excluded from network drive access prohibition can be set. In addition, "\" cannot be specified at the end of path. Initial Value: No specification Refer to "1.2.45 IPv6 Support" for details on specifying an IPv6 address. | |
View | The dialog for selecting the excluded folder can be displayed. | |
Notes | Enter the information such as memo. | |
Number of registrations | The number of registered cases displayed in the list and the maximum number of registrations possible are displayed. A maximum of 50 cases can be registered. | |
Number of registered characters | The number of characters that can be used for the folder name is limited to a maximum of 500 halfwidth (250 fullwidth) characters. The number of characters used for the registered folder names is converted to halfwidth characters and displayed. | |
Add/Update | Add an excluded folder. After modifying the selected Notes in the folder list, the information will updated (Folder Name cannot be updated). | |
Delete | Delete the selected lines in the folder list. | |
Set | Confirm the input contents and return to the previous window. | |
Cancel | Do not save the settings and close the window. | |
File Export Prohibition - USB Device Individual Identification Function - Detailed Settings window
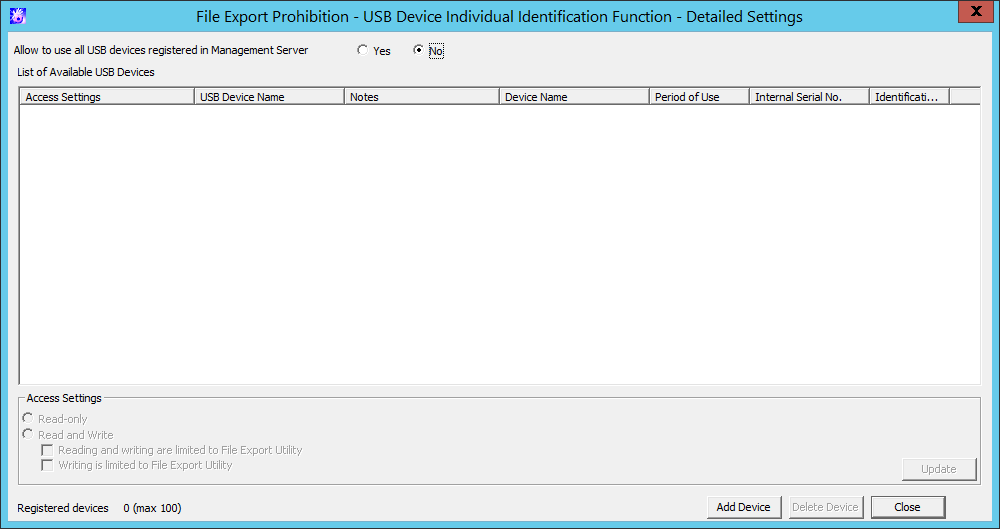
Item Name | Description | ||
|---|---|---|---|
Allow to use all USB devices registered in Management Server | Select whether the used of all USB devices registered in the Management Server is allowed. Yes: No: (Initial Value) | ||
List of Available USB Devices | The USB device that is allowed to be used by the administrator will be displayed. | ||
Access Settings | Set the conditions for accessing to the USB device allowed to be used. | ||
Read Only | The selected USB device in List of Available USB Devices can be read only. | ||
Read and Write | The selected USB device in List of Available USB Devices can be read and written. Only one can be selected among the Reading and writing are limited to File Export Utility check box and the Writing is limited to File Export Utility check box. | ||
Reading and writing are limited to File Export Utility | When it is selected: | ||
Writing is limited to File Export Utility | When it is selected: | ||
Update | The settings can be displayed in List of Available USB Devices. | ||
Registrered devices | The number of registered cases and the maximum number of registrations possible are displayed. | ||
Add Device | The File Export Prohibition - Detailed Settings of USB Device Individual Identification Function - Select USB device window can be displayed and the available USB devices can be added. | ||
Delete Device | The usage permission of the selected USB device can be canceled in List of Available USB Devices and the USB device can be deleted from List of Available USB Devices. | ||
Close | Shutdown the window. | ||
Select the line corresponding to the USB device in List of Available USB Devices.
Set conditions in Access Settings.
Click the Update button.
Select the line corresponding to the USB device in List of Available USB Devices.
Click the Delete Device button.
Click the Add Device button.
File Export Prohibition - Detailed Settings of USB Device Individual Identification Function - Select USB device window
The content registered in the USB Device Registration window of the Management Console can be displayed.
The line of the available USB device can be selected. After clicking the OK button, the corresponding USB Device will be added to the List of Available USB Devices in the File Export Prohibition - USB Device Individual Identification Function - Detailed Settings window.
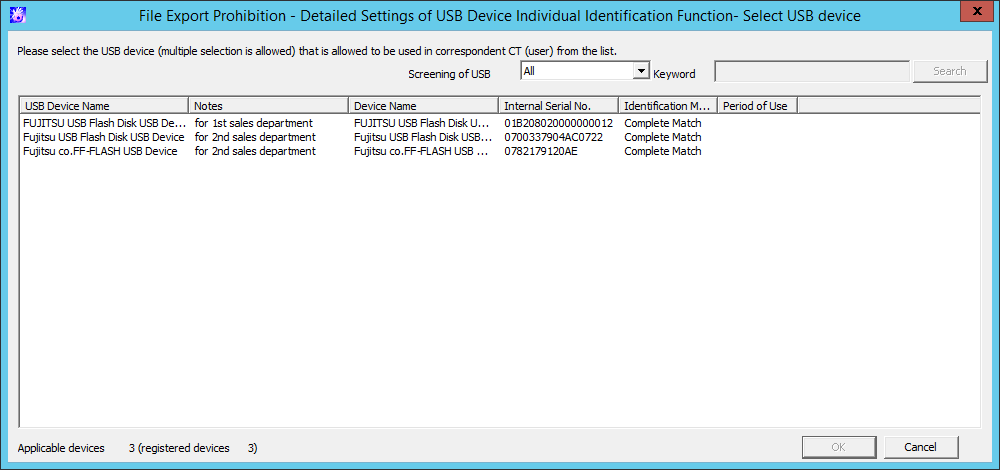
Item name | Description |
|---|---|
Screening of USB | The USB devices to be displayed in List of USB Devices can be filtered. Select from the following:
Notes |
Keyword | Specifies the search conditions for the USB devices to be displayed. Specify up to 128 halfwidth and fullwidth characters. |
Search | Performs USB device search using the conditions specified in Screening of USB Device and Keyword. |
Note
Depending on the type of portable device/imaging device, the communication mode may be automatically set during connection to the PC, or you may be able to select it from the menu. Either of the following connections will be established but the configured Access Settings may not be enabled depending on the communication mode.
Recognition method | Access behavior |
|---|---|
Drive letter assigned | Normally, the drive type for portable devices/imaging devices is recognized as Removable, and the device behaves according to Read-only or Read and Write set in the access settings configured in the Detailed Settings window. |
Drive letter not assigned | If connection is allowed, the device will behave according to Read and Write irrespective of the access settings. |
If dedicated software provided by the device manufacturer is used for communication, read prohibition may not be enabled.
The conditions for prohibiting printing on the PC with the client (CT) installed (specify the application allowed to print) and the prohibition of using PrintScreen key to collect screen hard copy can be set in Print/PrintScreen.
The following section describes the settings of Print/PrintScreen.
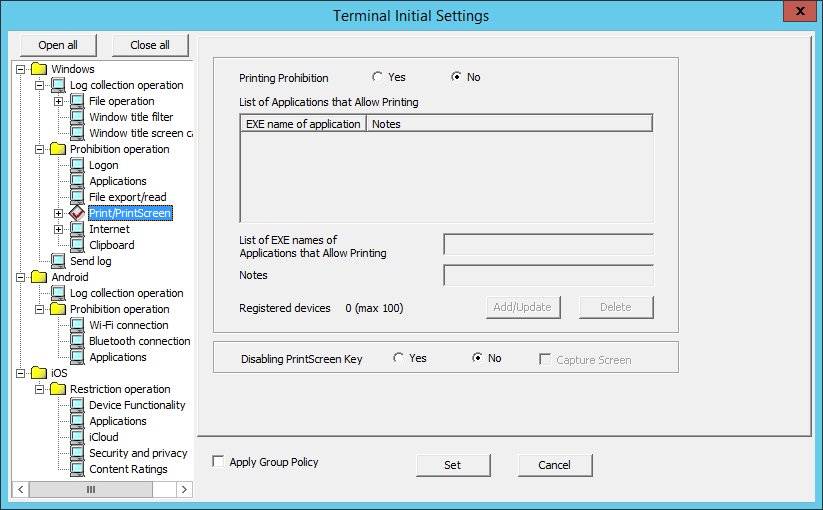
Item Name | Description | |
|---|---|---|
Printing Prohibition | Yes | Printing that uses applications apart from the EXE Name of application displayed in the List of Applications that Allow Printing is prohibited. |
No | Printing is not prohibited. | |
List of Applications that Allow Printing | The set EXE Name of Application that Allow Printing will be displayed. | |
List of EXE names of Applications that Allow Printing | Enter the EXE names including the extensions of Applications allowed to print. Up to 254 single-byte characters (127 double-byte characters) can be entered. (Alphabetic characters are not case-sensitive.) However, if the following symbols are used, error will occur. Initial Value: No specification will be made. | |
Notes | Enter the application name and memo information. | |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. | |
Add/Update | Add the EXE name of application allowed to print. After modifying the Notes of selected lines in the List of Applications Allowed to Print, the information will be updated. The EXE Name of Application that Allow Printing cannot be updated. | |
Delete | The selected lines in the List of Applications that Allow Printing can be deleted. | |
Item Name | Description | |
|---|---|---|
Disabling PrintScreen Key | When the PrintScreen Key Operation Log option in Windows > Log collection operation is No, settings can be performed. | |
Yes | The use of PrintScreen key is prohibited. | |
No | The use of PrintScreen key is not prohibited. | |
Capture Screen | When the option of PrintScreen Key Prohibition is "Yes", settings can be performed When it is selected: When it is not selected: | |
[When adding the EXE name of applications that Allow Printing ]
Enter the above settings items and click the Add/Update button.
Up to 100 cases can be added.
[When updating the existing information]
Select the lines to be updated from the List of Applications that Allow Printing, modify the Notes information and click the Add/Update button.
The EXE Name of Application that Allow Printing cannot be updated.
[When deleting information]
Select the lines to be deleted from the List of Applications that Allow Printing, and click the Delete button.
By monitoring the printed pages, the conditions can be set in Eco monitoring to reduce unnecessary printing.
In the Settings of Printing Monitoring Mode during the installation of CT, this function is effective when Monitor the printing of all printers set in the terminal (Recommended) is selected.
When Yes is selected in Printing Operation log of Windows > Log collection operation, the monitoring condition can be set.
When the set number of pages is reached and the printing is prohibited, a warning message will be displayed to the user of the client (CT), and the printing can be prohibited. At the same time, it will be recorded as a violation to the printing prohibition log.
The settings of Eco monitoring will be processed as CT policy.
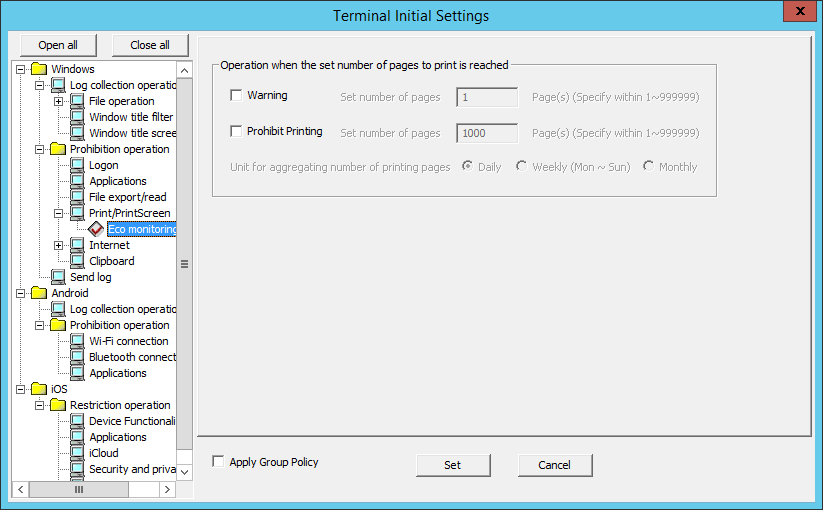
Item Name | Instruction | |
|---|---|---|
Warning (*) |
| |
Prohibit Printing(*) |
| |
Unit for aggregating number of printed pages | Daily | Monitor the number of printed pages in 24 hours. |
Weekly(Mon~Sun) | Monitor the number of printed pages in a week. | |
Month | Monitor the number of printed pages in a month | |
*) When both Warning and Prohibit Printing are selected,
input the set number of pages in Warning =< the set number of pages in Prohibit Printing.
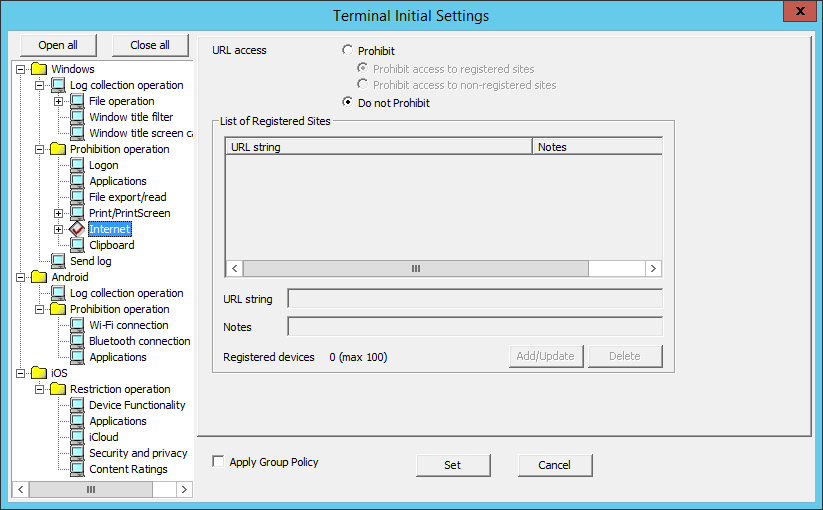
The URL prohibited from being accessed can be set in Internet.
Item Name | Description | ||
|---|---|---|---|
URL access | Prohibit | Access to URL is prohibited. | |
Prohibit access to registered sites | Access to the URL specified in List of Registered Sites is prohibited. | ||
Prohibit access to non-registered sites | Access to the URL other than the one specified in the List of Registered Sites is prohibited. | ||
Do not Prohibit | Any URL can be accessed. | ||
List of Registered Sites | The URL that is prohibited or allowed to be accessed and the memo related to the URL will be displayed. | ||
URL string | Enter the character string that contains part of the domain name of the prohibited or allowed to be accessed URL. [Example 2] If "10.10.10.10" is prohibited in the settings in URL string, the following will be prohibited. Up to 254 single-byte alphanumeric characters and symbols can be entered (Alphabetic characters are not case-sensitive) Halfwidth katakana, control characters, and spaces cannot be specified. A multi-byte character domain name cannot be used. Up to 100 cases can be registered. Refer to "1.2.45 IPv6 Support" for details on IPv6 addresses. Initial Value: Not Specified. | ||
Notes | Enter the information such as the memo of URL. | ||
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. | ||
Add/Update | URL will be added. After modifying Notes the lines selected in List of Registered Sites, the information can be updated (The URL string cannot be updated.) | ||
Delete | The lines selected in List of Registered Sites will be deleted. | ||
The Web upload and download operations permitted by the administrator can be set in Web upload/download.
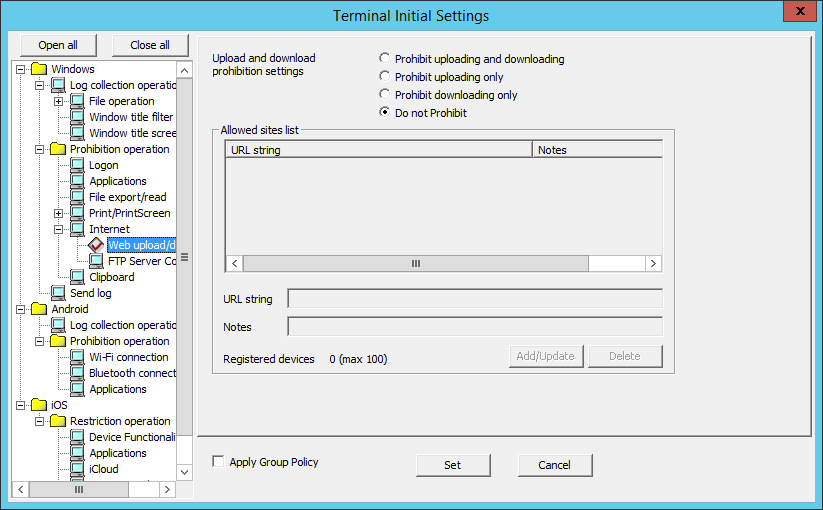
Item Name | Description | |
|---|---|---|
Upload and download prohibition settings | Prohibit uploading and downloading |
Prohibits uploading and downloading from websites other than those specified in Allowed sites list.
Prohibits downloading from websites other than those specified in Allowed sites list. Uploading will not be prohibited for any website.
Neither uploading nor downloading will be prohibited for any website. |
Prohibit uploading only |
Prohibits uploading from websites other than those specified in Allowed sites list. Downloading will not be prohibited for any website.
Prohibits uploading and downloading from websites other than those specified in Allowed sites list.
Prohibits downloading from websites other than those specified in Allowed sites list. Uploading will not be prohibited for any website.
Neither uploading nor downloading will be prohibited for any website. | |
Prohibit downloading only |
Prohibits downloading from websites other than those specified in Allowed sites list. Uploading will not be prohibited for any website.
Prohibits uploading and downloading from websites other than those specified in Allowed sites list.
Prohibits downloading from websites other than those specified in Allowed sites list. Uploading will not be prohibited for any website.
Neither uploading nor downloading will be prohibited for any website. | |
Do not Prohibit | Uploading and downloading from any website are allowed. | |
Allowed sites list | URLs of the websites for which uploading and downloading are allowed, and notes about these URLs are displayed. Up to 100 URLs can be registered. Default value: No value is displayed. | |
URL string | Enter the URL of the Web site that allows upload and download. Example 2: If "10.10.10.10" is specified in URL string, the following will be allowed. The following will be prohibited if the IP address for jp.fujitsu.com is "10.10.10.10": http://jp.fujitsu.com (Not allowed) Example 3: If "/desktopkeeper" is specified in URL string, the following will be allowed. http://jp.fujitsu.com (Not allowed) Up to 254 single-byte alphanumeric characters and symbols can be entered. (Alphabetic characters are not case-sensitive) A multi-byte character domain name cannot be used. Up to 100 cases can be registered. To specify an IPv6 address, enclose the address in []. Example: http://[2001:db8::1] To set the path part only, "/" must be specified at the beginning. Example: /desktopkeeper Initial Value: Not Specified. | |
Notes | Enter the memo information of the URL that allows upload and download. | |
Registered devices | The number of registered cases and the maximum number of registrations are displayed. | |
Add/Update | The URL of the Web site that allows upload and download will be added. After modifying the Notes information of lines selected in the List of sites allow uploading and downloading, the information can be updated (The URL Character String cannot be updated.). | |
Delete | The lines selected in the List of sites allow uploading and downloading will be deleted. | |
Note
Client (CT) for V14.1.0 and V14.2.0 when the path part is included in the URLs set for the allowed sites
In V14.3.0 or later (Master) Management Server/Management Console, the path part can be included in the URLs set for the allowed sites. (Example: jp.fujitsu.com/solutions)
If operation is performed with a policy in which the path part is included in the URLs set for the allowed sites. However, uploading and downloading to and from the allowed sites will not be allowed on the client (CT) for V14.1.0 and V14.2.0. In this case, specify the host name part of the URL ("jp.fujitsu.com" in "jp.fujitsu.com/solutions") as the URL of the allowed site.
Example:
Upload and download prohibition settings: Settings other than Do not Prohibit
URL of the allowed site set: jp.fujitsu.com/solutions
If the URL of the website accessed is "http://jp.fujitsu.com/download.html"
Client (CT) for V14.3.0 or later: Would determine that it is not an allowed site.
Client (CT) for V14.1.0 and V14.2.0: Would determine that it is not an allowed site.
If the URL of the website accessed is "http://jp.fujitsu.com/solutions/download.html"
Client (CT) for V14.3.0 or later: Would determine that it is an allowed site.
Client (CT) for V14.1.0 and V14.2.0: Would determine that it is not an allowed site.
Prohibition of the connection to the FTP server which is not permitted by the administrator can be set in FTP Server Connection.
To prohibit the connection to FTP server from Internet Explorer(R), set in Internet.
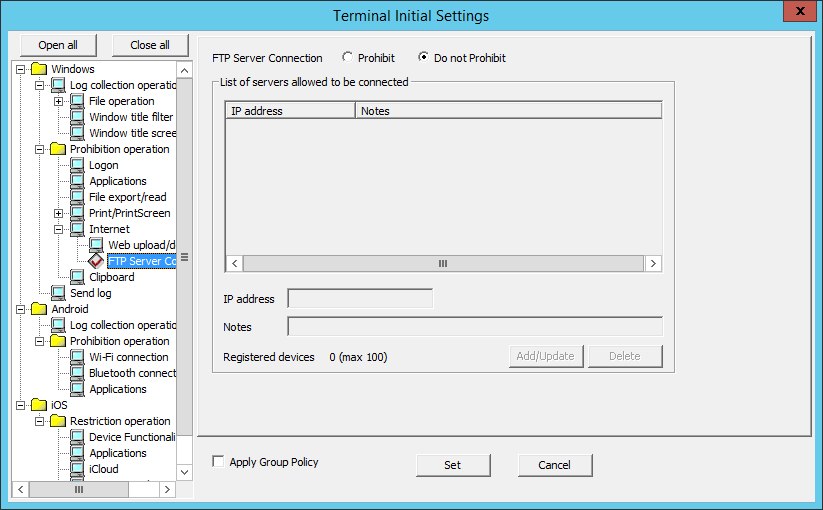
Item Name | Description | |
|---|---|---|
FTP Server Connection | Prohibit | Prohibit the access to the servers that is not specified in the List of servers allowed be connected. |
Do not Prohibit | Any FTP server can be connected. | |
List of servers allowed to be connected | The IP address of FTP server allowed to be connected and the memo related to the server to be connected are displayed. | |
IP address | Enter the IP address (IPv4/IPv6 format) of the server to be connected. Refer to "1.2.45 IPv6 Support" for details on registration with IPv6 addresses. | |
Notes | Enter the memo information of the server allowed to be connected, etc. | |
Number of registrations | The number of registered cases and the maximum number of registrations possible are displayed. | |
Add/Update | The server allowed to be connected will be added. After modifying the Notes of lines selected in the List of servers allowed to be connected, the information will be updated (The IP Address and Connecting Target port cannot be updated.) | |
Delete | The lines selected in List of servers allowed to be connected will be deleted. | |
The clipboard operation prohibition can be set in Clipboard.
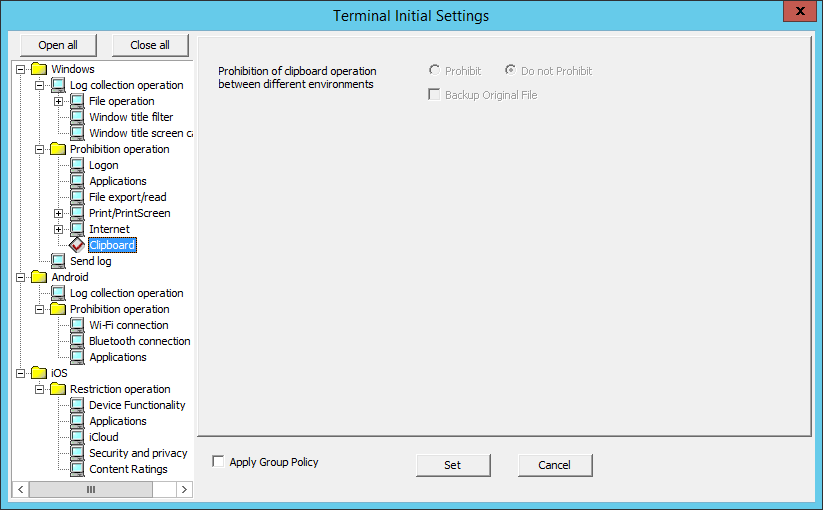
Item Name | Description | |
|---|---|---|
Prohibition of clipboard operation between different environments | When the Clipboard Operation Log (Virtual Environment) option in Windows > Log collection operation is No, settings can be performed. | |
Prohibit | The clipboard operation is prohibited. | |
Do not Prohibit | The clipboard can be used to copy from the virtual environment to the physical environment or from the physical environment to the virtual environment. | |
Backup Original File | When the option of Prohibition of clipboard operation between different environments is Prohibit, the item can be set. When this is selected: When this is not selected: (Initial Value) | |
The method of sending operation logs from the client (CT) to the Management Server can be set in Send log. The sent logs are operation logs, prohibition logs and attached data.
Note
About sending command operation log to the server
Command logs are always sent immediately after collection (not affected by this setting).
The method of sending can be set according to the following cases:
When the client (CT) is always connected to the server and network
When connecting to the server, the logs accumulated in the client (CT) due to the reasons such as a mobile application will be sent immediately.
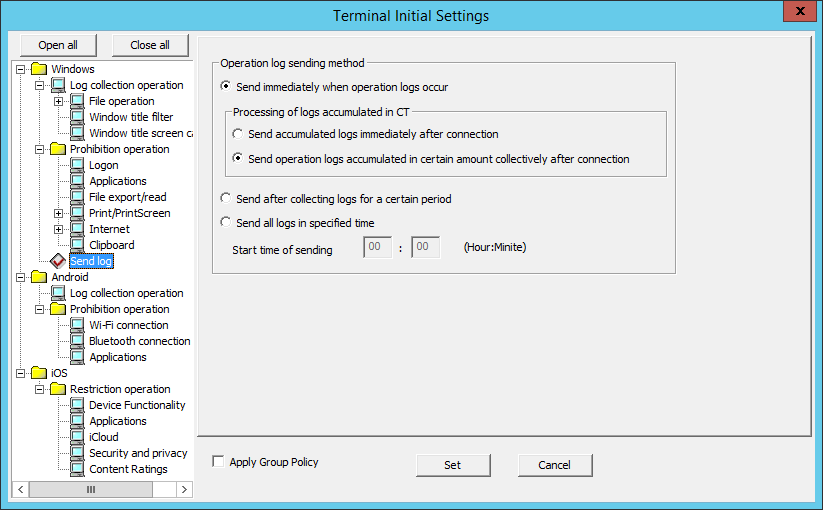
Item Name | Description | ||
|---|---|---|---|
Send immediately when operation logs occur | Logs will be sent to the server immediately when they are generated. | ||
Processing of logs accumulated in CT | Set the method of sending the logs accumulated in the client (CT) due to reasons such as a mobile application immediately when the network connects to the server. | ||
Send accumulated logs immediately after connection | If operation logs are generated, they will be accumulated at the time, and sent to the server every 10 seconds. | ||
Send operation logs accumulated in certain amount collectively after connection | If operation logs are generated, they will be accumulated at the time, and then sent to the server in a regular interval. Accumulated violation logs are sent every 0.5 seconds per log. | ||
Send after collectiong logs for a certain period | The same behavior as when Send immediately when operation logs occur > Send operation logs accumulated in certain amount collectively after connection is selected. | ||
Send all logs in specified time | Send logs to server in the specified time. The standards are as follows. The number of clients (CT number of sets) and amount of logs are basically in proportion to the time required for log sending. Example 1
Example 2
The number of logs to be sent at one time and the interval for sending are set in the Terminal Operation Settings window. Refer to "2.4.2 Perform Terminal Operation Settings" for details. | ||
In Android > Log collection operation, specify whether to collect each log type. Select Yes, and the operation logs for the smart device (agent) will be collected.
The following describes the settings configured in Android > Log collection operation.
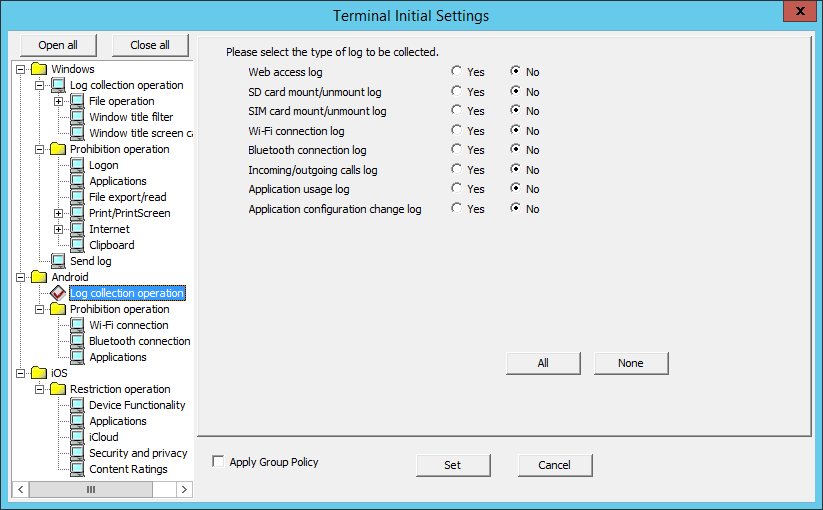
Item name | Description |
|---|---|
Web access log | Logs accessed from standard browsers will be collected. |
SD card mount/unmount log | SD card mount/unmount logs will be collected. |
SIM card mount/unmount log | SIM card mount/unmount logs will be collected. |
Wi-Fi connection log | Wi-Fi connection/disconnection logs will be collected. |
Bluetooth connection log | Bluetooth connection/disconnection logs will be collected. Default value: No is selected. |
Incoming/outgoing calls log | Phone numbers will be collected from the phone call history, and if the numbers are registered in the phonebook, then the names of those associated with the numbers will also be collected. Default value: No is selected. |
Application usage log | Logs for applications used will be collected. Default value: No is selected. |
Application configuration change log | Application configuration change (install/uninstall) logs will be collected. Default value: No is selected. |
In Wi-Fi connection, specify the BSSID for the access point to prohibit Wi-Fi use.
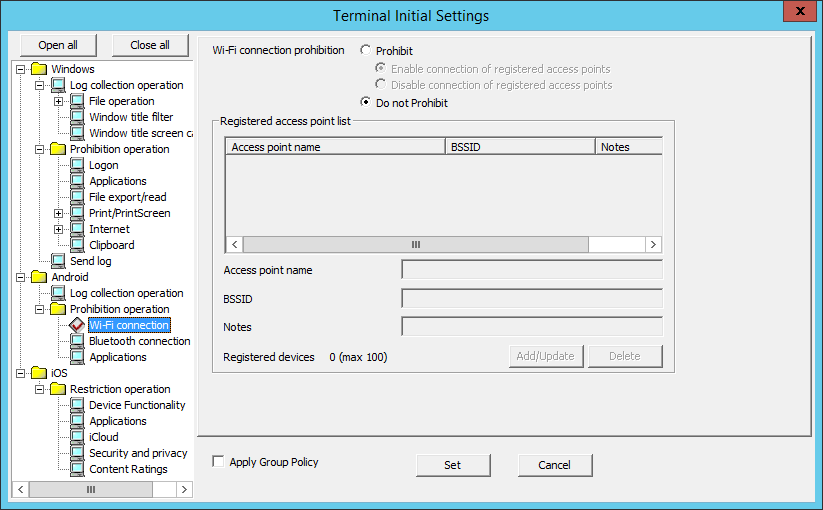
Item name | Description | ||
|---|---|---|---|
Wi-Fi connection prohibition | Prohibit | Prohibits connection to the access points specified in Registered access point list. | |
Enable connection of registered access points | Enables connection to the access points specified in Registered access point list. | ||
Disable connection of registered access points | Disables connection to the access points specified in Registered access point list. | ||
Do not Prohibit | Connection to any access point is possible. | ||
Registered access point list | Displays the access point name, BSSID, and notes for the access points to which connection will be enabled or disabled. | ||
Access point name | Enter the access point name. Specify up to 254 halfwidth (127 fullwidth) characters. Up to 100 names can be registered. Default value: No value is displayed. | ||
BSSID | Enter the access point Basic Service Set Identifier (BSSID). The characters that can be entered comply with the BSSID convention. Enter the BSSID in the "XX:XX:XX:XX:XX:XX" or "XX-XX-XX-XX-XX-XX" format. ("X" denotes a halfwidth alphanumeric character while ":" and "-" denote halfwidth colon and halfwidth hyphen respectively.) (Example: 02:E0:32:33:A3:C0) Default value: No value is displayed. | ||
Notes | Enter information such as notes on the access points to which connection is allowed. Specify up to 128 halfwidth (64 fullwidth) characters. Default value: No value is specified. | ||
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. | ||
Add/Update | Adds access points to which connection will be allowed. Information will be updated when Access point name and Notes for the row selected in Registered access point list are changed. A new access point will be added when BSSID is changed. | ||
Delete | Deletes the row selected in Registered access point list. | ||
In Bluetooth connection, set the MAC address for Bluetooth devices on which Bluetooth use will be prohibited.
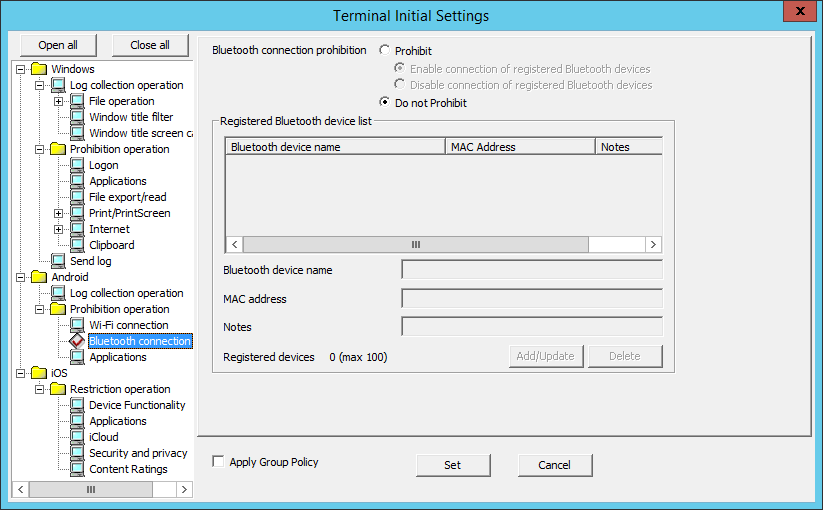
Item name | Description | ||
|---|---|---|---|
Bluetooth connection prohibition | Prohibit | Prohibits connection to the Bluetooth devices specified in Registered Bluetooth device list. | |
Enable connection of registered Bluetooth devices | Enables connection to the Bluetooth devices specified in Registered Bluetooth device list. | ||
Disable connection of registered Bluetooth devices | Disables connection to the Bluetooth devices specified in Registered Bluetooth device list. | ||
Do not Prohibit | Connection to any Bluetooth device is possible. | ||
Registered Bluetooth device list | Displays the Bluetooth device name, MAC address, and notes for the Bluetooth devices to which connection will be enabled or disabled. | ||
Bluetooth device name | Enter the Bluetooth device name. Control characters cannot be specified. | ||
MAC address | Enter the MAC addresses for uniquely identifying Bluetooth devices. The characters that can be entered comply with the MAC address convention. Enter the MAC address in the "XX:XX:XX:XX:XX:XX" or "XX-XX-XX-XX-XX-XX" format. ("X" denotes a halfwidth alphanumeric character while ":" and "-" denote halfwidth colon and halfwidth hyphen respectively.) (Example: 02:E0:32:33:A3:C0) Default value: No value is displayed. | ||
Notes | Enter information such as notes on the Bluetooth devices registered. Specify up to 128 halfwidth (64 fullwidth) characters. Default value: No value is specified. | ||
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. | ||
Add/Update | Adds Bluetooth devices to which connection will be allowed. Information will be updated when Bluetooth device name and Notes for the row selected in Registered Bluetooth device list are changed. A new Bluetooth device will be added when MAC address is changed. | ||
Delete | Deletes the row selected in Registered Bluetooth device list. | ||
In Android > Application, set the package name for prohibited applications.
You can also set whether to prohibit use of specified applications outside business hours only, and whether to delete application data outside business hours, and so on.
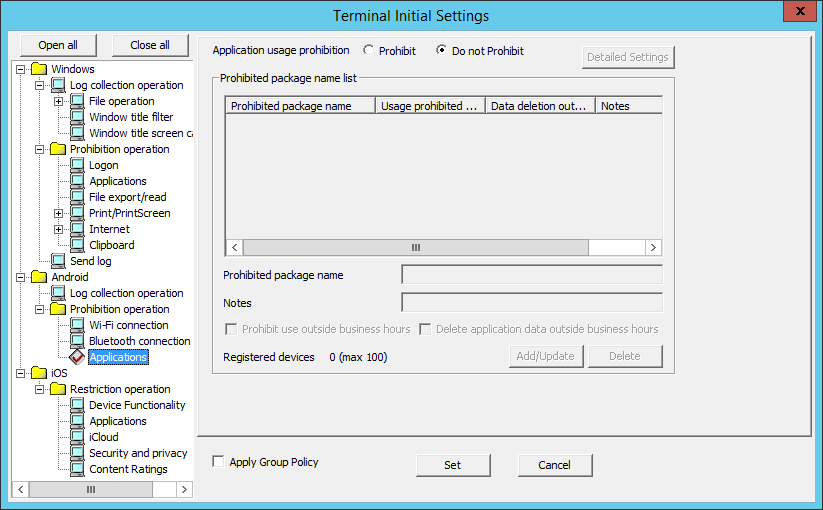
Item name | Description | |
|---|---|---|
Application usage prohibition | Prohibit | Prohibits use of packages specified in Prohibited package name list. |
Do not Prohibit | Any package can be used. | |
Prohibited package name list | Displays the package name and notes for the package to be prohibited. | |
Prohibited package name | Enter the package name. The characters that can be entered comply with the package name convention. Entering of the extension (apk) is optional. Control characters cannot be used. | |
Notes | Enter information such as notes on the packages. | |
Registered devices | The number of registered cases and the maximum number of registrations possible are displayed. | |
Prohibit use outside business hours | Select this to prohibit the use of specified packages outside business hours. | |
Delete application data outside business hours | Select this to delete the data of specified packages outside business hours. If packages for which this item is selected are installed, the following message will be output when outside business hours. This message will be output only once outside business hours. [AA10-WRN004] System administrator prohibits the use of the application outside business hours so the data will be deleted. Tap 'OK'. If the application screen appears, tap 'Clear data' to delete the data. The data in the following folders are deleted automatically: - Folders used by the application - Any folders specified by system administrator Default value: Not selected. Refer to "2.4.2 Perform Terminal Operation Settings" for details on the use outside business hours. | |
detailed Settings | Click this to delete data on external storage devices such as SD cards. The rule for entering the folder name is as follows:
| |
Add/Update | Adds or updates the packages to be prohibited. Information will be updated when Notes for the row selected in Prohibited package name list is changed. A new package will be added when Prohibited package name list is changed. | |
Delete | Deletes the row selected in Prohibited package name list. | |
*1: The absolute path here means the absolute path from the SD cards.
An example is shown below.
To delete files and folders under "/mnt/sdcard/temp/private":
Specify "/temp/private".
To delete files and folders under "/mnt/external_sd/gyomu1/important":
Specify "/gyomu1/important".
In Device Functionality, set the prohibition feature for iOS devices.
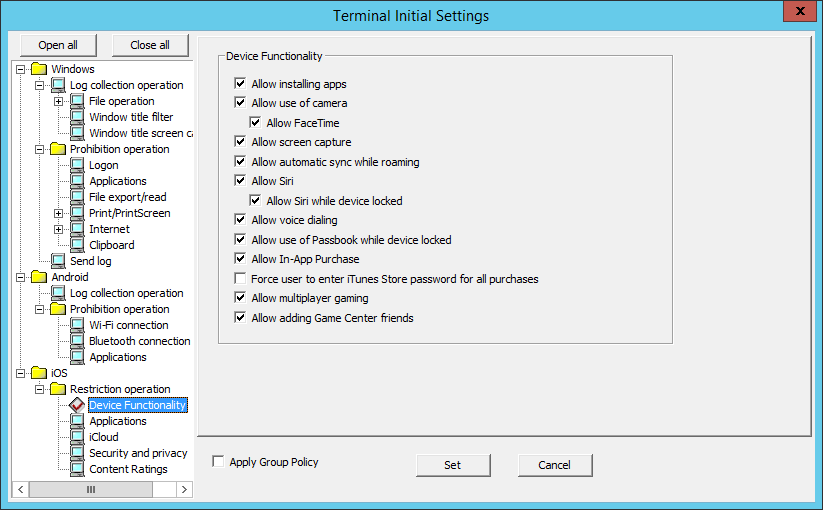
Item name | Description | |
|---|---|---|
Allow installation of apps | Specify whether to allow installation of applications. | |
Allow use of camera | Specify whether to allow use of the camera. | |
Allow FaceTime | Specify whether to allow FaceTime. | |
Allow screen capture | Specify whether to allow screen capture. | |
Allow automatic sync while roaming | Specify whether to allow automatic synchronization during roaming. | |
Allow Siri | Specify whether to allow Siri. | |
Allow Siri while device locked | Specify whether to allow Siri when the device is locked. | |
Allow voice dialing | Specify whether to allow voice dialing. | |
Allow use of Passbook while device locked | Specify whether to allow Passbook when the device is locked. | |
Allow In-App Purchase | Specify whether to allow in-app purchases. | |
Force user to enter iTunes Store password for a purchases | Specify whether to force the user to enter iTunes Store password before any purchase. | |
Allow multiplayer gaming | Specify whether to allow multiplayer gaming. | |
Allow adding Game Center friends | Specify whether to allow Game Center friends to be added. | |
In iOS > Application, set the prohibition feature for iOS applications.
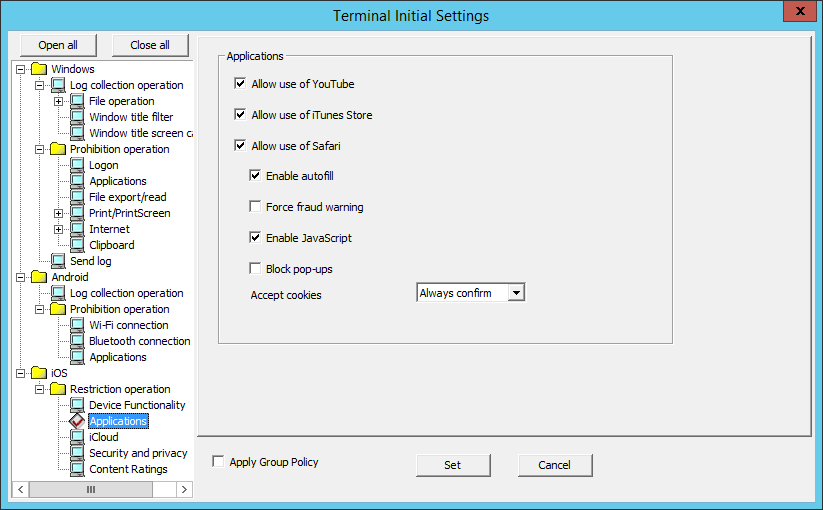
Item name | Description | |
|---|---|---|
Allow use of YouTube | Specify whether to allow use of YouTube. | |
Allow use of iTunes Store | Specify whether to allow use of the iTunes Store. | |
Allow use of Safari | Specify whether to allow use of Safari. | |
Enable autofill | Specify whether to enable autofill. | |
Force fraud warning | Specify whether to allow access to suspicious websites. | |
Enable JavaScript | Specify whether to enable JavaScript. | |
Block pop-ups | Specify whether to enable pop-ups. | |
Accept cookies | Select from the menu to specify whether to enable cookies.
| |
In iCloud, set the iCloud prohibition feature for iOS.
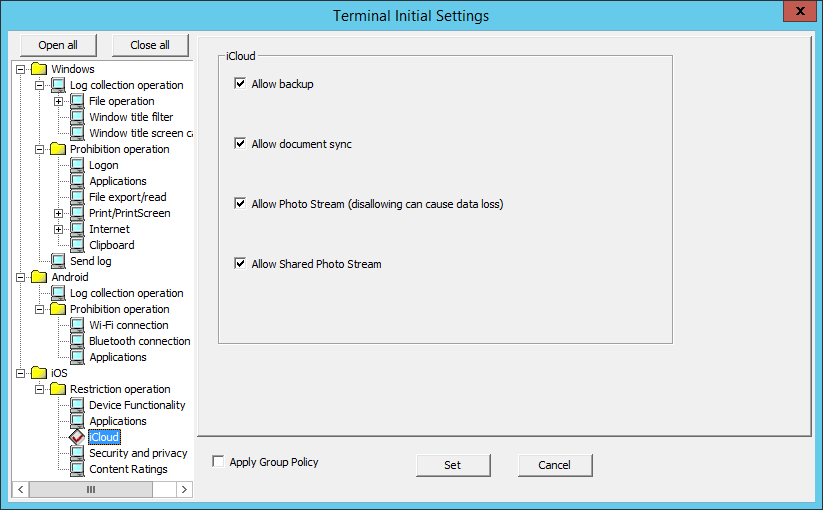
Item name | Description |
|---|---|
Allow backup | Specify whether to allow backup to iCloud. |
Allow document sync | Specify whether to allow document synchronization. |
Allow Photo Stream (disallowing can cause data loss) | Specify whether to allow Photo Stream. |
Allow Shared Photo Stream | Specify whether to allow shared Photo Stream. |
In Security and privacy, configure settings for sending data to Apple and security settings.
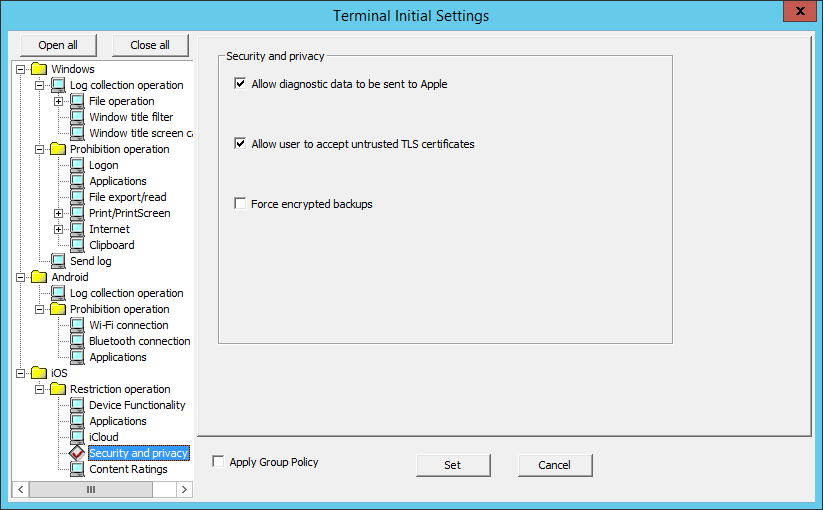
Item name | Description |
|---|---|
Allow diagnostic data to be sent to Apple | Specify whether to allow diagnostic data to be sent to Apple. |
Allow users to accept untrusted TLS certificates | Specify whether to allow untrusted TLS certificates to be accepted. |
Forced encrypted backups | Specify whether to forcibly encrypt backups. |
In Content Ratings, specify the content that can be viewed depending on the ratings.
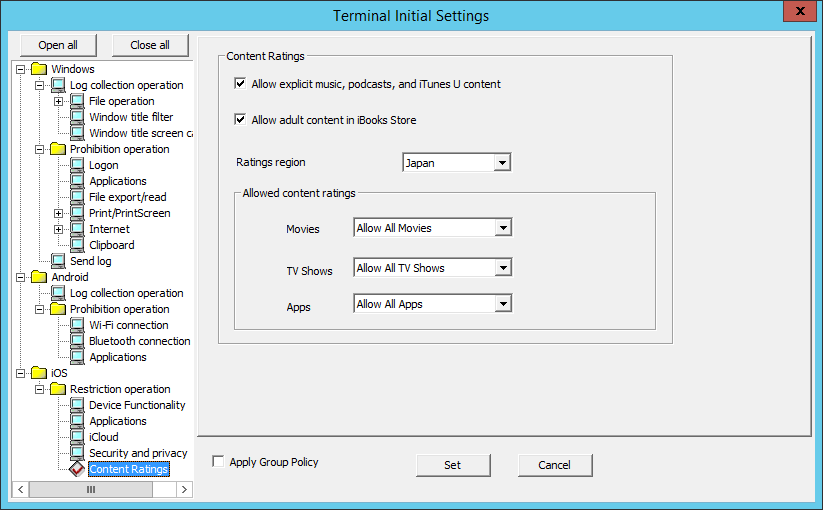
Item name | Description | |
|---|---|---|
Allow explicit music, Podcasts, and iTunes U content | Specify whether to allow explicit music, Podcasts, and iTunes U content. | |
Allow adult content in iBooks Store | Specify whether to allow adult content in iBooks Store. | |
Ratings region | Select the appropriate ratings region from the menu.
Note If Content Ratings is set for an iOS device, region settings different from Ratings region in the iOS device may not take effect. | |
Allowed content ratings | Configure the content prohibition settings to suit the ratings for the region selected in Ratings region. | |
Movies | Select the movie ratings from the menu.
Other selection items vary depending on the region selected in Ratings region. Configure settings in accordance with the ratings for respective regions. | |
TV Shows | Select the TV show ratings from the menu.
Other selection items vary depending on the region selected in Ratings region. Configure settings in accordance with the ratings for respective regions. | |
Apps | Select the application ratings from the menu.
Selection items are common to all regions. | |