By viewing file operation log, the changes in file operation executed by the user can be searched/displayed when the user of a client (CT) with suspected misoperation is detected.
The File Tracing function is a tool for searching/displaying file operation changes that are executed in client (CT) according to "File Operation Log", "File Export Log", "E-mail Sending Log (with attachment)", "E-mail Sending Suspension Log (with attachment)", "E-mail Attachment Prohibition Log", "FTP Operation Log (FTP upload or download)" and "Web Operation Log". Following functions are provided by the File Tracing function.
From the logs that have been searched in Log Viewer, select a file as the file tracing target to trace the operation. In addition, the results of the tracing can be displayed in the window or exported to a CSV file.
The operation logs that can be selected as tracing targets are the following logs that contain file operation information:
File Operation Log
File Export Log
E-mail Sending Log (with attachment)
E-mail Sending Interruption Log (with attachment)
E-mail Attachment Prohibition Log
FTP Operation Log (FTP upload or download)
Web Operation Log (Web upload or download)
In addition, the following logs will be contained in the results of tracing as supplement information of the above operation logs
Printing Operation log
Printing Prohibition log
Note
File operation in Citrix XenApp Client cannot be traced
The file trace function cannot be used in the log viewer via file operation logs in the Citrix XenApp client.
The range of file operation in Systemwalker Desktop Keeper Client (CT) can be traced
The clients of the logs as trace targets are traceable; it is impossible to perform file trace among multiple clients.
Trace File operation
This section describes how to set the file information to be used as tracing target.
To perform file tracing, the file information to be used as a tracing target must be set. To set file information, the following logs that include file operation information should be displayed at first:
File Operation Log
File Export Log
E-mail Sending Log (with attachment)
E-mail Sending Interruption Log (with attachment)
E-mail Attachment Prohibition Log
FTP Operation Log (FTP upload or download)
Web Operation Log
"Printing Operation Log" and "Printing Prohibition Log" cannot be selected as file tracing targets.
To use the file names contained in those logs as tracing targets, enter the "file name" contained in "Printing Operation Log" or "Printing Prohibition Log" in "Keywords" of the CT Operation Log - Log Search window and perform searching. If search results contain the above logs (File Operation Log, File Export Log, or E-mail Sending Log, E-mail Sending Interruption Log, E-mail Attachment Prohibition Log, FTP Operation Log, Web Operation Log), file trace can be executed by setting those logs as tracing targets.
The following describes how to perform file tracing through the file information set in tracing target.
Search (display the search result that includes path in "accuracy") cannot be performed unless the file names of "File Operation Log", "File Export Log", "E-mail Sending Log", "E-mail Sending Interruption Log", "E-mail Attachment Prohibition Log", "FTP Operation Log" and "Web Operation Log" completely match with those of the tracing target (except the path).
In addition, since "Printing Operation Log" and "Printing Prohibition Log" can be searched when their file names partially match with those of the tracing target, in the mean time of tracing the logs of file as tracing target, the logs with lower correlation with the tracing target file will also be searched.
Trace conditions shall be set up for the purpose of trace based on information about trace target files.
Point
You can perform a file trace even when searching the user operation log of a user who browses the Log Viewing Database.
The file trace feature is used in the same way as the CT operation log.
The range of a user operation log file trace is the user name and client (CT) for which the logs that were set as the trace target have been obtained. If there are multiple user names in a client (CT), you cannot perform a trace across multiple user names.
The description below describes how to perform a file trace using the CT operation log file trace feature, but the procedure is the same for the user operation log file trace feature.
Start Log Viewer.
The CT Operation Log(Operation) - Log Search - Log Details window of the operation logs for which the file tracing is executed is displayed.
For display method, refer to "5.2.1 View Logs in the CT Operation Log Window".
Click the File trace button.
When the selected log type is E-mail Sending and multiple attachments are contained in the log, the CT Operation Log - Log Search - File Tracing - Log Details - Select Tracing Target window will be displayed. If the display condition is not satisfied, the CT Operation Log(Operation) - Log Search - File Trace will be displayed.
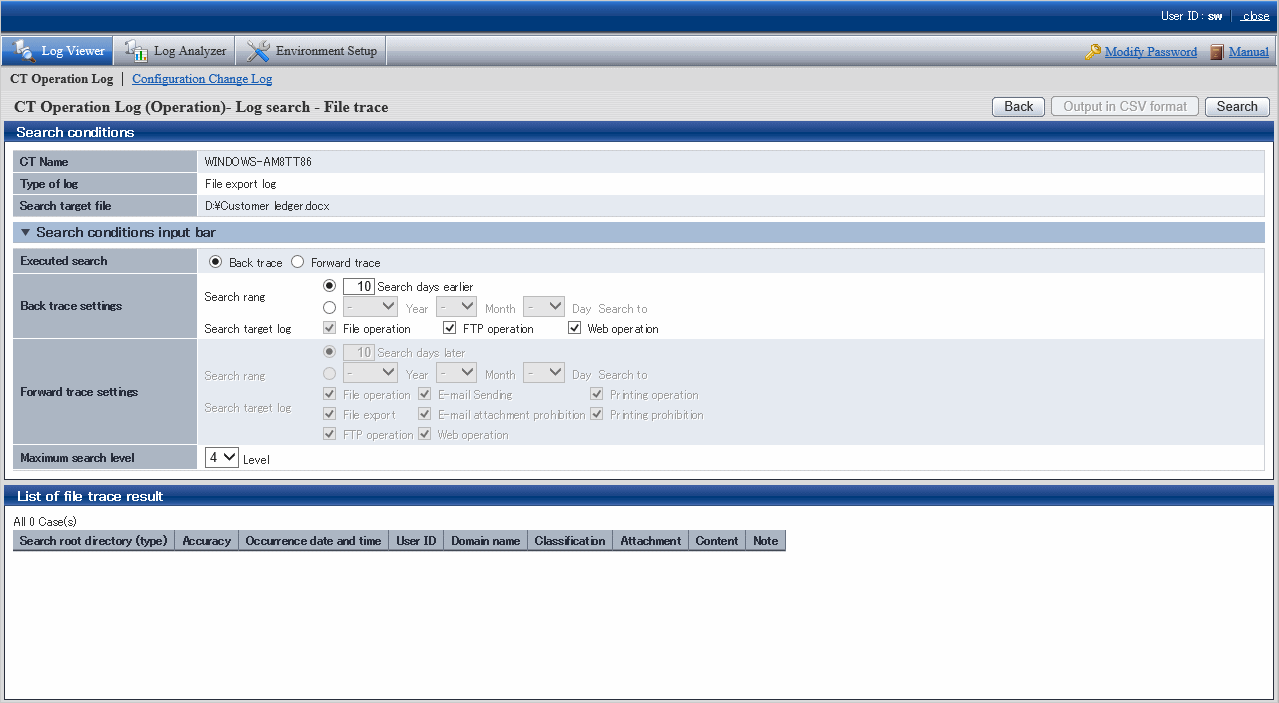
The CT Operation Log - Log Search - File Tracing - Log Details - Select Tracing Target window will be displayed if the following conditions are satisfied:
When the selected log type is E-mail Sending and multiple attachments are contained in the log.
a) The CT Operation Log - Log Search - File Tracing - Log Details - Select Tracing Target window will be displayed.
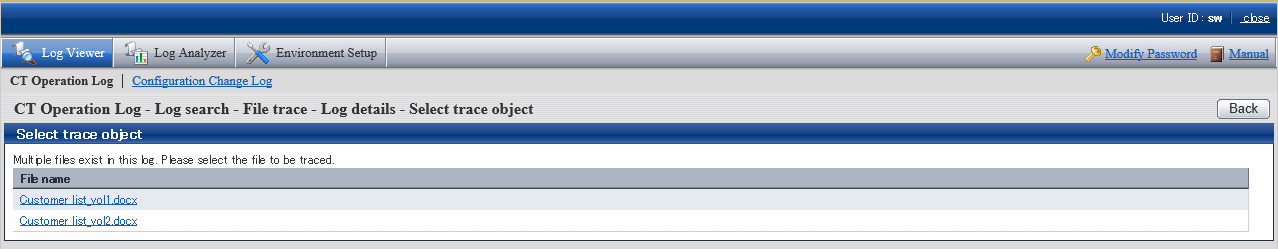
b) Select a file from Select Tracing Target to perform file tracing.
The selected attachment name will be set as file tracing target.
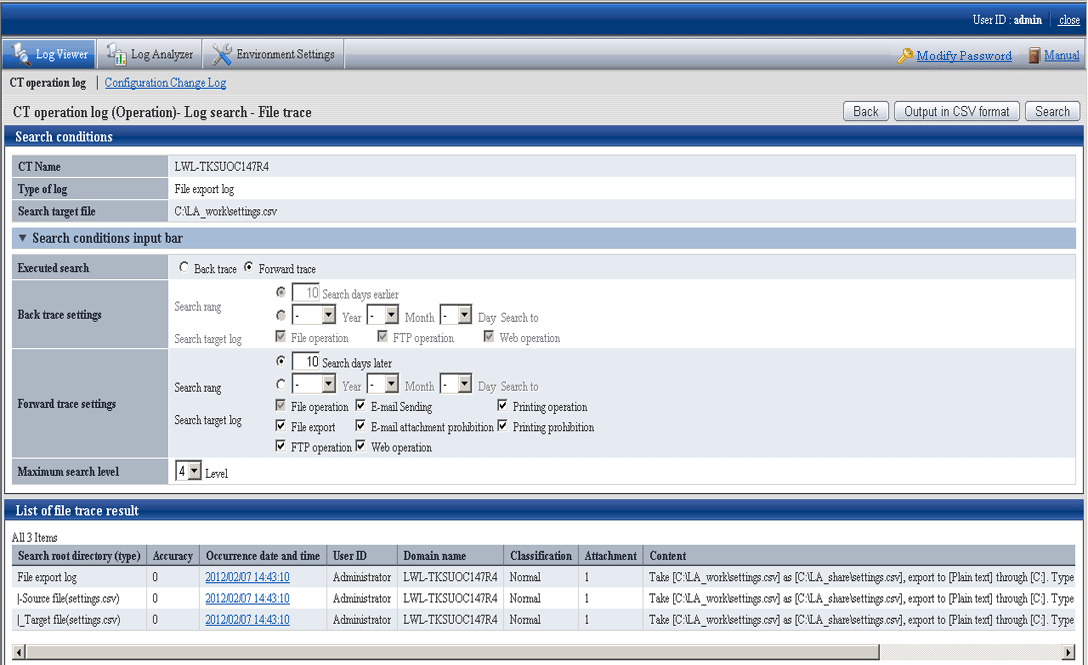
Set up Search Conditions.
Item Name | Description |
|---|---|
CT Name | This is the name of the client (CT) in which the logs selected in Log Viewer are displayed. The scope of file tracing will be the logs collected in this client (CT). |
Type of log | This is the type of log selected in the Log Viewer window. |
Search target file | This is the name of the file to be used as the tracing target. |
Executed search | Back trace Forward trace |
Search range | Specify the search range by time period (days) or date. The initial value is "Period (days)". The period (days) or date that can be specified is shown as follows:
|
Search target log | When Executed search is Forward trace, the type of logs as search target can be selected. File operation log is a mandatory option, so it cannot be set to "OFF". |
Maximum search level | Specify the maximum level for searching. "1" ~ "9" can be specified. The initial value is "4". |
Click the Search button.
Results are displayed in the List of file trace result window.
Search conditions will be saved automatically. The saved search conditions will be set as the initial value for next startup of the File trace window.
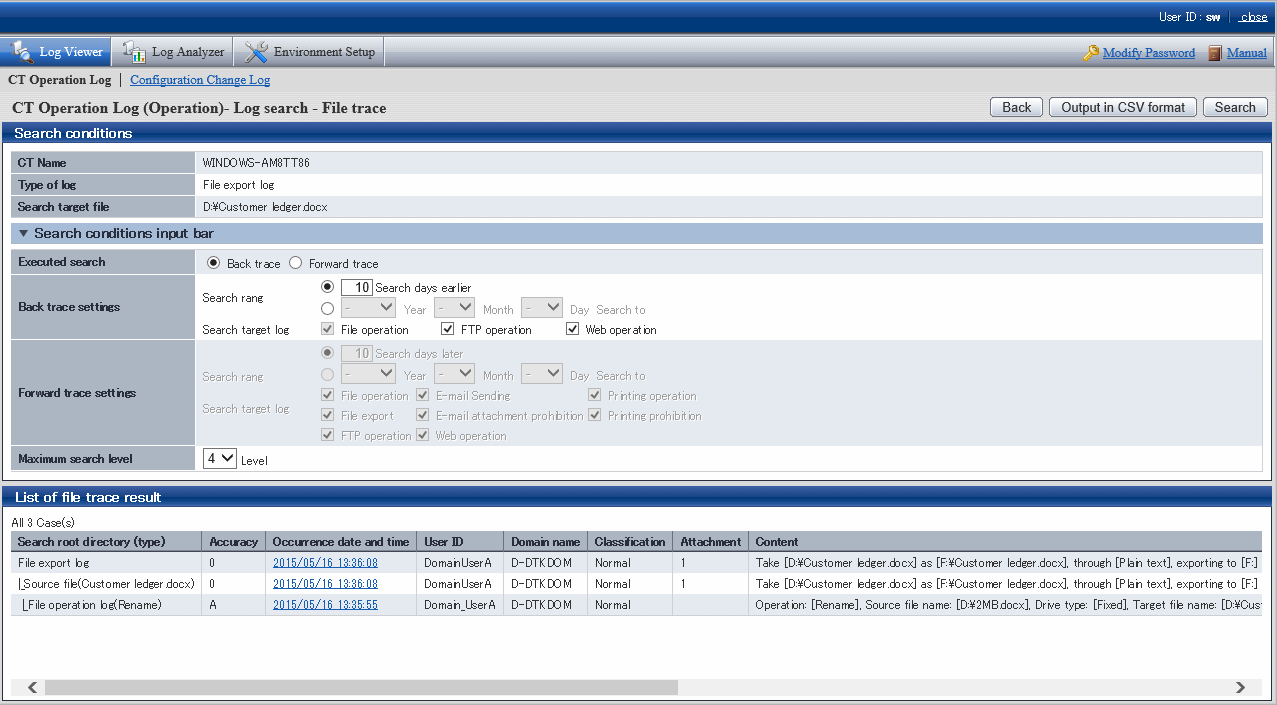
Item Name | Description |
|---|---|
Search root directory (type) | The selected log is displayed at the beginning, and the results of the tracing log are displayed in the tree view. |
Accuracy | Consistency (accuracy) of traced logs: 0: Log of the investigation start target A: Searched logs that are in complete consistency in drive or UNC description B: Searched logs with consistency under share name C: Searched logs with consistency under file name D: Result searched with only consistency in file name E: Searched logs with partial consistency in file name in printing operation log and printing prohibition log" *: Display when same logs exist in trace logs. Add to the front of the above accuracy (A ~ E) +: Display when the log can be traced further. Add to the front of the above accuracy (A ~ E) |
Occurrence Date and Time | This displays the time when log occurrence date and time. |
User ID | Display the user name |
Domain name | The domain name of the client (CT) when logging on to a domain. This is the computer name when logging on to a local computer. |
Classification | Type of log (normal or Violation) |
Attachment | Display whether the attached data of log exists or not. For the content of attached data, refer to "View attached data". |
Content | Display the content of the log. |
Notes | Display the notes of the log. |
When there are more than 1,000 search results, a message indicating that search processing was canceled will be displayed and only the first 1,000 search results will be displayed.
This refers to a process of searching how the files are processed in the past according to the selected log. Only Copy, Cut, Rename, Create, Update, Delete operations of File Operation Log and export operations of the File Export Log will be traced. This is used while investigating previous file operations.
Example of back trace search:
(Investigation target file: customer information.txt)
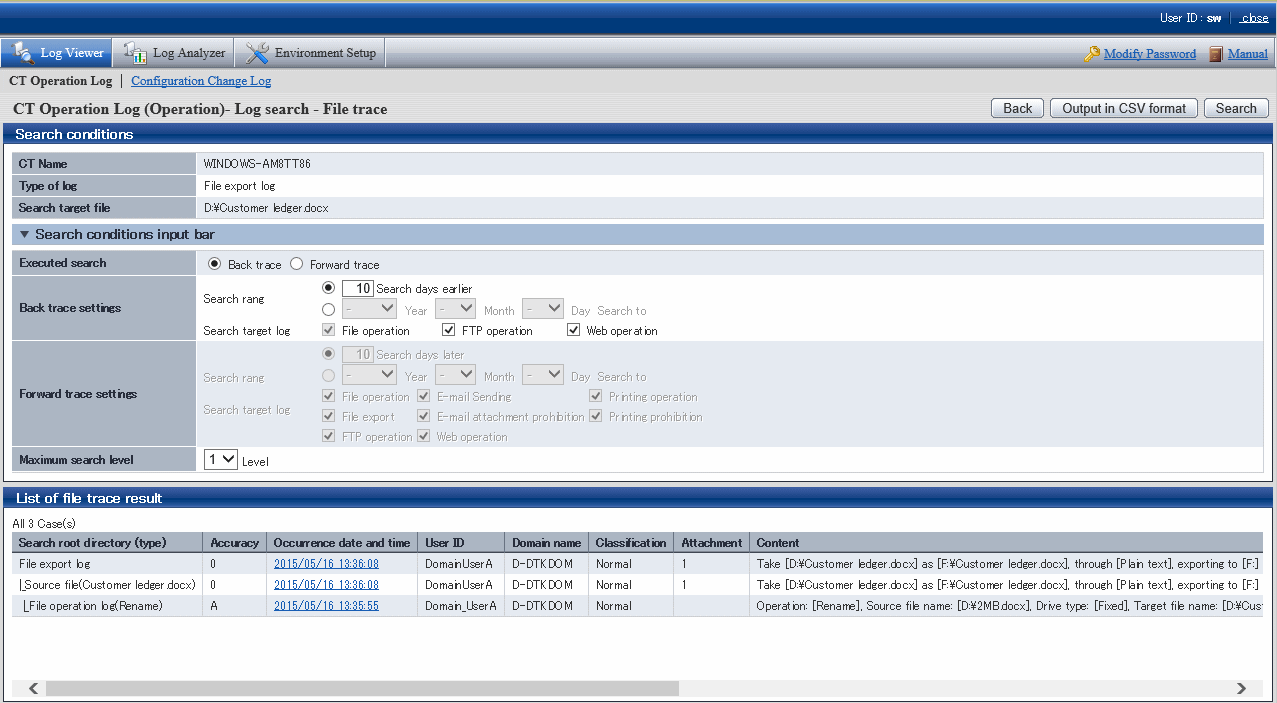
Pay attention to Content in List of File Tracing Results.
Information of [Search Route (Type)] | Information of [Content] |
|---|---|
File Export Log | Export [C:\Documents and Settings\Administrator\Desktop\Customer Information.txt] to [A:] as [A:\Customer Information.txt] in [Plain text]. |
Source File (Customer Information.txt) | Export [C:\Documents and Settings\Administrator\Desktop\Customer Information.txt] to [A:] in [Plaintext] as [A:\Customer Information.txt]. |
File Operation Log (Copy) | Operation: [Copy]; Source file name: [\\192.168.1.11\share\Customer Information.txt]; Source drive type: [Remote]; Target file name: [C:\Documents and Settings\Administrator\Desktop\Customer Information.txt]; Target drive type: [Fixed]; Name of application: [Explorer.exe] |
The information of investigation target file (Customer Information List.xls) is displayed in the first line. As proceeding to different stages, the previous operation will be traced.
Viewing from the start record of search results, this file is in the client (CT) with the name of SV2
1. The target file for investigation (Customer Information.txt) is exported to a removable media in plain text.
2. The target file for investigation (Customer Information.txt) on the file server is copied to SV2.
This operation record indicates that after the file "Customer Information.txt" is copied to desktop and exported to removable media in plain text.
This refers to a process of searching how the files are processed later according to the selected log. The operation process since the generation occurrence date and time of the operation logs specified as tracing target can be investigated. One file may be changed to multiple files by using the copy operation, and the search result may increase, which results from an expanded search target in the log.
Example of Forward Trace Search:
(Investigation target file: customer information.txt)
Pay attention to Content in List of file tracing result.
[Search Route (Type)] | [Content] |
|---|---|
File Export Log | Export [C:\Documents and Settings\Administrator\Desktop\Customer Information.txt] to [A:] as [A:\Customer Information.txt] in [Plain text]. |
File Operation Log (Delete) | Operation: [Delete]; Source file name: [C:\Documents and Settings\Administrator\Desktop\Customer Information.txt]; Drive type: [Fixed]; Name of application: [Explorer.exe] |
The information of the investigation target file (Customer Information List.xls) is displayed in the first line. As proceeding to different stages, information on how the investigation target file has been processed up to now will be displayed.
Viewing from the start record of search results, this file is in the client (CT) with the name of SV2
1. Export Customer Information.txt.
2. Delete Customer Information.txt from local disk.
This operation record indicates that the customer information is deleted after exporting to the external.
Export tracing result of file operation to CSV file
This department describes how to export searched file trace results to a CSV file.
When the trace logs to be exported to a CSV file are displayed in List of file tracing result, click the Output in CSV format button.
When the file download window is displayed, click the Save button.
After selecting the saving folder and entering the file name, click the Save button.
The following symbols cannot be used as file name:
"\", "/", ":", "*", "?", " "", "<", ">", "|"
When a file with same name exists in the export destination, the option window indicating whether to overwrite will be displayed. Select the desired option.
For item name and description of an exported CSV file, refer to "Log List of File Trace Result" of Systemwalker Desktop Keeper Reference Manual.
Reset tracing file to trace file again
This department describes how to execute file tracing again after modifying the tracing target file according to the searched file trace result.
Select a log with the file information needed to be reset from List of file trace result of the CT Operation Log (Operation) - Log Search - File Trace window, and click Occurrence date and time.
"Printing Operation Log" and "Printing Prohibition Log" will be displayed as additional information in File Trace Results, but they cannot be selected as search target.
Click the Reset Trace object button.
The file name is set in Search target file .
When selecting an E-mail sending log that has multiple attachments, the Select Tracing Target window will be displayed first. Select a file name in the Select Tracing Target window and set it as Search Target File.
Set search conditions, and click the Search button.
The results of tracing will be displayed in List of file trace results.
When file download is not successful
When the download of CSV file, original file backup and command operation file is not successful, refer to "Preparation of Using Web Browser in PC" of Systemwalker Desktop Keeper Installation Guide to modify the settings of Internet Explorer(R)