This chapter explains how to build and set up Interstage Single Sign-on.
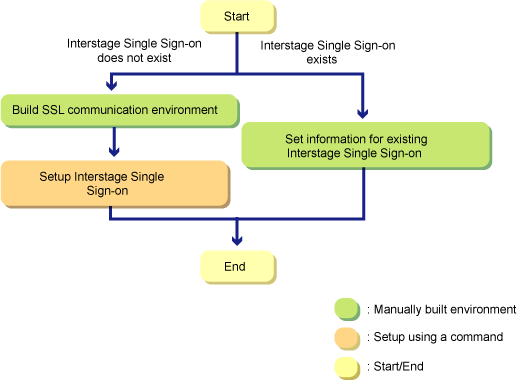
The flow for the setup of Interstage Single Sign-on and the setting of information in the existing Interstage Single Sign-on is shown below:
Note
Execute the procedures explained in this chapter using administrator privileges.
The LDAP using Interstage Single Sign-on is only Interstage directory service. You do not use Active Directory/OpenLDAP.
Log into the Interstage Management Console explained on this chapter in the following procedure.
Input the following URL to the browser and display the Log in windows. Specify system administrator for operating system as user login.
http://[The hostname for Management server]:[Interstage Management Console port number]/IsAdmin
or
https://[ The hostname for Management server]:[Interstage Management Console port number]/IsAdmin
This section explains how to build the SSL communication environment.
Note
There is no need to perform this task if the SSL communication environment build is already completed.
Procedure to build the SSL communication environment
Build the SSL communication environment as preparation before the Interstage Single Sign-on setup.
Build the SSL communication environment using the following procedure:
Setting the Interstage Certificate Environment Access Permissions
Creating the Interstage Certificate Environment and the Application to Obtain the Certificate that is used for SSL Communication
Registering Certificates used in SSL Communication
Settings for SSL Communication
Information
Refer to "Setting and Use of the Interstage Certificate Environment" in the Interstage Application Server Security System Guide for information on how to build the SSL environment.
Create an owner group that has permissions to access the Interstage certificate environment.
An example of creating the owner group using the command is shown below:
Note
This task is only required if the platform to build Interstage Single Sign-On is Linux. This task is not required for Windows.
Create the Interstage certificate environment owner group.
In the following example, the owner group is created as "iscertg".
# groupadd iscertg
Note
The owner group that was created at the time of the Interstage certificate environment build must be specified in the -g option of the Certificate Signing Request (CSR) creation command (scsmakeenv). Refer to "3.1.3.1.2 Creating the Interstage Certificate Environment and the Application to Obtain the Certificate that is used for SSL Communication" for information on the CSR creation command.
Register the executing user in the "iscertg" group.
In the following example, the executing user is created as "nobody".
# usermod -G iscertg nobody
Note
The executing user that is registered in the Interstage certificate environment owner group must have been set in the User directive of the Interstage HTTP Server environment configuration file (httpd.conf). The user "nobody" has been set if you installed Interstage Application Server bundled with Systemwalker Service Catalog Manager.
The CSR creation command (from now on, this is referred to as the "scsmakeenv command") is used to create the CSR that will create the Interstage certificate environment and apply for the certificate that is used for SSL communication.
The creation procedure and execution example are shown below:
Creation procedure
Set the JDK or JRE installation path in the JAVA_HOME environment variable. This procedure is only required for Linux. Setting of the environment variable JAVA_HOME is unnecessary for Windows.
Execute the scsmakeenv command.
[Windows]
scsmakeenv -n <private key nickname> -f <output destination file name for the CSR>
[Linux]
scsmakeenv -n <private key nickname> -f <output destination file name for the CSR> -g <Group that has permissions to access the Interstage certificate environment>
Change the CSR output destination file name if necessary.
Note
The private key nickname specified in the scsmakeenv command will be required when the site certificate obtained from the CA is registered.
Information
Refer to " SSL Environment Setting Commands" in the Interstage Application Server Reference Manual (Command Edition) for information on the scsmakeenv command.
Enter a password to access the Interstage certificate environment.
The password will be required to access the Interstage certificate environment.
Enter an identifier.
When the "What is your first and last name?" (alphanumeric name) enquiry is made, specify the FQDN of the server used to apply for the certificate as the Web server host name.
As with step 4, enter the following items:
Name of organizational unit
Name of organization
Name of City or Locality
Name of State or Province
Two-letter country code
Check the values that were entered.
To create the CSR using the values that were entered, enter yes. To change the values that were entered, enter no.
Send the CSR to the CA to request that a certificate be issued.
If the scsmakeenv command has terminated normally, the CSR will be output to the certificate output destination file name that was specified in the -f option of the scsmakeenv command. Send that file to the CA and request that a certificate be issued. Follow the request method used by the CA.
Execution example [Windows]
The command execution examples shown below use the following values:
- Site certificate nickname: SERVERCERT - Applicant output destination file name: C:\temp\ssocert.txt - First and last name: ssoserver.example.com - Name of organizational unit: FUJITSU TOKYO - Name of organization: FUJITSU - Name of City or Locality: Shinjuku - Name of State or Province: Tokyo - Two-letter country code for this unit:jp
In the example, the applicant output file name is "C:\temp\ssocert.txt". Change the applicant output file name if necessary.
At the password prompt, enter the password that will be used to access the Interstage certificate environment. (it will not be displayed).
C:\>scsmakeenv -n SERVERCERT -f C:\temp\ssocert.txt New Password: Retype: Input X.500 distinguished names. What is your first and last name? [Unknown]: ssoserver.example.com What is the name of your organizational unit? [Unknown]: FUJITSU TOKYO What is the name of your organization? [Unknown]: FUJITSU What is the name of your City or Locality? [Unknown]: Shinjuku What is the name of your State or Province? [Unknown]: Tokyo What is the two-letter country code for this unit? [Un]: jp Is <CN=ssoserver.example.com, OU=FUJITSU TOKYO, O=FUJITSU, L=Shinjuku, ST=Tokyo,C=jp> correct? [no]: yes <SCS: INFO: scs0101: CSR was issued <C:\temp\ssocert.txt> C:\>
Execution example [Linux]
The command execution examples shown below use the following values:
- Site certificate nickname: SERVERCERT - Applicant output destination file name: /tmp/ssocert.txt - Group that has permissions to access the Interstage certificate environmentiscertg - First and last name: ssoserver.example.com - Name of organizational unit: FUJITSU TOKYO - Name of organization: FUJITSU - Name of City or Locality: Shinjuku - Name of State or Province: Tokyo - Two-letter country code for this unit:jp
In the execution example, a new Interstage certificate environment is created for which "iscertg" access permissions are set, and the CSR is also created. If an Interstage certificate environment has already been created, then set access permissions to it if necessary.
The Bourne shell has been used in the execution example.
# JAVA_HOME=/opt/FJSVawjbk/jdk6;export JAVA_HOME # scsmakeenv -n SERVERCERT -f /tmp/ssocert.txt -g iscertg New Password: Retype: Input X.500 distinguished names. What is your first and last name? [Unknown]: ssoserver.example.com What is the name of your organizational unit? [Unknown]: FUJITSU TOKYO What is the name of your organization? [Unknown]: FUJITSU What is the name of your City or Locality? [Unknown]: Shinjuku What is the name of your State or Province? [Unknown]: Tokyo What is the two-letter country code for this unit? [Un]: jp Is <CN=ssoserver.example.com, OU=FUJITSU TOKYO, O=FUJITSU, L=Shinjuku, ST=Tokyo,C=jp> correct? [no]: yes UX:SCS: INFO: scs0101: CSR was issued </tmp/ssocert.txt> UX:SCS: INFO: scs0180: The owners group of Interstage certificate environment was set. #
Note
You will be prompted to input password for Interstage certificate environment if Interstage certificate environment is already configured. In this case, input the password that was set when you configured Interstage certificate environment.
Information
Test site certificates can be used in the test environment. Note that these test site certificates are only for test environments, and so should not be used for actual operations.
Refer to Appendix B Creating Test Site Certificates for information on creating test site certificates.
Obtain the site certificate that was issued by the CA, and the CA certificate of the issuer of that certificate, and register them using the certificate/CRL registration command (from now on, this is referred to as the "scsenter command").
Information
Depending on the CA, it might be necessary to register an intermediate CA certificate. Refer to "Registering Certificates and CRLs" in " Setting and Use of the Interstage Certificate Environment" in the Interstage Application Server Security System Guide for details.
This work is unnecessary if you created a test site certificate.
Creation procedure
Set the JDK or JRE installation path in the JAVA_HOME environment variable.
This is necessary procedure for Linux. For Windows, it is not necessary.
Register the CA certificate using the scsenter command.
scsenter -n <CA certificate nickname> -f <CA certificate>
Information
Refer to "SSL Environment Setting Commands" in the Interstage Application Server Reference Manual (Command Edition) for information on the scsenter command.
Enter a password to access the Interstage certificate environment.
Enter the password that was specified in the scsmakeenv command to access the Interstage certificate environment.
Register the site certificate using the scsenter command.
scsenter -n <Site certificate nickname> -f <Site certificate> -o
To register the site certificate that was obtained from the CA, specify the nickname that was specified in the private key in the scsmakeenv command. Note that the -o option must be specified to register the site certificate.
Enter a password to access the Interstage certificate environment.
Enter the password that was specified in the scsmakeenv command to access the Interstage certificate environment.
Execution example [Windows]
The command execution examples shown below use the following values:
- CA certificate: C:\temp\ca-cert.cer - CA certificate nickname: CACERT - Site certificate: C:\temp\server-cert.cer - Site certificate nickname: SERVERCERT
In the examples, the CA and site certificates obtained are "C:\temp\ca-cert.cer" and "C:\temp\server-cert.cer". Change the file path name of each certificate if necessary.
At the password prompt, enter the password that will be used to access the Interstage certificate environment (it will not be displayed).
C:\>scsenter -n CACERT -f C:\temp\ca-cert.cer Password: Certificate was added to keystore SCS: INFO: scs0104: Certificate was imported. C:\>scsenter -n SERVERCERT -f C:\temp\server-cert.cer -o Password: Certificate reply was installed in keystore SCS: INFO: scs0104: Certificate was imported. C:\>
Execution example [Linux]
The command execution examples shown below use the following values:
- CA certificate: /tmp/ca-cert.cer - CA certificate nickname: CACERT - Site certificate: /tmp/server-cert.cer - Site certificate nickname: SERVERCERT
Change the file names of the CA and site certificates that were obtained if necessary.
The Bourne shell has been used in the execution example.
# JAVA_HOME=/opt/FJSVawjbk/jdk6;export JAVA_HOME # scsenter -n CACERT -f /tmp/ca-cert.cer Password: Certificate was added to keystore UX:SCS: INFO: scs0104: Certificate was imported. # scsenter -n SERVERCERT -f /tmp/server-cert.cer -o Password: Certificate reply was installed in keystore UX:SCS: INFO: scs0104: Certificate was imported. #
Using the Interstage Management Console, create the SSL definition.
Start the Interstage Management Console.
Follow the procedure below to start the Interstage Management Console:
Start the Web browser.
Specify the Interstage Management Console URL.
The URL format is shown below:
(When SSL encrypted communication is not used)
http://[host name of the Management Server]:[port number for the Interstage Management Console]/IsAdmin/
(When SSL encrypted communication is used)
https://[host name of the Management Server]:[port number for the Interstage Management Console]/IsAdmin/
Log into the Interstage Management Console.
Create the SSL definition.
Select the System >> Security >> SSL >> Create a new SSL Configuration tabs to show General Settings, then select the registered site certificate nickname, then create the SSL definition.
Specify the following items, then push Create button.
Settings item | Settings value |
|---|---|
Configuration name | Set the name that will identify the SSL definition.
|
Site Certificate Nickname | Set the nickname that was specified when the site certificate was registered in the Interstage certificate environment, in "3.1.3.1.3 Registering Certificates used in SSL Communication". The site certificate that was selected can be checked in the System >> Security >> Certificates >> Site Certificates window of the Interstage Management Console. |
Protocol Version | Select "SSL 3.0" and "TLS 1.0". |
Verify Client Certificate? | Select "No". |
Encryption Method | Refer to the Interstage Management Console Help, and change this if necessary. |
CA Certificate Nickname | Refer to the Interstage Management Console Help, and change this if necessary. |
This section explains how to set up Interstage Single Sign-On.
Note
There is no need to perform this task if the Interstage Single Sign-On setup is already complete.
Using the Interstage Management Console, create the Management Server Web server (Interstage HTTP Server).
Note
There is no need to perform this task if the Management Server Web server has already been built. Normally, this is created automatically at the time of product installation.
Using the Interstage Management Console, create the Management Server Web server (Interstage HTTP Server).
Start the Interstage Management Console.
Follow the procedure below to start the Interstage Management Console:
Start the Web browser.
Specify the Interstage Management Console URL.
The URL format is shown below:
(When SSL encrypted communication is not used)
http://[host name of the Management Server]:[port number for the Interstage Management Console]/IsAdmin/
(When SSL encrypted communication is used)
https://[host name of the Management Server]:[port number for the Interstage Management Console]/IsAdmin/
Log into the Interstage Management Console.
Create the Management Server Web server (Interstage HTTP Server).
Select the System >> Services >> Web Server >> Create a new Web Server tabs, and configure the Interstage HTTP Server environment settings.
Specify the following items:
Settings item | Settings value |
|---|---|
Web Server Name | Set "FJapache". |
Port Number | Set "80". |
Select the Web server name that was created, open the environment settings tab, click Detailed Settings >> Show, change the environment settings as shown below, then click the Update button.
Settings item | Settings value |
|---|---|
Enable SSL Encryption | Select "No". |
Set up Interstage Single Sign-On using the Interstage Single Sign-On Setup command ("ssoclsetup command").
By executing the ssoclsetup command, the servers shown below that are required for Interstage Single Sign-On is built:
Repository server (update type)
Authentication server
Business server
Following information is set by ssoclsetup command.
Settings item | Settings value |
|---|---|
Public directory | ou=interstage, o=fujitsu, dc=com |
Administrator DN | cn=manager, ou=interstage, o=fujitsu, dc=com |
Authentication Web server name | SSOauth |
Authentication server port number | 10443 |
Idle monitoring time | 30 min. |
Re-authentication interval | 480 min. |
Lock User | Consecutive failures: 6 |
Release lock | Auto release time: 30 min. |
Business server name | FJapache |
Business server port number | 80 |
Note
The following information is required to execute the ssoclsetup command:
(Mandatory)
Server FQDN
SSL definition
For the SSL definition, specify the SSL definition created in "3.1.3.1.4 Settings for SSL Communication". Refer to the Building environment command in the Systemwalker Runbook Automation Reference Guide for information on the ssoclsetup command
Creation procedure
Perform the following tasks beforehand if this product has been installed in "C:\Program Files (x86)" on a machine running 64-bit Windows:
Create the following two folders. The folder name can contain up to 192 characters, and can contain alphanumeric characters, whitespace characters, and the following symbols ($ & ' + - . = @ _ ` ~ [ ] { } : /).
The SSO repository database storage folder (Example:C:\SSORepository\Database)
The SSO repository access log storage folder (Example:C:\SSORepository\var)
Edit the following SSO repository operating environment definition file:
[Systemwalker Runbook Automation Management Server installation directory]\sso\F3FMctsec\sso\conf\irep\irep.conf
Specify the directory created in the previous step as indicated below:
SSO repository database storage directory
[Before]
#ena_directory:
[After (Example)]
Example in which C:\SSORepository\Database was created as the SSO repository database storage directory:
ena_directory: C:\SSORepository\Database
SSO repository access log storage directory
[Before]
#accesslog_dir:
[After (Example)]
Example in which C:\SSORepository\var was created as the SSO repository access log storage directory:
accesslog_dir: C:\SSORepository\var
Execute the ssoclsetup command:
[Windows]
[Systemwalker Runbook Automation Management Server installation directory]\sso\bin\ssoclsetup FQDN SSLConfName [-rn RepositoryName] [-lp LDAPPort]
[Linux]
/opt/FJSVctsec/sso/bin/ssoclsetup FQDN SSLConfName [-rn RepositoryName] [-lp LDAPPort]
Enter the SSO repository administrator DN password. Note that $, \, ", and spaces must not be used.
For the detail of ssoclsetup command, refer to "ssoclsetup (Interstage Single Sign-on Setup Command)"
in the Systemwalker Runbook Automation Reference Guide.
By executing the ssoclsetup command, the servers shown below that are required for Single Sign-On is built.
Repository server (update type)
Authentication server
Business server
Execution example [Windows]
The command execution examples shown below use the following values:
- Server FQDN: ssoserver.example.com - SSL definition: AuthSSL - Repository name:rep001 - Repository port number:389
Change the FQDN and SSL definition if necessary.
In Systemwalker Runbook Automation, the command is stored in the following folder:
[Systemwalker Runbook Automation Management Server installation directory]\sso\bin
ssoclsetup ssoserver.example.com AuthSSL Please input SSO Repository administrator DN password Password: Retype: IREP: INFO: irep10815: Password file was created. file=C:\INTERS~3\F3FMsso\ssoatcsv\conf\tmp_passwdfile checking the repository configuration... (1/4) initializing the repository... (2/4) creating the public directory. (3/4) updating the repository management list... (4/4) IREP: INFO: irep70001: Repository environment configured. [rep001] IHS: INFO: ihs01000: The command terminated normally. IHS: INFO: ihs01000: The command terminated normally. IHS: INFO: ihs01000: The command terminated normally. IREP: INFO: irep70000: Repository environment setup updated. [rep001] IHS: INFO: ihs01000: The command terminated normally.
Execution example [Linux]
The command execution examples shown below use the following values:
- Server FQDN: ssoserver.example.com - SSL definition name: AuthSSL - Repository name:rep001 - Repository port number:389
Change the FQDN and SSL definition name if necessary.
The Bourne shell has been used in the execution example.
# /opt/FJSVctsec/sso/bin/ssoclsetup ssoserver.example.com AuthSSL Please input SSO Repository administrator DN password Password: Retype: UX:IREP: INFO: irep10815: Password file was created. file=/etc/opt/FJSVssosv/conf/tmp_passwdfile checking the repository configuration... (1/4) initializing the repository... (2/4) creating the public directory. (3/4) updating the repository management list... (4/4) UX:IREP: INFO: irep70001: Repository environment configured. [rep001] UX:IREP: INFO: irep10000: Repository started. [rep001] UX:IHS: INFO: ihs01000: The command terminated normally. UX:IHS: INFO: ihs01000: The command terminated normally. UX:IHS: INFO: ihs01000: The command terminated normally. UX:IREP: INFO: irep70000: Repository environment setup updated. [rep001] UX:IREP: INFO: irep10000: Repository started. [rep001] UX:IHS: INFO: ihs01000: The command terminated normally.
This section explains the setting of information in the existing Interstage Single Sign-On.
This section explains the setting of additional roles in the existing Interstage Single Sign-On.
Creation procedure
Check public directory that was set as SSO repository of existing Interstage Single Sign-On.
Open System >> Services >> Repository, and click repository name that was set as SSO repository to check the public directory.
Check LDIF file defining roles.
Confirm that the LDIF file defining roles is stored in the following place.
[Windows]
[Systemwalker Runbook Automation Management Server installation directory]\sso\ldif\cloud_role.ldif
[Linux]
/opt/FJSVswrba/sso/ldif/cloud_role.ldif
Copy the LDIF file defining roles to another folder, and open the copied file.
Confirm that the following string is set in the file.
$PUBLIC_DIR$
%PUBLIC_DIR%
Note
Open the copied file because the LDIF file described in step 2 is the master file.
Change string which confirmed in step3 to value of public directory which confirmed in step1.
Specify the file changed in 4 in the ldapmodify command, and add the role to the existing Interstage Single Sign-On.
Refer to the Interstage Application Server Reference Manual (Command Edition) for information on the ldapmodify command.
Using the Interstage Management Console click System >> Security >> Single Sign-on >> Authentication Infrastructure >> Repository Server >> Update Role Information tab, Update button.
Settings example
The LDIF file settings example shown below uses the following environment:
- Public directory: ou=interstage,o=fujitsu,dc=com
dn: cn=CFMGSystemAdmin,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: CFMGSystemAdmin dn: cn=CFMGSystemUser,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: CFMGSystemUser #Systemwalker Service Catalog Manager V14g Role dn: cn=CTMGProviderAdmin,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: CTMGProviderAdmin dn: cn=sop_contractor,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: sop_contractor dn: cn=sop_resource_manager,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: sop_resource_manager dn: cn=sop_delegated_manager,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: sop_delegated_manager dn: cn=sop_restricted_user,ou=Role,ou=SSO ACI,ou=interstage,o=fujitsu,dc=com objectClass: ssoRole objectClass: top cn: sop_restricted_user
Execute ldapmodify command.
Execute the ldapmodify command specifying the LDIF file modified in step 5 to add roles to Interstage Single Sign-On.
The command execution examples shown below use the following settings values:
- SSO repository FQDN: existing_ssoserver.example.com - SSO repository port number: 389 - SSO repository administrator DN: cn=manager,ou=interstage,o=fujitsu,dc=com - SSO repository administrator DN password: admin
[Interstage Application Server installation directory]\bin\ldapmodify -H ldap://existing_ssoserver.example.com: 389 -D "cn=manager,ou=interstage,o=fujitsu,dc=com" -w admin -a -f copy destination folder\cloud_role.ldif
The command execution examples shown below use the following values:
- SSO repository FQDN: existing_ssoserver.example.com - SSO repository port number: 389 - SSO repository administrator DN: cn=manager,ou=interstage,o=fujitsu,dc=com - SSO repository administrator DN password: admin
# /opt/FJSVirepc/bin/ldapmodify -H ldap://existing_ssoserver.example.com:389 -D "cn=manager,ou=interstage,o=fujitsu,dc=com" -w admin -a -f copy destinationAfter the command has been executed, using the Interstage Management Console click System >> Security >> Single Sign-on >> Authentication Infrastructure >> Repository Server >> Update Role Information tab, Update button.
To use the existing Interstage Single Sign-On, the repository server environment settings must be configured.
With the Interstage Management Console, register the repository server using the following procedure:
Perform the environment settings for repository server.
Click System >> Security >> Single Sign-on >> Authentication infrastructure >> Repository server, then select the Settings tab.
Click Repository server detailed settings >> Show, then set "o" in Information notified to the Business System >> Extended user information, then click Update button.
Restart the authentication server.
Click System >> Services >> Web Server >> [SSOauth], then select the Web Server Status tab
When the status of the Web server (SSOauth) is running: Click Stop Button, then click Start button.
When the status of the Web server (SSOauth) is stopped: Click [start] button.
To use the existing Interstage Single Sign-On, the Management Server must be registered in the existing Interstage Single Sign-On.
With the Interstage Management Console, register the Management Server using the following procedure:
Registering Management Server Site Definitions
Registering Protected paths
Creating the Business system setup file
Adding Interstage Single Sign-On Business Servers
Suppressing Contents Cache
Note
The ssoclsetup command cannot be used to register the Management Server.
Registering Management Server Site Definitions
With the Interstage Management Console, set the Management Server public URL using the following procedure:
Start the Interstage Management Console.
Refer to 3.1.3.2.1 Creating the Management Server Web Server for the Management Server for information on the Interstage Management Console start procedure.
Set the Management Server public URL.
Open the System >> Security >> Single Sign-on >> Authentication infrastructure >> Repository server >> Protected resource >> New tab.
In Site Definition >> FQDN, Port Number, enter the Management Server FQDN and port number (80) then click the Create button.
Registering Protected Paths
With the Interstage Management Console, register the protected path using the following procedure:
Start the Interstage Management Console.
Refer to 3.1.3.2.1 Creating the Management Server Web Server for information on the Interstage Management Console start procedure.
Register the protected path.
Select the System >> Security >> Single Sign-on >> Authentication infrastructure >> Repository server >> Protection Resource >> Management Server FQDN:80 >> Protection Path >> Create a New Path configuration tab.
Set the role/roleset for the path definition and path as shown below, then create the new protected path.
Path Configuration Settings | Role/Roleset (Select the following items) | |
|---|---|---|
Path | Notify extended user information | |
/console/Default/ | - | - |
/managerview/ | Select "o" | CFMGSystemAdmin CFMGSystemUser |
/myportal/ | Select "o" | sop_contractor sop_resource_manager sop_restricted_user |
/op_portal/ | - | CTMGProviderAdmin |
/ibpmm/dashboard/ | - | CTMGProviderAdmin |
/CTMGApproverSelection/ | - | sop_contractor sop_resource_manager sop_restricted_user |
/CMDBConsole/ | - | - |
Creating the Business System Setup File
With the Interstage Management Console, create the business system build file using the following procedure:
Start the Interstage Management Console.
Refer to 3.1.3.2.1 Creating the Management Server Web Server for information on the Interstage Management Console start procedure.
Create the business system build file.
Click System >> Security >> Single Sign-on >> Authentication Infrastructure >> Business system setup file tab.
Set Business System Information as shown below, enter a password (6 or more characters), then click Download.
Settings item | Settings value |
|---|---|
Public URL | http://Management Server FQDN:80 |
Linkage with Interstage Portalworks? | No |
Save the downloaded file.
Registering the Management Server
With the Interstage Management Console, add the Interstage Single Sign-On Business Server to the Management Server using the following procedure:
Start the Interstage Management Console.
Refer to 3.1.3.2.1 Creating the Management Server Web Server for information on the Interstage Management Console start procedure.
Set the business system build file and password.
Click System >> Security >> Single Sign-on >> Business System >> Addition of Business server tab.
Set the business system build file and password that were downloaded in "Creating the Business System Setup File" in Business System Setup File and Password of file, then click Next.
Add the Interstage Single Sign-On Business Server to the Management Server.
Set the following simple settings values, then click the Add button.
Settings item | Settings value |
|---|---|
Business system Name | Business001 |
Web Server used | Fjapache |
Host for Web server used | Main host: 80 |
When updating Access Control Information? | Execute when Business server is started |
Use Single Sign-On JavaAPI? | Yes |
Change the environment settings.
Click System >> Security >> Single Sign-on >> Business system >> Business system Name. Business system Name is the business system name that was specified in step 3.
Open the environment settings tab, click Detailed Settings >> Show, change the environment settings as shown below.
Settings item | Settings value |
|---|---|
Enable Client IP Address Check? | No |
Notify User Information? | Yes |
Notify Sign-off URL? | Yes |
Check the values that were set.
Once the above settings are complete, click the Update button.
Suppressing Contents Cache
Activate the Web browser cache settings using the following procedure:
Start the Interstage Management Console.
Refer to 3.1.3.2.1 Creating the Management Server Web Server for information on the Interstage Management Console start procedure.
Stop the Web server.
With the Interstage Management Console, select System >> Services >> Web Server >> FJapache to display FJapache:Status, then click the Stop button.
Update the Business Server environment definition file.
Using an editor, update the Business Server environment definition file.
The Business Server environment definition file storage location and file name are as follows:
[Windows]
<Interstage Application Server installation folder>\F3FMsso\ssoatzag\conf\ssoatzag.conf[Linux]
/etc/opt/FJSVssoaz/conf/ssoatzag.conf
Edit the above file as follows:
Add "http-cache-cntl=NO" to the line that follows "business-system-name = <business system name that was specified in 3.1.3.3.3 Registering the Management Server>".
In the execution example below, "Business001" has been used for the business system name.
ServerPort=80
(snip)
business-system-name=Business001
http-cache-cntl=NOStart the Web server.
Select System >> Services >> Web Server >> FJapache to display FJapache:Status, then click the Start button.