Note
Notes concerning the startup of web console
Please do not start multiple web consoles on one PC.
Start Log Viewer
Start the web console through any of the following methods:
In a 2-level structure: Please connect to the Management Server.
Select [Programs] - [Systemwalker Desktop Keeper] - [Server] - [Desktop Keeper Main Menu] from the [Start] menu of Management Server.
Specify the address of browser to “http://host name or IP address of management server/DTK/index.html”
If IIS port number has been changed, specify as follows:
http:// IP address: port number/DTK/index.html
In a 3-level structure: Please connect to the Master Management Server.
Select [Programs] - [Systemwalker Desktop Keeper] - [Server] - [Desktop Keeper Main Menu] from the [Start] menu of Master Management Server.
Specify the address of browser to “http://host name or IP address of master management server/DTK/index.html
If IIS port number has been changed, specify as follows:
http:// IP address: port number/DTK/index.html
→The [Login] window is displayed.
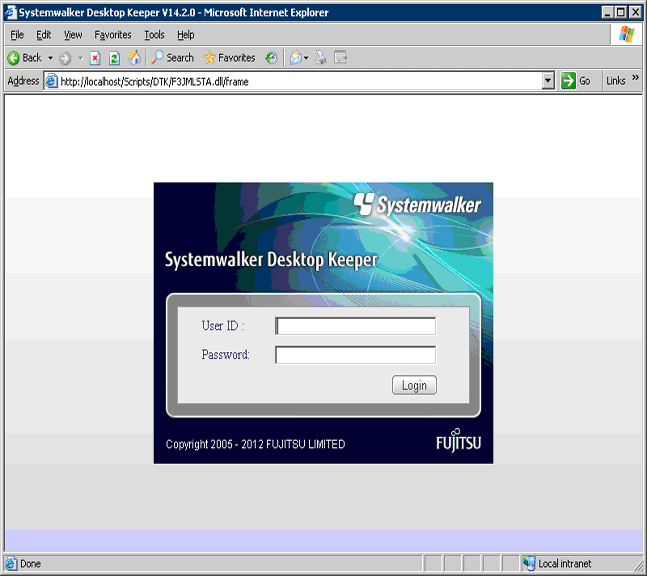
Enter the following information and click the [Login] button.
The system administrator and department administrator log in the same way.
When performing a single sign-on link with Systemwalker Desktop Patrol, the entered User ID should be case-sensitive.
[User ID]: [User ID] set in the [Administrator Information Settings] window of the Server Settings Tool.
[Password]: [Password] set in the [Administrator information settings] window of the Server Settings Tool
It is recommended to change the password regularly. For details on how to do so, please refer to “Change password”.
→ The status window is displayed.
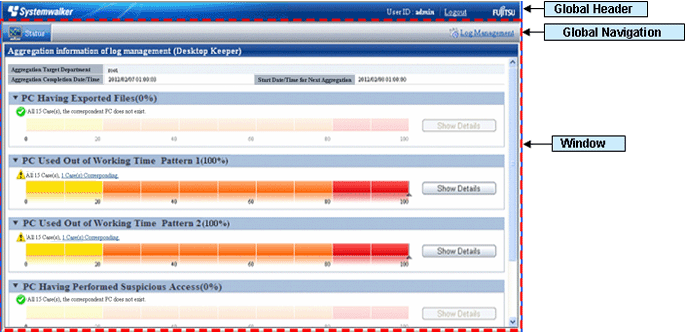
Select [Log Management] from Global Navigation.
→Log Viewer is started, and the [CT Operation Log] window is displayed.
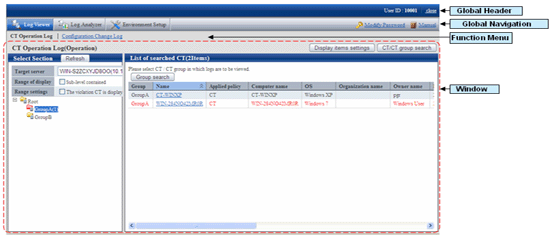
Global Header
User ID: The user ID for login is displayed.
close: Close the Log Viewer window.
Global Navigation
Log Viewer: The Log Viewer window is displayed.
Log Analyzer: The Log Analyzer window is displayed.
Environment Setup: The option window (the window used to set aggregation condition on which the aggregation results displayed in the status window are based).
Modify Password: Change the password for starting the Web Window. (Please refer to “Change password” for how to change password)
Manual: Display the manual.
Function Menu
CT Operation Log: Search and display CT Operation Logs.
Configuration Change Log: Search and display Configuration Change Logs.
Contents
[Display items settings]: The selection of visible columns in [List of searched CT] and the display sequence can be modified. Please refer to “Set visible columns in [List of searched CT] ” for details.
[CT/CT group search]: The [CT operation log(Operation) - CT/CT group search] window is displayed. Search after setting the conditions if the location of client (CT) and CT group under Management Server is not known.
[Select Section]: The server name next to the root directory and its subordinate CT groups are displayed.
[Refresh]: Import the latest tree structure and CT list information of server selected from [Target Server].
[Target server]: Select the Management Server or Master Management Server to be connected with.
[Range of display]
If the checkbox is selected, the selected CT group and all its subordinate CTs will be displayed in [List of searched CT].
If the checkbox is not selected, all CTs directly under the selected CT group will be displayed in [List of searched CT].
[Range settings]
When this item is selected, only the client (CT) that generates violation logs will be displayed in [List of searched CT]. When the client (CT) under the group has already been displayed in [List of searched CT], after this item is selected, it will change to display only the client (CT) that generates violation logs.
When this item is not selected, client (CT0 under the group will be displayed in [List of searched CT].
Icons of CT Group Tree
Icons displayed in the CT Group tree vary depending on the different users log in to Log Viewer.
The following describes the conditions for displaying each icon.
User logs on to Log Viewer | Displayed icon | Meaning of icon |
|---|---|---|
System administrator |
| All groups will be displayed with identical icons when the system administrator logs on to the Log Viewer. This indicates the group in which “Display the group or client (CT) that has generated violation logs in red” is not set; or no violation log has been generated though settings have been performed. |
| This indicates the group in which “Display the group or client (CT) that has generated violation logs in red” has been set and violation log has been generated in the set time. | |
| This indicates the “Deleted CT” group. | |
| This indicates the “Not Configured” group. | |
Department administrator |
| This indicates if a group has been set as the department administrator. |
| This indicates if a group has not been set as the department administrator. | |
| This indicates the group in which Display the group or client (CT) that has generated violation logs in red” has been set and in which a violation log has been generated in the set time. | |
| This indicates that the CT group that has been set as the department administrator exists in the sub-group of this group. |
Domain display
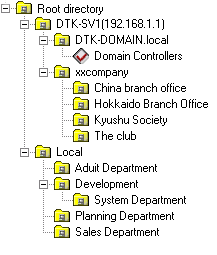
When linking with Active Directory, the domain name is always displayed together with the server name.
[Example of domain displayed during link with Active Directory]
[List of searched CT]: The client (CT) belongs to the selected group is displayed. The item to be displayed can be selected. For the method, please refer to “Set visible columns in [List of searched CT]
Set visible columns in [List of searched CT]
Click the [Display items settings] button in the [CT Operation Log] window.
→ The [Display items settings] window is displayed.
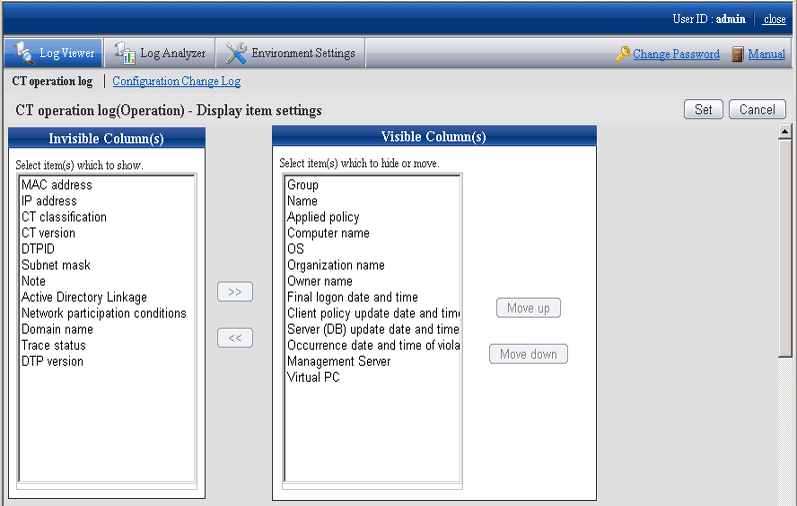
[Invisible Column(s)]: Items that will not be displayed in “List of searched CT”.
[Visible Column(s)]: Items that will be displayed in “List of searched CT”. The initial value will be displayed as the items with * in the following table.
In addition, the display sequence can be modified. Items are displayed from left to right in “List of searched CT” by names in the order from top to bottom. Item description is as follows.
Item Name | Description |
|---|---|
[Name] (*) | The name that can be added to client (CT), initial value is the computer name. |
[Group] (*) | This is the group to which the client (CT) belongs. |
[Applied policy] (*) | This is the policy that is applied. [CT]: This indicates the CT policy that has been set. |
[Computer name] (*) | This is the computer name of client (CT). |
[MAC address] | This is the MAC address of client (CT). |
[IP address] | This is the IP address of client (CT) |
[OS] (*) | This is the OS name of client (CT). |
[CT classification] | This is displayed as [SE] (for Standard Edition versions prior to V13.2.0, it is displayed as [SE]; for Base Edition, it is displayed with blank) |
[CT version] | This is the version of the client (CT) of Systemwalker Desktop Keeper that is installed. In addition, for correspondence of product version/edition, please refer to “CT version” of “Systemwalker Desktop Keeper Reference Manual”. |
[DTPID] | This is “User ID (+) PC Name” of Systemwalker Desktop Patrol Client (CT) Thi will be displayed when both Systemwalker Desktop Keeper Client (CT) and Systemwalker Desktop Patrol Client (CT) are installed on the same PC. |
[Organization name] (*) | This is the organization name set in the OS of client (CT). |
[Owner name] (*) | This is the owner name set in the OS of client (CT). |
[Subnet mask] | Subnet mask set up in the client (CT) network. |
[Active Directory Linkage] | This shows whether the client imports information by Active Directory Linkage.
|
[Network participation conditions] | Network participation situation of the client (CT) is displayed.
|
[Domain name] | The name of domain to which the client belongs is displayed. |
[Final logon date and time] (*) | The client (CT) communicates with Master Management Server or Management Server during its startup. This is the final date and time when the server performs the following tasks on the client during communication,
|
[Client policy update date and time] (*) | This is the final date and time when the Master Management Server or Management Server sends CT policy to the client (CT).
|
[Server (DB) update date and time] (*) | This is the latest date and time when the Management Server or Master Management Server updates the policy of client (CT) and reflects it to the database (including immediate update). |
[Note] | This is the information input when updating policy of the client (CT). |
[DTP version] | This is the version of Systemwalker Desktop Patrol Client installed in PC. |
[Trace status] | This is the setting of trace collection in client (CT).
|
[Occurrence date and time of violation log] (*) | This is the date and time when violation logs are collected on client (CT). |
[Management Server] | The computer name of the management server to which the client belongs. |
[Virtual PC] | The following icons will be displayed if the client (CT) is installed in a virtual environment:
|
*) Items displayed as initial value.
Set visible columns and display sequence and click the [Set] button.
Display the “Deleted CT” group in [Select Department] display domain
To view the logs of a deleted (moved to “Deleted CT” group) client (CT), the “Deleted CT” group needs to be displayed in the [Select Department] display domain.
Nobody but the system administrator can Perform this operation.
Click the [Display items settings] button in the [CT Operation Log] window.
→The following window is displayed.

Click the [Display] button in [Display deleted CT group] of [Department display settings].
Click the [Set] button.
When linking with Active Directory, it will be displayed as the last group under Local group.
When Active Directory Linkage is not performed, it will be displayed as the last group under the server.
The method of viewing and searching the logs of a client (CT) that belongs to the “Deleted CT” group is the same as that of viewing and searching logs of client (CT) of other CT group.
Display the group or client (CT) that has generated violation logs in red
After [Violation CT display settings] has been performed, the CT group in which violation logs have occurred will be displayed in red when Log Viewer is started.
After selecting the CT group that is displayed in red, the column of the CT where violation log occurred will be displayed in red in [List of searched CT].
After clicking the [Select CT] button, the column of CT with violation log occurred will be displayed in red in [Select CT]. In addition, [Number of violation logs] will also be displayed in the visible columns.
Click the [Display items settings] button in the [CT Operation Log] window.
→ The following window is displayed.

Item description is as follows.
Item Name | Description |
|---|---|
[Display violation CT] | Set the group to which the client (CT) that has generated violation log belongs in the “Select Department” window and the method of displaying the client (CT) that has generated a violation log.
Initial value: [Not display] is select. |
[Violation range of display] | Set whether to display the situation in which the client (CT) that has generated the violation log exists in a certain range of time prior to the startup date of Log Viewer in red.
|
[The specified date] | Setting can be performed when [Within the specified date] is selected from [Violation range of display]. |
Set each item and click the [Set] button.

Change the database to be viewed
Note
About department administrator
The department administrator cannot view the log viewing database.
Select the database to view operation logs.
Click the [Display items settings] button in the [CT Operation Log] window.
→The following window is displayed.
A Item Description Item is as follows.
Item Name | Description |
|---|---|
[Viewing database settings] | Set the database to be viewed by Log Viewer
Initial value: Select [Operation database]. Setup is not possible if the Log viewing database has not been created |
Select the database to be viewed and click the [Set] button.
Modify search target
Set “Search the terminals that are specified as the search range of operation logs only”, or “Also search the connection source terminal and connection target terminal of specified terminal”.
Click the [Display items settings] button in the [CT Operation Log] window.
→The following window is displayed.
A Item description is as follows.
Item Name | Description |
|---|---|
[Log search settings] | Set the search range of operation log.
Initial value: [Logs of the specified terminal are searched only] is selected |
Select the database to be viewed and click the [Set] button.
Change password
Select [Modify Password] of Global Navigation.
→The [Modify Password] window is displayed.
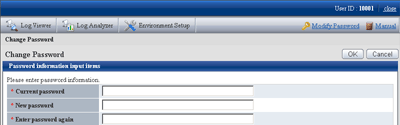
Enter the following information, and click the [OK] button.
[Current password]: Enter the password that is currently used.
[New password]: Enter the new password with single-byte alphanumeric characters or symbols (1-32 characters).
However, “&”, “\”, “:”, “?”, “””, “~”, “^”, “’”, “<”, “>”, “|” and space are not allowed. In addition, the password is case-sensitive.
[Enter password again]: Enter the new password again.