It describes how to set the auditing indicator to be used in security auditing.
In addition, it is not required to set auditing indicator when the recommended auditing indicator provided by Systemwalker Desktop Patrol is not to be modified.
The procedure is as follow.
Log on to the AC menu.
Click [Setup of Report].
→The following window will be displayed.
Click the [Security Auditing] button, and the [Security Audit Set] window will be displayed.
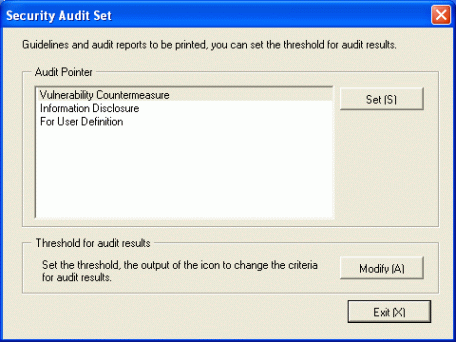
Select the [Audit Pointer] to be modified, and click the [Set] button of [Audit Pointer].
To newly define the auditing indicator, select [For User Definition]. To edit the recommended indicator, select [Information Disclosure] or [Vulnerability Countermeasure].
In addition, the setting of each auditing item is selected by combination of operation method and environment.
→ The [Audit Pointer Setting] window will be displayed.
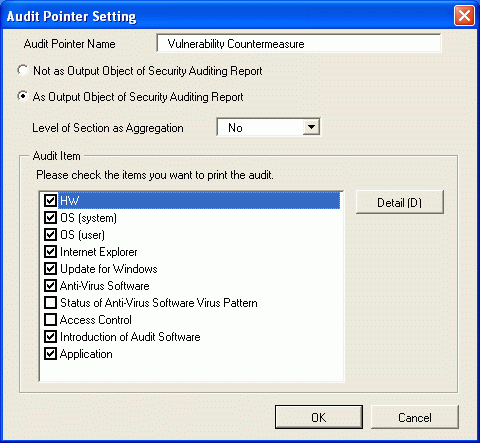
Set the following information, and click the [OK] button.
Item Name | Description | |
|---|---|---|
[Audit Pointer Name] | Set the name of auditing indicator. Up to 32 characters of single-byte alphanumeric characters, single-byte symbols and malti-byte characters can be set. | |
[Not as Output Object of Security Auditing Report ] | Select when not to output security auditing report. | |
[As Output Object of Security Auditing Report] | Select to output security auditing report. | |
[Level of Section as Aggregation] (Note 1) | Not specify or select from level 1 to level 9. | |
[Audit Item] | [HW] | Select it when BIOS status is included in the output item of security auditing report. |
[OS (System)] | Select it when status of OS settings related to the system such as logon status and settings of automatic update are included in the output item of security auditing report. | |
[OS (User)] | Select it when status of OS settings related to use such as screen saver is included in the output item of security auditing report. | |
[Internet Explorer] | Select it when the setting status of security zone status of Internet Explorer is included in the output item of security auditing report. | |
[Windows Update Program] (Note 2) | Select it when the setting status of patch installation such as OS is included in the output item of security auditing report. | |
[Anti-Virus Software] | Select it when the setting status of installation status of anti-virus software and real-time search .etc is included in the output item of security auditing report. | |
[Status of Anti-Virus Software Virus Pattern] | Select it when the application status of virus patter is included in the output item of security auditing report. | |
[Access Control] | Select it when the application status of prohibition operation is included in the output item of security auditing report. | |
[Introduction of Audit Software] | Select it when the setting status of auditing software installation status is included in the output item of security auditing report. | |
[Application] | Select it when the setting status of application such as Google Desktop function and firewall settings are included in the output item of security auditing report. | |
[Detail] | Display the window to set whether to output the auditing for each item. For setting items, please refer to “Items of auditing indicator”. | |
Note 1) It is the section level when aggregating the best section and worst section.
In the following example, when the second level is specified as the section level, the unit displayed as section is as follows.
Upper-level section
General section (including subordinate sections)
In the “General Section” of the second level, the PC under the “Business Division”, “Finance Division”, “Administrative Affairs Division” and “General Affairs Division” will be aggregated and the best section and worst section will be judged in the aggregation content.
In addition, for the “Software Unit”, “Hardware Unit” and “Management Unit” in the higher level than the second level, it will be aggregated as one section of “Upper-level Section”, and the best section and worst section will be judged in the “Upper-level Section”.
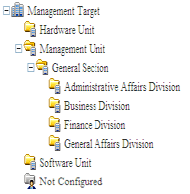
In addition, if no level has been set, all sections will be targets of best section and worst section. In addition, for PC without configuration, no judgment of best section and worst section will be included.
Note 2) Select the patch installation status using the patch distribution information managed by Systemwalker Desktop Patrol. In addition, For the patch to be selected, it is required to select automatic patch installation in the [Main Menu] - [Distribution Software] window. For the patch without selection of automatic patch installation, it will not be selected.
If automatic patch installation is not executed, please set “Not as Auditing Target” in the [Details] window.
If all patches included in the patch distribution information are installed to PC, this PC will be processed as the PC whose patch installation is OK. Even if one patch is not installed, it will be processed as the PC of NG. The patch is not installed can be confirmed from the window of Systemwalker Desktop Patrol.
For information on how to confirm the patch not installed, please refer to “3.2.1 View Inventory Information”.
→ To modify the output standard of each auditing item, select each auditing item and click the [Details] button. The following is the window when [Hardware] is selected.
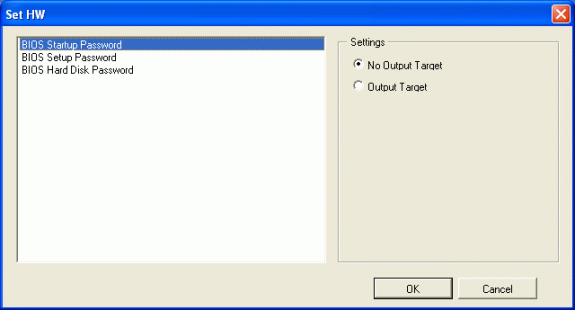
Set the following information, and click the [OK] button.
Item Name | Description | |
|---|---|---|
[BIOS Startup Password] | For the startup password of BIOS, select when setting the output to report. | |
[BIOS Setup Password] | For the setting password of BIOS, select when setting the output to report. | |
[BIOS Hard Disk Password] | For the hard disk password of BIOS, select when setting the output to report. | |
Settings (Note) | [No Output Target] | Select when the selected items are not taken as output target. |
[Output Target] | Select when the selected items are taken as output target. | |
[Items Judged as OK] | For [Unable to Collect], [Not Set] and [Has been Set],l select the items that are judged as OK. | |
Note) Setting of judgment standard can be set for each auditing item of [Access Control Status].
Set the auditing items apart from [Hardware] in the same way.
In addition, [Item Name] displayed in the setting window may vary depending on the item of auditing indicator. For other auditing items, please refer to “Items of auditing indicator”.
To modify the threshold value of auditing result, click the [Set] button of [Threshold setting of audit results].
In the [Threshold setting of audit results] window, the output standard of icon can be modified.
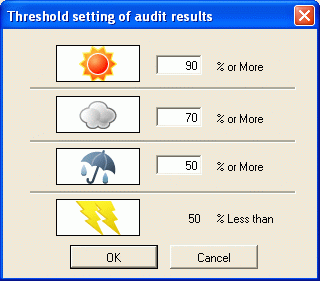
Set the following information, and click the [OK] button.
Item Name | Description |
|---|---|
Threshold value of [Sunny] icon | Only single-byte number can be set. The initial value is over 90%. |
Threshold value of [Overcast] icon | Only single-byte number can be set. The initial value is over 70%. Set a value that is smaller than the threshold value of [Sunny]. |
Threshold value of [Rainy] icon | Only single-byte number can be set. The initial value is over 50%. Set a value that is smaller than the threshold value of [Overcast] |
Save the icon to the following folder and the icon can be modified.
Registration folder of image file
AC installation directory\images |
Image file/file name
Image File | File Name |
| best.bmp |
| better.bmp |
| bad.bmp |
| worse.bmp |
Size/Format of image file
Size/Format | |
Width | 82 pixels (Note) |
Height | 36 pixels (Note) |
Format | bmp format |
Note) when the image file of a different size is used, displayed as the above size.
Point
Modification of image file
The modification of image file is only effective in the modified AC terminal. To unify image files in all AC terminals, please replace the image file of all AC terminals.
There are following methods to restore image file.
Before modification, when avoiding the icon of product, please configure the avoided product icon to the registration folder again.
Before modification, when the icon of product is not avoided, please delete the icon after modification and re-install the AC of this product. (it is not need to uninstall since it is overwriting installation)
When the image file is displayed as blank, reasons such as files being damaged or insufficient should be considered. When it is displayed as blank, please check the saving target of icon and restore through preparing a new image or restoring the above image file.
Items of auditing indicator
It describes the items of monitoring indicator.
For content of each item, please refer to “3.2.5 View Security Information”.
For the following items, whether the auditing report will be output as output target of auditing report can be set in each item unit.
HW (Note)
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
BIOS Startup Password | Not as output object | As output object |
BIOS Setup Password | Not as output object | As output object |
BIOS Hard Disk Password | Not as output object | As output object |
Note) In case of virtual PC, since the hardware is “Unable to Audit”, the “Hardware Type” will be displayed as ”Virtual PC, and “Hardware” will be displayed as [-] in the report.
OS (System)
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Automatic Logon | Not as output object | As output object |
Welcome To Use | Not as output object | Not as output object |
Last User Name | Not as output object | Not as output object |
Security of Guest Account | Not as output object | As output object |
Settings of Automatic Update | Not as output object | Not as output object |
User Account Control (UAC) | Not as output object | Not as output object |
Insecure Shared Folder | Not as output object | As output object |
Require a Password on Wakeup | Not as output object | Not as output object |
Set Complicated Password Required | Not as output object | Not as output object |
OS (User)
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Screen Saver | Not as output object | As output object |
Screen Saver Password | Not as output object | As output object |
Password of Logon User | Not as output object | As output object |
Internet Explorer
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Internet Zone | As output object | As output object |
Introduction of Audit Software
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Check whether Systemwalker Desktop Patrol CT is installed (whether inventory information is collected) | As output object | As output object |
Windows Update Program
Setting Item | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Check the patch installation status using the patch distribution information managed by Systemwalker Desktop Patrol | As output object | As output object |
Anti-virus Software
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Installation of Anti-virus Software | As output object | As output object |
Real-time Scan Status of Anti-virus Software | As output object | As output object |
Scheduled Scan Status of Anti-virus Software | Not as output object | Not as output object |
Scan Scope of Anti-virus Software | Not as output object | Not as output object |
Status of Anti-virus Software Virus Pattern
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Check whether the latest virus pattern has been applied | As output object | As output object |
Access Control
It can be used after Systemwalker Desktop KeeperV13.0.0 or later has been installed.
Information | Content | Initial Value of Recommended Auditing Indicator | |
|---|---|---|---|
Vulnerability Countermeasure | Information Disclosure | ||
File Export Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Normal export | |||
Encrypted export | |||
Unable to export | |||
Printing Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
PrintScreen Key Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Logon Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Application Startup Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
E-mail File Attachment Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Allow encrypted file only | |||
Prohibit specified extensions only | |||
Allow specified extensions only | |||
Application Startup Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Application Termination Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Window Title Obtaining Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
E-mail Sending Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Command operaton log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Device Configuration Change Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Printing operation log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
File Export Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
File Operation Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Logon/Logoff Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
External Application log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
PrintScreen Key Operation log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
File Export Utility | Unable to collect | Not as output object | Not as output object |
Normal export | |||
Encrypted export | |||
Unable to export | |||
Reading prohibition of removable drive | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
USB Device Individual Identification | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Web Operation Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
FTP Operation Log | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Confirmation of Recipient Address | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
URL Access Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
FTP Server Connection Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Web Download Prohibition | Unable to collect | Not as output object | Not as output object |
No | |||
Yes | |||
Application
Information | Initial Value of Recommended Auditing Indicator | |
|---|---|---|
Vulnerability Countermeasure | Information Disclosure | |
Firewall | As output object | As output object |
Adoption of Encryption software | Not as output object | Not as output object |
Google Desktop [Search Across Computers] | Not as output object | As output object |
Detection of Banned Software Status | Not as output object | Not as output object |
For the settings of whether to perform auditing of each auditing items, please refer to “4.2.2.1 Set the Auditing Items of Security Settings”.
In addition, the auditing result output in the security auditing report is consistent with the auditing result in the diagnosis result of operation settings (security auditing). For judgment method, please refer to “Diagnosis Result” of “4.3.1.2 Structure of Security Diagnosis Result Window”.
For PC imported through linking with other products of Systemwalker Desktop Patrol, the auditing result is as follows.
Auditing items that are judged as OK
[Import Auditing Software]
[Windows Update Program]
Auditing items that are judged as NG
[Anti-Virus Software]
[Virus Pattern Status of Anti-virus Software]
Items except the above
Judged as OK.