The following will define the network configuration required by the system.
For each server, choose the network interfaces to use for the following purposes.
Network interface assigned to the admin LAN
Network interface assigned to the iSCSI LAN (Only when iSCSI is used)
Network interface assigned to the public LAN
Choose the following settings to fit the system environment.
Network redundancy settings
Network configuration of LAN switch blades (when using PRIMERGY BX servers)
Refer to "Example of VLAN network configuration (with PRIMERGY BX600)" and the description below to define a network configuration.
Admin LAN
The admin LAN is the network used by the manager to communicate with agents on the managed servers and other managed devices.
The number of network interfaces required for the admin server and managed servers can be determined as follows.
For a non-redundant configuration: 1 network interface.
For a redundant configuration: 2 network interfaces.
If HBA address rename is used, two network interfaces (named NIC1 and NIC2) are required regardless of network redundancy.
For details, refer to "Required Network Configuration when Using HBA Address Rename".
For PRIMERGY managed servers:
For a non-redundant configuration
NIC1 (Index1)
For a redundant configuration, or when using HBA address rename
NIC1 (Index1) and NIC2 (Index2)
For PRIMERGY Partition Model managed servers:
For a non-redundant configuration
The smallest NIC number of the GSPB allocated to a partition
For a redundant configuration, or when using HBA address rename
The smallest and the second smallest NIC number of the GSPB allocated to a partition
Set up routing to enable communications from the admin client to the admin server. It is also suggested to allow communications from the admin client to managed servers, server management units, and switch blades. Such routing configuration is necessary to allow access to ServerView and other management consoles.
There is no need to set up routing if the admin client is already located within the admin LAN.
Note
When using blade servers, connecting the management blade to a LAN switch blade will make the management blade inaccessible in the event of a LAN switch blade failure. Therefore, it is recommended that the management blade be connected to a LAN switch outside the chassis.
Do not place a DHCP server or a PXE server on the admin LAN.
Do not configure multiple IP addresses for network interfaces used on the admin LAN.
When a cloning image is deployed to multiple servers, IGMP Snooping should be enabled on admin LAN switches. If IGMP Snooping is not enabled, transfer performance may deteriorate when ports with different speeds co-exist in the same network, or multiple image operations are run simultaneously.
For PRIMERGY BX900 LAN switch blades operating in IBP mode, the admin LAN should not be included in the service LAN or its port group configuration.
iSCSI LAN
The iSCSI LAN is designed for communication between managed servers and storage devices.
The number of network interfaces required for managed servers is as follows:
For a non-redundant configuration: 1 network interface.
For a redundant configuration: 2 network interfaces.
It is necessary to establish this LAN separately from the admin LAN and public LAN by using NIC 3 (Index 3) or later.
Note
Keep the following points regarding the iSCSI LAN in mind.
Tagged VLANs cannot be used.
Teaming is not available.
Use is not possible in cluster configurations.
The STP of connected switches must be turned off.
DHCP cannot be used for iSCSI LAN IP addresses. Fixed IP addresses should be configured.
Refer to the hardware manual for details on other points.
Public LAN
The public LAN is the network used by managed servers to provide services over internal or external networks (such as intranets or the internet).
Use NIC3 or higher (Index3 or higher) on managed servers:
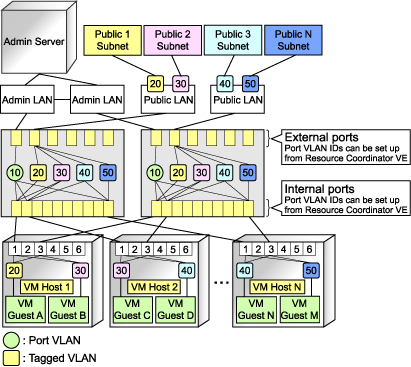
A network interface can be shared between multiple public LANs by using a redundant configuration and tagged VLAN.
Information
For blade servers, depending on the model of LAN switch used in the same chassis, the network interfaces whose index numbers are between 3 and 6 (NIC3 - NIC6) cannot be used.
Instead, it is possible to use two more interfaces for the public LAN by adding expansion cards (NIC7 and NIC8) and a LAN switch blade, or by sharing the NIC1 and NIC2 interfaces with the admin LAN.
All network interfaces shared between the admin and public LANs should be configured with tagged VLAN IDs.
Network configuration of LAN switch blades (when using PRIMERGY BX servers)
In a blade system environment, multiple subnets can be consolidated onto LAN switch blades by using VLANs.
For PRIMERGY BX900 LAN switch blades operating in IBP mode, the above can also be achieved by using port group settings instead of VLAN settings.
Each port of a LAN switch blade can be set with VLAN IDs.
Only those ports set with a same VLAN ID can communicate with each other.
Setting up different VLAN IDs then results in multiple subnets (one per VLAN ID) co-existing within the same switch.
Define the VLANs to set on both the internal (blade server side) and external ports of each LAN switch blade.
Internal ports
For the internal ports connected to admin LAN network interfaces (see "Admin LAN"), only port VLAN is supported. Be sure to configure those ports with port VLAN IDs.
For the internal ports connected to public LAN network interfaces (see "Public LAN"), be sure to assign different VLAN IDs (port or tagged VLAN) for each subnet, while avoiding the VLAN ID "1" (default VLAN ID).
Using tagged VLANs on LAN switch ports also requires configuring the network interfaces of managed servers with tagged VLANs. As Resource Coordinator VE cannot set tagged VLANs to network interfaces on managed servers, this must be done manually.
External ports
Choose the LAN switch blade ports to connect to external LAN switches, and the VLAN IDs to use for both the admin and public LANs.
When choosing a tagged VLAN configuration, the VLAN ID chosen for a LAN switch blade's external port must be the same as that used on its adjacent port on an external LAN switch.
Note
To change the VLAN ID for the admin LAN, perform the following.
Enable communications between the admin server and the LAN switch blade.
Manually change the following two settings.
- Change the VLAN ID of the external port(s) used for the admin LAN.
- Change the VLAN ID used by the admin IP of the LAN switch blade.
Change the VLAN ID used by the managed server on the admin LAN.
VLAN settings for LAN switch blades are not included in cloning images. Configure VLAN settings for the target servers before deploying a cloning image.
VLANs cannot be set from the RC console on ports set with any of the following:
Link state group
Backup port
Deactivated (depends on LAN switch blade model)
Choose VLAN IDs as well as VLAN types (port or tagged VLAN) for the ports on LAN switch blades that are connected to each server blade's network interfaces. For each of a physical server's network interfaces, choose:
Physical server name
NIC index
VLAN ID
VLAN type (port or tagged VLAN)
Note
On servers, operating systems associate each physical network interface with a connection name (Local area connection X in windows and ethX in Linux).
If more than one network interface is installed, the index numbers (X) displayed in their connection name may differ from their physically-bound index (defined by each interface's physical mount order).
The relations between physically-bound indexes and displayed connection names can be confirmed using OS-provided commands or tools.
For details refer to network interface manuals.
Also note that Resource Coordinator VE uses the physical index of a network interface (based on physical mount order).
[Windows/Hyper-V]
When using the backup, restore, or cloning functions, enable the managed server's NetBIOS over TCP/IP.
Note that the managed server should be restarted after enabling NetBIOS over TCP/IP.
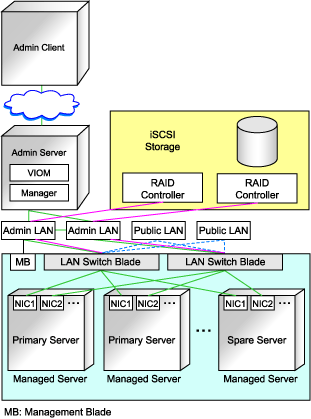
Example of VLAN network configuration (with PRIMERGY BX600)
Figure 3.1 With Port VLANs
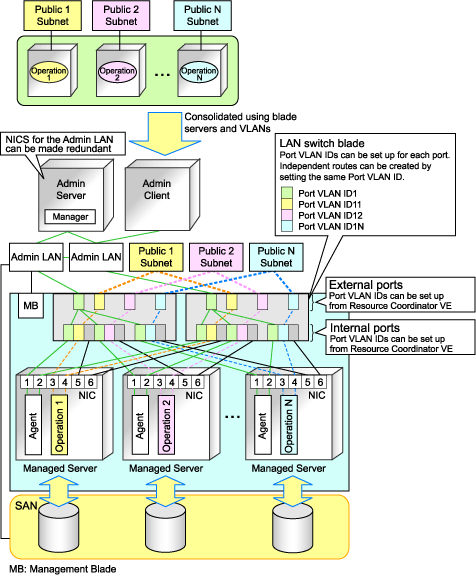
Figure 3.2 With Tagged VLANs
Information
It is recommended that a dedicated admin LAN is installed as shown in "Example of VLAN network configuration (with PRIMERGY BX600)".
If you need to use the following functions, a dedicated admin LAN is required in order to allocate admin IP addresses to the managed servers using the DHCP server included with Resource Coordinator VE.
Backup and restore
Collection and deployment of cloning images
HBA address rename
In a configuration using a LAN switch blade, a VLAN has to be configured if the LAN switch blade is shared by an admin LAN and a public LAN where a dedicated admin LAN is required.
Required Network Configuration when Using HBA Address Rename
At startup a server set with HBA address rename needs to communicate with the Resource Coordinator VE manager. To enable startup of managed servers even when the manager is stopped, Resource Coordinator VE should be set according to one of the following configurations.
Manager cluster configuration with admin LAN redundancy.
For details, refer to "Appendix B Manager Cluster Operation Settings and Deletion" in the "ServerView Resource Coordinator VE Installation Guide".
Dedicated HBA address rename server
This section describes the network configuration that is required for an environment with a dedicated HBA address rename server.
For details about the HBA address rename setup service, refer to "6.2.2.1 Settings for the HBA address rename setup service".
This service uses NIC2 (Index2). Connect NIC2 to the admin LAN.
This service uses NIC2 (Index2). Connect NIC2 to the admin LAN.
This service periodically obtains information about managed servers from the admin server and operates using this information. For this reason, it should be installed on a server that can be left active all the time.
There must be two LAN cables between LAN switches (cascade connection) on the admin server and on the managed server.
Note
The HBA address rename setup service cannot operate on the same server as ServerView Deployment Manager, or on a server where any other DHCP or PXE service is running.
The following diagram shows an example of how the HBA address rename setup service can be configured.
Figure 3.3 Sample configuration showing the HBA address rename setup service (with PRIMERGY BX600)
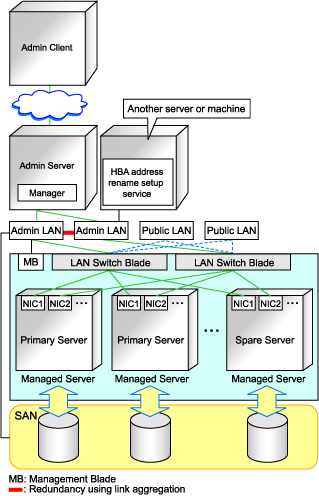
Connections between LAN switches on the admin LAN can be made redundant using link aggregation.
Connect the NIC2 (Index2) to the admin LAN.
Configure the HBA address rename setup service on a server connected to the admin LAN. This server must be different from the admin server.
Ensure that the server or personal computer that is used to operate the HBA address rename setup service is always on when the managed servers are active.
Network Configuration Required for VIOM Integration
When integrating with VIOM, the network configuration is defined by LAN switch blade and Intelligent Blade Panels.
For details, refer to the ServerView Virtual-IO Manager manual.
Refer to "6.1.1 Registering VIOM Settings" for details.
The following diagram shows an example of how the HBA address rename setup service can be configured.
Figure 3.4 Sample configuration for VIOM integration (on PRIMERGY BX600 servers using a SAN)
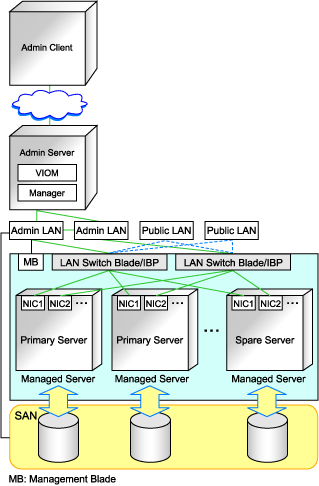
Figure 3.5 Sample configuration for VIOM integration (on PRIMERGY BX600 servers using iSCSI)
When using IBPs, the first IBP port should be connected to the admin LAN.
On the adjacent admin LAN switch, the Spanning Tree Protocol (STP) should be disabled on the port connected to that first IBP port.
Functions Provided by Resource Coordinator VE
Resource Coordinator VE provides the following VLAN and port group management functions for PRIMERGY BX LAN switch blades.
VLAN configuration
VLAN IDs of switch blade ports can be configured from the RC console.
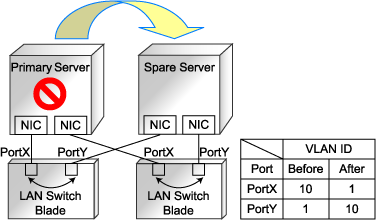
Exchange of VLAN IDs within each LAN switch blade in conjunction with server switchovers
When a server switchover occurs, the VLAN configuration of related LAN switch blades is automatically adjusted to preserve the network connectivity of applications.
VLAN IDs that were set on the LAN switch blade ports connected to the original server are exchanged with the VLAN IDs set on the ports connected to the spare server, as shown in "Figure 3.6 VLAN exchange mechanism for Auto-Recovery, server switchover and server failback".
Figure 3.6 VLAN exchange mechanism for Auto-Recovery, server switchover and server failback
Exchange of port groups in LAN switch blades during server switchovers.
When a server switchover occurs, the port group configuration of related LAN switch blades (if in IBP mode) is automatically adjusted to preserve the network connectivity of applications.
Note
The targets of such VLAN ID and port group exchanges are the LAN switch blade ports connected to the switched over manager servers. If the switched over servers are connected to different LAN switch blades (e.g. when switching over managed servers in different chassis) the external ports of those LAN switches should be set with the same VLAN or port group configuration, and the switch blades placed in the same network.