Systemwalker Operation Manager allows you to set any user who can access to the resources used by services/daemons and limits the Systemwalker Operation Manager users.
When the user definition is enabled, only the users registered in the swadmin group, users who belong to the Administrators group, and the superuser are enabled for the following:
Starting demand jobs (Job execution user)
Starting job nets that have the Job Execution Control attribute (Job execution user)
Using some of Jobscheduler command functions (User executing the command)
Using some of master scheduling command functions (User executing the command)
For a new installation of Systemwalker Operation Manager V17.0.0 or later, this definition is enabled by default. Refer to "How to disable the user restriction definition" for information on how to disable it.
Also, refer to "How to enable the user restriction definition" for information on how to enable the definition setting from a disabled status.
Note
You can use this option to limit the Systemwalker Operation Manager users only when you are using the file system of NTFS. You cannot use this option when you are using FAT, so disable the user restriction definition. [Windows]
How to disable the user restriction definition
Log in as system administrator (user belonging to the Administrators group or superuser).
Audit log file settings
[Windows]
Add "read" and "write" access rights for the Users group to the audit log output destination directory.
Delete the swadmin group from the access permission entries for the audit log output destination directory.
[UNIX]
Change the access right for the audit log output destination directory to 777, and the owner to the sys group. The following is an example where the audit log output destination directory is /var/opt/FJSVftlo/audit (by default):
# cd /var/opt/FJSVftlo # chmod 777 audit # chgrp sys audit |
Display the Define Operation Manager Shared Parameter window
The Define Operation Manager Shared Parameter window is displayed by clicking Shared parameter in the Systemwalker Operation Manager Environment Setup window.
Disable the user restriction definition
Clear the option Restrict so that only users included in the swadmin group can start demand jobs, start jobnet Job execution control attributes or use Jobscheduler command functions.
Restart the service/daemon
If OK is clicked in the Define Operation Manager Shared Parameter window, the restart confirmation dialog box is displayed. If OK is clicked in the dialog box, the following services or daemons restart as below:
[Windows]
Job Execution Control, Jobscheduler, Task Link services restart. If running multi-subsystem operation, all the subsystems and Task Link services restart.
[UNIX]
Job Execution Control and Jobscheduler daemons restart. If running multi-subsystem operation, all the subsystems restart.
How to enable the user restriction definition
The user restriction definition is inherited from the older version when upgrade installation is performed. Refer to the following procedure for information on how to enable the setting when it was disabled in the older version.
Creating the swadmin group
The swadmin group is required to restrict the users who can submit on-demand jobs, start job nets with the job execution control attribute or use the Jobscheduler commands.
Windows:
The swadmin group is created automatically during installation of the Systemwalker Operation Manager server. Once the swadmin group is created, it is NOT deleted even when the user restriction is canceled from the Define Operation Manager Shared Parameter window.
UNIX version:
The swadmin group is created automatically during installation of the Systemwalker Operation Manager server.
Register all of the users who are permitted to use the Jobscheduler and Job Execution Control commands in the swadmin group.
Configuration in the Define Operation Manager Shared Parameter window
Display the Define Operation Manager Shared Parameter window
The Define Operation Manager Shared Parameter window is displayed by clicking Shared parameter in the Systemwalker Operation Manager Environment Setup window.
Enable the user restrictions definition
Check the option Restrict so that only users included in the swadmin group can start demand jobs, start jobnet Job execution control attributes or use Jobscheduler command functions.
Restart the service/daemon
If OK is clicked in the Define Operation Manager Shared Parameter window, the restart confirmation dialog box is displayed. If OK is clicked in the dialog box, the following services or daemons restart as below:
[Windows]
Job Execution Control, Jobscheduler, Task Link services restart. If running multi-subsystem operation, all the subsystems and Task Link services restart.
[UNIX]
Job Execution Control and Jobscheduler daemons restart. If running multi-subsystem operation, all the subsystems restart.
Define Operation Manager Shared Parameter window
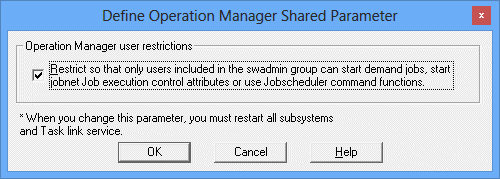
Specify this option to allow only users of swadmin group, those of Administrators group and the superuser to start on-demand jobs, start job nets having Job Execution Control attributes, and use Jobscheduler commands.
Protecting audit log files
To protect audit log files, make security definitions, and then use the following procedure to set up access rights for the output destination directory.
Note
Make these settings again if the output destination directory for audit log files is changed.
[Windows]
Log in as a user that belongs to the Administrators group.
Delete the "full control" access rights to the audit log output destination directory for the "Everyone" user group.
Add "full control" access rights to the audit log output destination directory for the "swadmin" group.
[UNIX]
Log in as a superuser.
Change the ownership rights to the audit log output destination directory to the "swadmin" group.
Example: # chgrp swadmin /var/opt/FJSVftlo/audit
Change the access rights to the audit log output destination directory.
Example: # chmod 770 /var/opt/FJSVftlo/audit
The commands in this example assume the default settings are used for the audit log output destination directory.
Notes on the user restriction definition
Access privileges to resources used by services/daemons
You can start some Systemwalker Operation Manager services only when you have access privileges to those resources. To do so, you must set the "full control" to the Administrators group to use the following resources of Systemwalker Operation Manager servers.
Installation destination directory and subordinate files specified during installation
Calendar information directory (Systemwalker Operation Manager installation directory\MpWalker.JM\mpjmcal\caldb)
Database directory of Jobscheduler (The initial value is the Systemwalker Operation Manager installation directory\MpWalker.JM\mpjobsch\jobdb) and subordinate files
Each daemon of Systemwalker Operation Manager uses the following resources, and the access privileges to those resources are set depending on the selection of the Operation Manager user restrictions check box option. Never change these access privileges. If changed, Systemwalker Operation Manager may not operate normally.
Solaris version and Linux version
- Resources under the system installation directory
- Resources under the database directory (/var/opt/package name)
HP-UX version and AIX version
- Resources under the system installation directory
The access privileges that differ from those specified during system installation may be used when you check the Operation Manager user restrictions option, and an error message may be output when you issue the pkgchk command.
When using the Extended User Management function [UNIX]
If the Extended User Management function is enabled, OS users that are associated with Operation Manager users will be subject to the definitions in "Define user restrictions".
If the Extended User Management function and the user restriction definition are enabled, the access rights are determined as below:
The associated OS user is checked for belongingness to the swadmin group.
If the belongingness to the swadmin group is confirmed, the OS user is checked for possession of the access privileges to projects.
When the OS user's access privileges is confirmed, he/she can use this option to submit on-demand jobs, start job nets having Job Execution Control attributes, and issue Jobscheduler commands.
Submitting jobs [Windows]
If the user restriction definition is enabled and a domain user belonging to the swadmin groups is specified as the following users below, the specified domain user needs to be registered in the Define Job Owner's Information window to submit a job normally.
Schedule jobs: The project owner or the execution user for the job
On-demand jobs: The login user
The qsub command: The execution user for the job
Job submission API: The execution user for the job