This section explains how to set up a cluster application.
You can use any one of the nodes of the cluster system for the settings described in this section.
Cluster application setup flow
The setup flow for a cluster application is explained for each topology, below.
For information on these topologies, see "2.3 Determining the Cluster System Operation Mode."
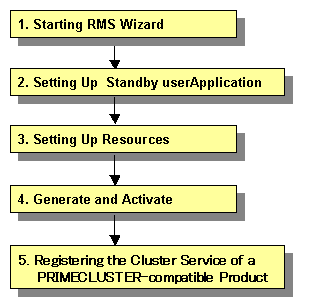
1) 1:1 standby for standby operation
Set up 1:1 standby for standby operation as follows.
2) Mutual standby for standby operation
Set up mutual standby for standby operation as follows.
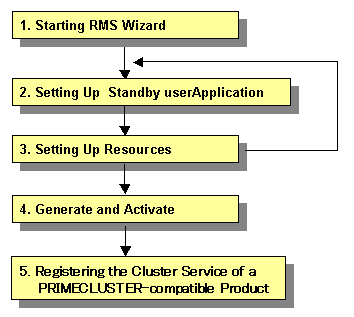
To create two cluster applications, repeat steps 2. to 3.
3) N:1 standby for standby operation
Set up N:1 standby for standby operation as follows.

To create two or more cluster applications, repeat steps 2. and 3.
Example) For 2:1 standby, repeat steps 2. and 3. two times, to create two cluster applications.
4) Cascaded standby operation
Set up cascaded standby operation as follows.

5) Priority transfer of standby operation
Set up the priority transfer of standby operation as follows.

To create two or more cascade cluster applications, repeat steps 2. and 3.
Establish an exclusive relationship between the cluster applications.
For details on exclusive relationships, see "6.7.7 Exclusive Relationships Between Cluster Applications."
Example) For priority transfer with two cascade cluster applications, repeat steps 2. and 3. two times to create two cascade cluster applications.
6) Scalable operation
Set up a scalable operation as follows.
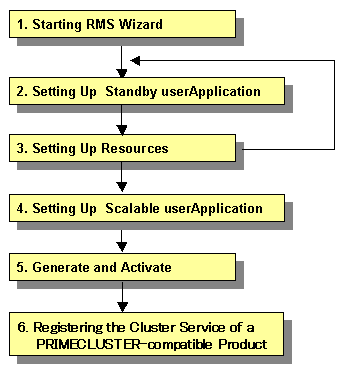
Before you create cluster applications as part of scalable operation, create cluster applications in standby operation that act as the constituent factors of the cluster applications in scalable operation. To create cluster applications in standby operation, repeat steps 2. to 3.
Example 1) For scalable operation with three nodes, repeat steps 2. and 3. three times to create three cluster applications of standby operation.
Example 2) For high-availability scalable 1:1 standby (standby operation), repeat steps 2. and 3. once to create 1:1 standby cluster applications.
See
After you finish setting up the cluster application, start the cluster applications. For instructions on starting the application, see "7.2.2.1 Starting a Cluster Application."
For instructions on changing a cluster application, see "10.3 Changing a Cluster Application." For instructions on deleting a cluster application, see "10.2 Deleting a Cluster Application."
For the setting contents of a cluster application depending on the operation, and notes on its setting, see "6.10 Setting Contents and Notes on Cluster Application."
Note
Set up the cluster application and resources based on the cluster application and resource information in "Setup (cluster application)"of PRIMECLUSTER Designsheets that was created in the design stage, and the sheet corresponding to each resource. If you need to change the cluster application after it is created, the designsheets are helpful. Make sure to create the designsheets before performing necessary operation.
You cannot share one resource with multiple userApplication.
Generate and Activate process fail if RMS is running. Using Cluster Admin or hvdisp, you need to confirm that RMS has not started before creating a cluster application. If RMS has already started, stop RMS from Cluster Admin or execute the "hvshut" command to stop RMS on all the nodes of the cluster system. For details on "hvdisp" and "hvshut", see the pages of these commands respectively.
Set up "remote file copy" and "remote command execution" for the RMS Wizard. See the notes on "5.1.1 Setting Up CF and CIP."
If the cluster interconnect is not protected by security, cancel the "remote file copy" and "remote command execution" settings on all the cluster nodes after setting up the cluster applications.