Managed devices (servers, storage units, and network devices), the admin server, and the admin client are connected to the admin LAN.
An admin LAN can be divided into multiple admin LANs. Using this function, communication among tenants on physical L-Servers performed through an admin LAN can be prevented.
When using multi-tenant functions, prepare a separate admin LAN for each tenant, and configure the admin LAN for each tenant for network pools.
This improves the security of the network.
When designing an admin LAN, the following information needs to be defined beforehand:
The number of tenants
The number of VLAN IDs for use on the admin LAN
As the upper limit of the number of VLAN IDs varies depending on the device, when using devices that connect with both the admin and public LANs, ensure that the number does not exceed the maximum.
The scope of VLAN IDs for use on the admin LAN
As the available VLAN ID range varies depending on the device, when using the devices that connect with both the admin and public LANs, ensure that ranges do not overlap.
The IP address range of the admin LAN
When using admin LANs with multiple subnets, communication from the admin server to the managed devices and admin clients is necessary, so ensure that the subnet address range does not overlap between different admin LANs.
Whether to configure admin route redundancy
For each server, choose the network interfaces to use for the following purposes.
Network interface assigned to the admin LAN
The number of network interfaces required for the admin server and managed servers can be determined as follows.
For a non-redundant configuration: one network interface
For a redundant configuration: two network interfaces
If HBA address rename is used, two network interfaces (named NIC1 and NIC2) are required regardless of network redundancy.
For details, refer to "9.1.1.5 Required Network Configuration when Using HBA address rename".
For PRIMERGY Managed Servers
For a non-redundant configuration
NIC1 (Index1)
For a redundant configuration, or when using HBA address rename
NIC1 (Index1) and NIC2 (Index2)
The NICs above used by managed servers are the default values, and they can be changed when registering managed servers.
For details, refer to "5.4 When Using Blade Servers" and "5.5 When Using Rack Mount and Tower Servers" in the "User's Guide for Infrastructure Administrators (Resource Management) CE".
For PRIMEQUEST Managed Servers
For a non-redundant configuration
The smallest NIC number of the GSPB allocated to a partition (*)
For a redundant configuration
The smallest and second smallest Onboard LAN NIC numbers of the GSPB allocated to a partition (*)
* Note: For the PRIMEQUEST 2000 series, take "GSPB" as meaning "IOU". For Extended Partition, allocate IOU GbE.
For Rack Mount or Tower Managed Servers
Check the alignment sequence and number of NICs on the back of rack mount or tower servers, and then decide the numbers of NICs specified for the admin LAN using consecutive numbers starting with 1 (such as 1, 2,...).
For a non-redundant configuration
NIC 1
For a redundant configuration
NIC 1 and NIC 2
Choose the following settings to fit the system environment.
Whether to useadmin LAN redundancy
Perform the redundancy of the admin LAN as below.
For physical L-Servers, use Intel PROSet, GLS, or Linux bonding.
For VM hosts, perform redundancy according to the server virtualization software used.
The network configuration for LAN switch blades
See
When the admin LAN is operated among multiple subnets, install DHCP servers referring to "2.1.1 Manager Installation [Windows Manager]" or "2.1.2 Manager Installation [Linux Manager]" in the "Setup Guide CE".
Note
For the admin server, only a single IP address can be used on the admin LAN.
A network address that was set when installing the manager has been registered as an admin LAN network resource.
Change the admin LAN network resource specifications, and register the IP address of a device that is not managed by Resource Orchestrator as an IP address to exclude from allocation.
If the IP address is not registered, it may conflict with the IP addresses of devices that are not managed by Resource Orchestrator.
When using blade servers, connecting the management blade to a LAN switch blade will make the management blade inaccessible in the event of a LAN switch blade failure. Therefore, it is recommended that the management blade be connected to the admin LAN using a LAN switch outside the chassis.
When performing I/O virtualization using HBA address rename, if specifying a 10Gbps expansion card (NIC) for the admin LAN, backup and restore, and cloning cannot be used.
Do not use products or services that use the functions of other DHCP servers or PXE servers on the admin server.
However, such products or services can be placed on the same network as Resource Orchestrator managers. In this case, configure the managed server for Resource Orchestrator to be excluded from being managed by any other DHCP server.
Do not configure multiple IP addresses for network interfaces used on the admin LAN.
When the same cloning image is deployed to multiple servers, IGMP snooping should be enabled on admin LAN switches. If IGMP snooping is not enabled, transfer performance may deteriorate in the following cases:
When ports with different speeds co-exist in the same network
When multiple image operations are being executed simultaneously
For PRIMERGY BX900/BX400 LAN switch blades operating in IBP mode, the admin LAN should not be included in the ServiceLAN or the ServiceVLAN group configuration.
Choose the LAN ports of the network devices (firewalls, server load balancers, L2 switches, Ethernet Fabric switches, and L3 switches) to be used.
Figure 9.2 Admin LAN Connection Example
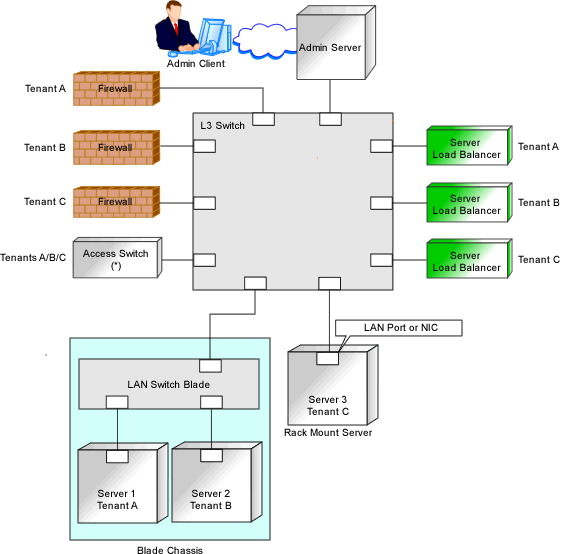
* Note: L2 switches or Ethernet fabric switches.
For environments where virtual L-Servers and the admin server (manager) communicate, it is recommended to perform the following configuration to improve security:
Place a firewall between the public LAN used by the virtual L-Servers and the admin LAN
Installing firewalls or configuring OS firewalls according to the description in "Appendix A Port List" enables secure operation of the admin LAN.
In Resource Orchestrator, the manager accesses agents using HTTPS communication.
Figure 9.3 Network Configuration Example
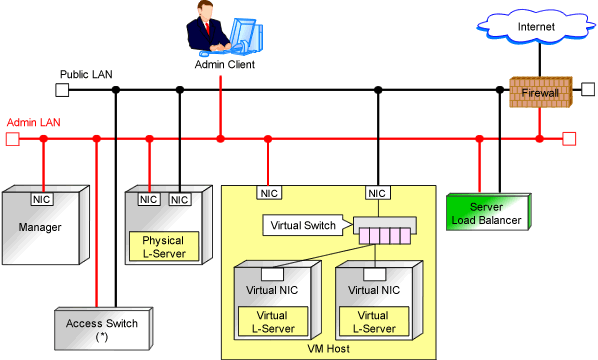
* Note: L2 switches or Ethernet fabric switches.
At startup a managed server set with HBA address rename needs to communicate with the Resource Orchestrator manager. To enable startup of managed servers even when the manager is stopped, Resource Orchestrator should be configured as follows.
A dedicated HBA address rename server
This section describes the network configuration that is required for an environment with a dedicated HBA address rename server.
For details about the HBA address rename setup service, refer to "6.1 Settings for the HBA address rename Setup Service" in the "Setup Guide CE".
This service must be on the same admin LAN as the admin server. Do not start more than one instance of this service.
This service uses NIC2 (Index2).
Connect NIC2 of the managed server to the admin LAN.
NIC2 is the default value, and it can be changed when registering managed servers.
For details, refer to "5.4 When Using Blade Servers" in the "User's Guide for Infrastructure Administrators (Resource Management) CE".
This service periodically obtains information about managed servers from the admin server and operates using this information. For this reason, it should be installed on a server that can be left active all the time.
There must be two LAN cables between LAN switches (cascade connection) on the admin server and on the managed server.
Note
The HBA address rename setup service cannot operate on the same server as ServerView Deployment Manager, or on a server where any other DHCP or PXE service is running.
The following diagram shows an example of how the HBA address rename setup service can be configured.
Figure 9.4 Sample Configuration Showing the HBA address rename Setup Service (with PRIMERGY BX600)
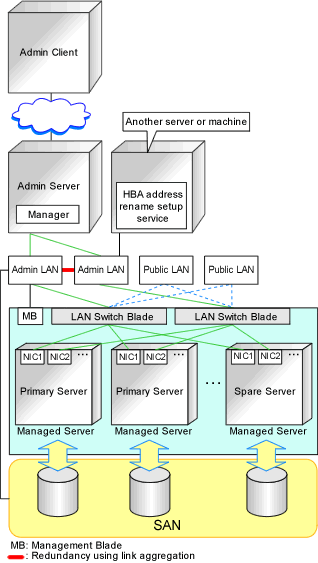
Connections between switches on the admin LAN can be made redundant using link aggregation.
Connect NIC2 (Index2) to the admin LAN (when it is the default).
Configure the HBA address rename setup service on a server connected to the admin LAN. This server must be different from the admin server.
Ensure that the server or personal computer that is used to operate the HBA address rename setup service is always on when the managed servers are active.