This section describes the logs that can be collected by record function.
Operation logs that can be collected
Set the policy to decide what kind of operation logs will be collected. Operation logs that can be collected are as follows.
The policy is set by the system administrator or department administrator in the Management Console.
Note
Functions may be restricted due to the environment being used
When setting the policy, functions may be restricted due to the environment being used.
For details, refer to "1.2.18 All Logs (for Clients (CT))" - "1.2.43 About Collection of Logs for Investigation of Client (CT)".
Application startup log
Application termination log
Application startup prohibition log
Window title obtaining log
E-mail sending log
E-mail receiving log
Device configuration change log
Printing log
Printing prohibition log
Logon prohibition log
File export log
PrintScreen key operation log
PrintScreen key prohibition log
Web operation log
Web operation prohibition log
FTP operation log
FTP operation prohibition log
Environment change log
Clipboard operation log
Clipboard operation prohibition log
File operation log
Logon/logoff log
Linkage application log
Configuration change log
Wi-Fi connection log (smart device)
Wi-Fi connection prohibition log (smart device)
Bluetooth connection log (smart device)
Bluetooth connection prohibition log (smart device)
Application usage log (smart device)
Application usage prohibition log (smart device)
Web access log (smart device)
SD card mount/unmount log (smart device)
SIM card mount/unmount log (smart device)
Incoming/outgoing calls log (smart device)
Application configuration change log (smart device)
Steps of viewing logs through policy setting
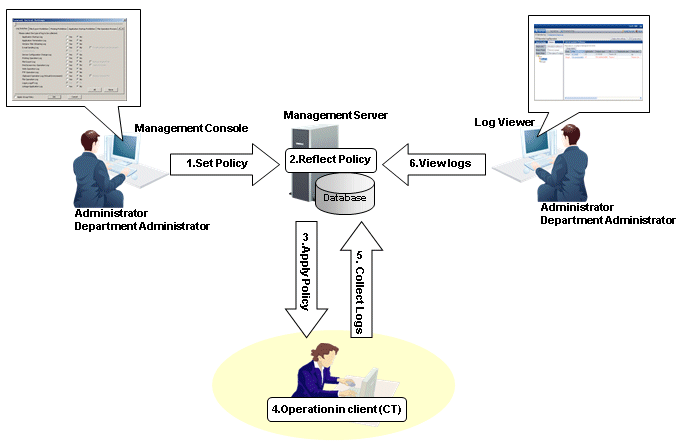
Set Policy
Set the policy for collecting various logs in the Terminal Initial Settings window, the User Policy Settings window or the window after starting the Management Console (the CT policy settings window).
Reflect Policy
The set policy will be reflected to the database.
Apply Policy
The set policy will be applied to the client (CT).
Operations in client (CT)
The client (CT) user performs various operations.
Collect Logs
Logs collected in the client (CT) will be sent to the Management Server.
When the client (CT) can communicate with the connected Management Server
The logs collected in the client (CT) will be sent to the Management Server according to the policy set in Send log of the policy settings window.
When the client (CT) cannot communicate with the connected Management Server
Logs collected in the client (CT) will be saved in the client (CT) temporarily. When the client (CT) can communicate with the connected Management Server, the logs collected in the client (CT) will be sent to the Management Server according to the policy set in Send log of the policy settings window.
View logs
The collected logs are viewed in Log Viewer.
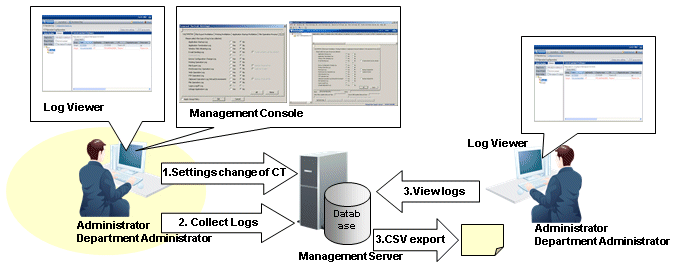
Configuration change of client (CT)
Change the settings information of the client (CT) in the Management Console or Log Viewer.
Collect Logs
The configuration change operation will be saved in the Management Server as a log.
View logs
View the configuration change operation performed in the Management Console in Log Viewer.
View the configuration change operation that is performed in Log Viewer (cannot be displayed in the List of Configuration Change Logs) and output to a CSV file. For details about the command for outputting configuration change logs in CSV format, refer to "DTKSTCV.EXE (output configuration change log)" of Reference Manual.
View logs
View the collected logs in Log Viewer.
Below is an example of the CT operation log display.
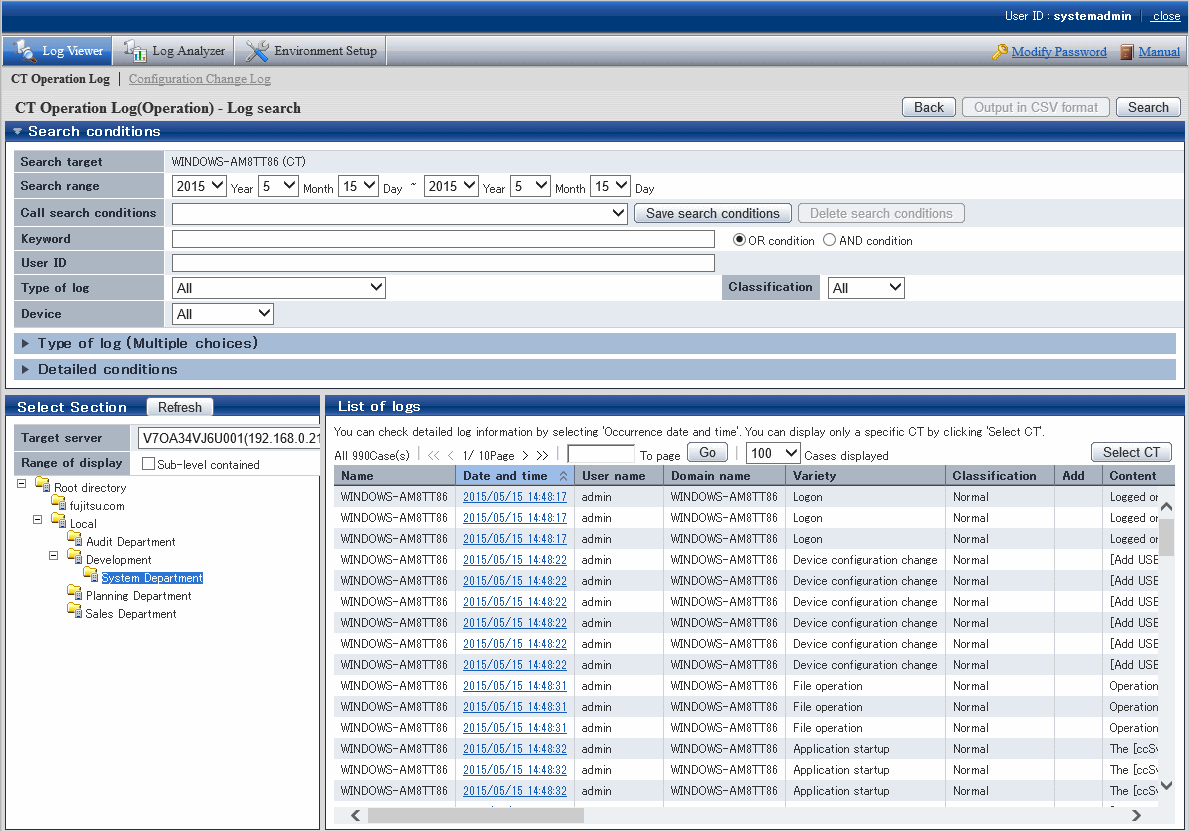
For items that can be viewed in Log Viewer, refer to "5.2.1 View Logs in the CT Operation Log Window", "5.2.2 View Logs in the User Operation Log Window" or "5.2.3 View Logs in the Configuration Change Log Window".