The server load balancer function is the function for distributing access from users based on configured rules, by virtualizing multiple servers (L-Servers) on an L-Platform as a single server.
Using this function provides the service including individual server load leveling, stable response, and flexible expansion.
Figure 1.6 Overview of the Server Load Balancer Function
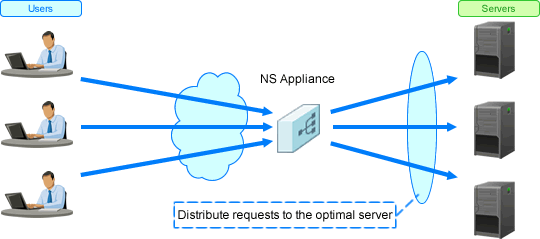
When a server (L-Server) error occurs on an L-Platform, inaccessibility can be avoided by distributing access to other operating servers (L-Servers). Response delay when access is concentrated can be avoided by distributing access to multiple servers (L-Servers) on an L-Platform.
Server maintenance or scale out can be performed by continuing the services, as multiple servers (L-Server) are used for operation.
NS Appliances provide the following functions:
When transferring the request from the client to the servers, the algorithm used to select the transfer destination server is called the server distribution method.
NS Appliances provide the following server distribution methods:
Server Distribution Method | Description |
|---|---|
Round robin | Transfers requests from the client to the server in order, regardless of the load of each distribution target server. |
Simple number of minimum connections | Transfers the access from the client to the server with the minimum number of connections, based on the number of connections being processed by each distribution target server. |
Monitors the operating statuses of servers, and when a failure is detected the failed server or application is excluded from the targets of transfer of requests from clients.
Figure 1.7 Overview of the Server Failure Monitoring
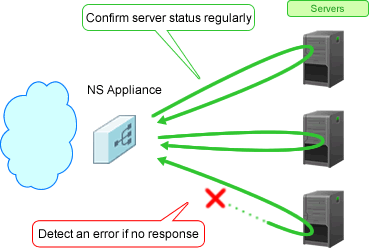
NS appliances provide the following server failure monitoring:
Server Failure Monitoring | Description |
|---|---|
Device monitoring | Monitors server failure depending on whether a response is received, by sending PINGs (ICMP Echo requests) at specified intervals |
Service monitoring | Monitors the operating status of applications based on the response for the TCP port and the UDP port of the applications operating on each server. Checks if a TCP connection is established for the TCP port. When a UDP probe packet is sent to the UDP port, if there is no response, it is regarded as normal. When ICMP unreachable packets are received, it is regarded as an error. |
Application monitoring | Supports the operation status of applications by monitoring their responses to requests sent to the application layers. Supports monitoring of the following application:
|
The following functions are provided as the option functions of server failure monitoring.
Option Function | Description |
|---|---|
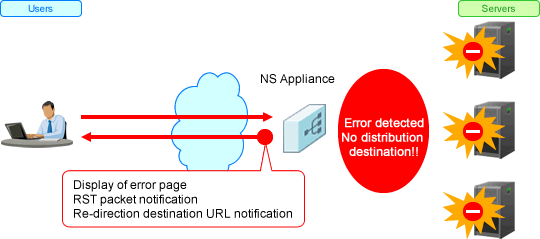
URL redirection | When a request from a client cannot be distributed to the distribution target server during HTTP communication, NS appliance returns an HTTP response to the client which redirects them to the notification URL. |
HTTP error message response | When all load balancing target servers have a high load or fail, NS appliance responds to the client, using error messages registered in NS appliance beforehand. |
Connection reset | When a server error is detected during TCP communication, the client is notified using a TCP RST packet for the TCP connection which is currently connected. |
Connection Purge | When a server error is detected during UDP communication, the management information of the UDP virtual connection which is currently connected is discarded. |
Figure 1.8 Overview of the Option Functions of the Server Failure Monitoring
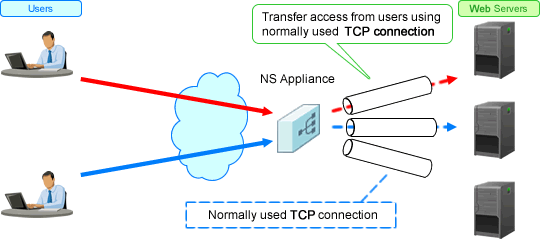
The function reduces the load of the web server, by decreasing the number of TCP connection establishment processes performed for each access from the client, by establishing TCP connections between an NS appliance and the web server in advance.
Figure 1.9 Overview of Web Acceleration
Transfers a series of packets (transaction) to the same server which was accessed before, for a certain duration.
Figure 1.10 Overview of Session Maintenance
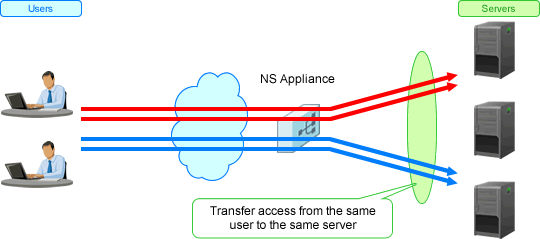
NS appliances provide the following session maintenance:
Unit | Description |
|---|---|
Node | Transfers the access from a specific node to the same server, using the node (IP address of client) as the unit. |
Connection | Selects the optimal server for each connection (TCP connection or UDP flow), and transfers to using the connection as the unit. When using a TCP connection (connection type), as long as the connection is established, the session is distributed to the same target server. When using UDP communication (connectionless type), the session is distributed to the same target server for a certain period of time (90 seconds). When using DNS communication, the session is distributed to the same target server for each query (request for DNS communication). |
Limiting the amount of access guarantees stable operation of the distribution targets.
Figure 1.11 Overview of Access Limitation
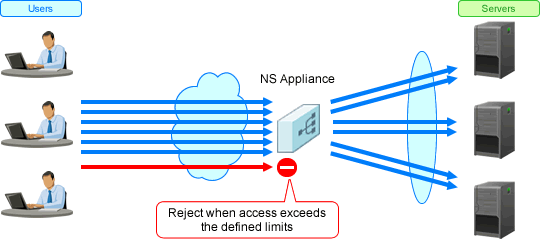
NS Appliance provides the following access limitation:
Limitation Target | Description |
|---|---|
Number of nodes | Limits clustered servers based on the number of the nodes. When the access limit is exceeded, packets received from the client are discarded. |
Number of connections | Limits clustered servers based on the number of connections. When the access limit is exceeded, packets received from the client are discarded. |
This function enables load distribution by converting HTTPS to HTTP communication, and improves the high availability of web servers (L-Servers).
Figure 1.12 Overview of SSL Accelerator
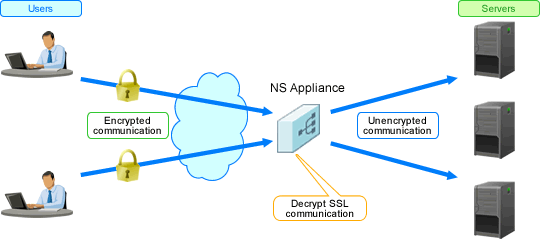
SSL encryption and decryption during HTTP communication by NS appliance makes it possible to show the communication as the HTTP communication of a web server (L-Server). It is not necessary to prepare the encryption function for each web server (L-Server).
NS Appliance supports the following protocols and allows for their customization:
SSLv3.0
TLSv1.0
NS Appliance supports the following cipher suites and allows for their customization:
For a CA certificate, the key length can be up to 4,096 bits, and for a server certificate, the key length can be up to 2,048 bits.
Name of Cipher Suite | Key Exchange (*1) | Encryption (*2) | Message Approval |
|---|---|---|---|
SSL_RSA_WITH_DES_CBC_SHA | RSA(4096) | DES(56) | SHA1 |
SSL_RSA_WITH_3DES_EDE_CBC_SHA | RSA(4096) | 3DES(168) | SHA1 |
SSL_RSA_EXPORT_WITH_DES40_CBC_SHA | RSA(512) | DES(40) | SHA1 |
SSL_RSA_EXPORT_WITH_RC2_CBC_40_MD5 | RSA(512) | RC2(40) | MD5 |
SSL_RSA_EXPORT_WITH_RC4_40_MD5 | RSA(512) | RC4(40) | MD5 |
SSL_RSA_EXPORT1024_WITH_DES_CBC_SHA | RSA(1024) | DES(56) | SHA1 |
SSL_RSA_EXPORT1024_WITH_RC2_CBC_56_MD5 | RSA(1024) | RC2(56) | MD5 |
SSL_RSA_EXPORT1024_WITH_RC4_56_MD5 | RSA(1024) | RC4(56) | MD5 |
SSL_RSA_EXPORT1024_WITH_RC4_56_SHA | RSA(1024) | RC4(56) | SHA1 |
SSL_RSA_WITH_RC4_128_MD5 | RSA(4096) | RC4(128) | MD5 |
SSL_RSA_WITH_RC4_128_SHA | RSA(4096) | RC4(128) | SHA1 |
SSL_RSA_WITH_AES_128_CBC_SHA | RSA(4096) | AES(128) | SHA1 |
SSL_RSA_WITH_AES_256_CBC_SHA | RSA(4096) | AES(256) | SHA1 |
*1: The number in () is the maximum key length (bit) used for key exchange
When the key length of the certificate is shorter than the number in (), use the key length of the certificate. When the key length of the certificate is longer than the number in (), use the key length of the number in ().
*2: The key length (bit) used for encryption during bulk transfer.
Name of Cipher Suite | Key Exchange (*1) | Encryption (*2) | Message Approval |
|---|---|---|---|
TLS_RSA_WITH_DES_CBC_SHA | RSA(4096) | DES(56) | SHA1 |
TLS_RSA_WITH_3DES_EDE_CBC_SHA | RSA(4096) | 3DES(168) | SHA1 |
TLS_RSA_EXPORT_WITH_DES40_CBC_SHA | RSA(512) | DES(40) | SHA1 |
TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5 | RSA(512) | RC2(40) | MD5 |
TLS_RSA_EXPORT_WITH_RC4_40_MD5 | RSA(512) | RC4(40) | MD5 |
TLS_RSA_EXPORT1024_WITH_DES_CBC_SHA | RSA(1024) | DES(56) | SHA1 |
TLS_RSA_EXPORT1024_WITH_RC2_CBC_56_MD5 | RSA(1024) | RC2(56) | MD5 |
TLS_RSA_EXPORT1024_WITH_RC4_56_MD5 | RSA(1024) | RC4(56) | MD5 |
TLS_RSA_EXPORT1024_WITH_RC4_56_SHA | RSA(1024) | RC4(56) | SHA1 |
TLS_RSA_WITH_RC4_128_MD5 | RSA(4096) | RC4(128) | MD5 |
TLS_RSA_WITH_RC4_128_SHA | RSA(4096) | RC4(128) | SHA1 |
TLS_RSA_WITH_AES_128_CBC_SHA | RSA(4096) | AES(128) | SHA1 |
TLS_RSA_WITH_AES_256_CBC_SHA | RSA(4096) | AES(256) | SHA1 |
*1: The number in () is the maximum key length (bit) used for key exchange
When the key length of the certificate is shorter than the number in (), use the key length of the certificate. When the key length of the certificate is longer than the number in (), use the key length of the number in ().
*2: The key length (bit) used for encryption during bulk transfer.