It is required to audit the application status of security countermeasures according to the auditing guide decided by the user. The security auditing result can be used for changing security countermeasures.
In addition, the security auditing result can be output in the form of report and used as attestation of correct execution of security countermeasures.
Auditing pointer setups
Security guide is an evaluation standard to judge which security policy is the best based on security auditing. Security auditing shall be carried out in accordance with the auditing pointer. The following audited items are contained in the auditing pointer; the user shall decide which items to select.
Hardware
OS (system)
OS (user)
Internet Explorer
Security patch application
Anti-virus software
Applied virus definition
Access control
Encryption status
Installed auditing software
Applications
Systemwalker Desktop Patrol provides "Information Leakage Countermeasure" and "Vulnerability Countermeasure" as recommended auditing pointer. The user can define the recommended auditing pointers of him/her and use them after changing the audited items according to application methods and the environment.
In addition, besides recommended auditing pointers, the user-defined auditing pointers can be used for security auditing.
Application method
Systemwalker Desktop Patrol recommends two application methods of auditing security countermeasure.
Rectification Period is set
Because PCs always moves, it must be ensured that security auditing is carried out when executing the security countermeasures correctly every month. The problems can be handled during rectification period, so security auditing must be strictly carried out.
Rectification Period is not set
Being a safe execution policy of security auditing, the security auditing rectification period is not necessary to set, but it is necessary for judging security auditing status by month. Any problem must be completely handled before the next month.
Application method can be changed. For the newly installed Systemwalker Desktop Patrol, if the completion rate of security auditing is lower, it is required to set the security auditing rectification period, and the security auditing rectification period can be canceled after the Systemwalker Desktop Patrol can operate stably.
It is recommended that security auditing date and correction date should be set in Systemwalker Desktop Patrol so as to carry out periodic security auditing.
Security auditing can be carried out by schedule at night.
Application pattern
When the 15th day in every month is set as the first auditing date, and the 20th day as the last auditing date, security auditing shall be carried out as the following case shown below. In the following case, it is required to execute security countermeasures and improve security countermeasure execution status from the first auditing date to the last.
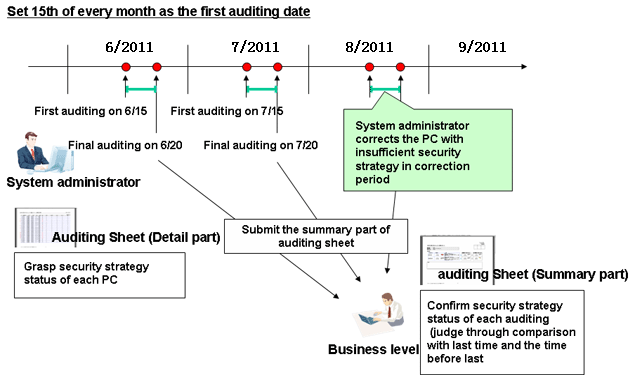
Security auditing shall be carried out according to the following procedure:
Output security auditing report at the first auditing date to master the current security countermeasure execution status.
Take security countermeasures after confirming that the security status is OK during the rectification period.
Security auditing shall be carried out every day during the rectification period, and security countermeasure shall be taken if the auditing result shows that the PC is not secure enough.
After taking security countermeasures collect the inventory information from the PC and confirm no any problem exists according to the security auditing report.
On the last auditing date, output the final security auditing data as a security auditing report.
The system administrator shall carry out the first auditing at the 15th day in every month. In addition, the system administrator shall confirm the output security auditing result and correct the application status of the device to which security countermeasures should be taken prior to the 20th day. On the 20th day in every month, the system administrator shall submit the security auditing result to the manager in charge.
If the rectification period is set, when the auditing result has any problem, the user of the problematic PC can take security countermeasures. If the problem cannot be solved in a short time, a grace period (rectification period) can be given the PC user to solve the problem.
When the 15th day in every month is set as the first auditing date, security auditing shall be carried out as the following case shown below. In the following case, if no rectification period is set, the system administrator shall output the security auditing report to confirm the execution status of long-term security countermeasures.
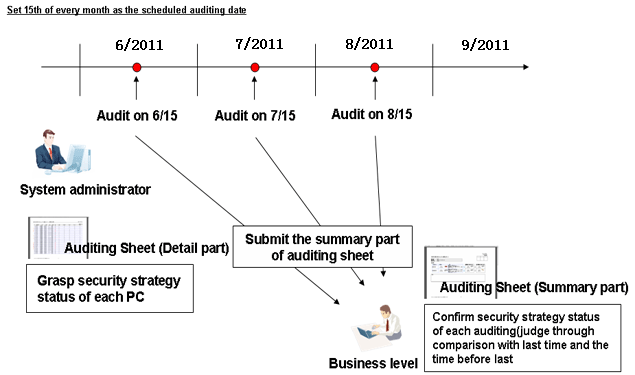
The system administrator shall take a regular security auditing at the 15th in every month. If security countermeasures have been taken, the system administrator shall carry out security auditing required when no rectification period is set when only needing to confirm the execution status of security countermeasures. If the auditing result becomes stable during the security auditing, the system administrator can give a judgment immediately.
Example of output security auditing report
Security auditing result shall be output as security auditing report. Security auditing report is an auditing or attestation report output to master and evaluate the application status of the security countermeasures against Systemwalker Desktop Patrol, Systemwalker Desktop Keeper and judge the risky section.
The following example is the output overview of security auditing report. The security auditing results for this time, last time or earlier can be output to confirm the changes in security status.
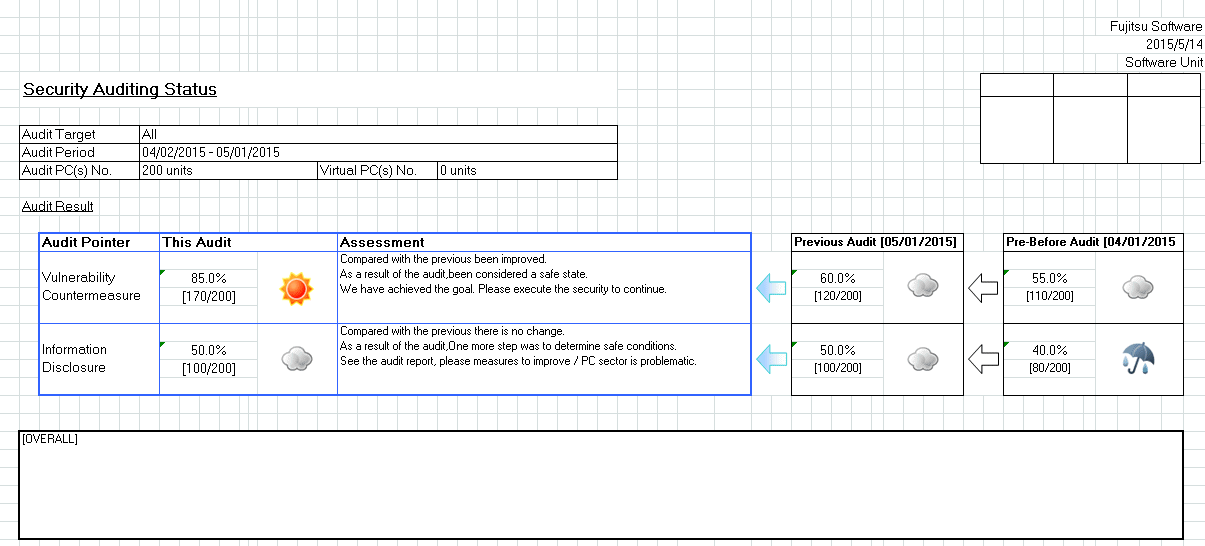
The following example is an output auditing report as part of security auditing report, which is used to display the auditing contents and completion rate of each audited item.
In addition, in the statistical result, it displays the group with high achievement rate having a higher percentage of OK events and the group with low achievement rate having a higher percentage of ERR events, to urge the group taking insufficient security countermeasures to correct security countermeasures.
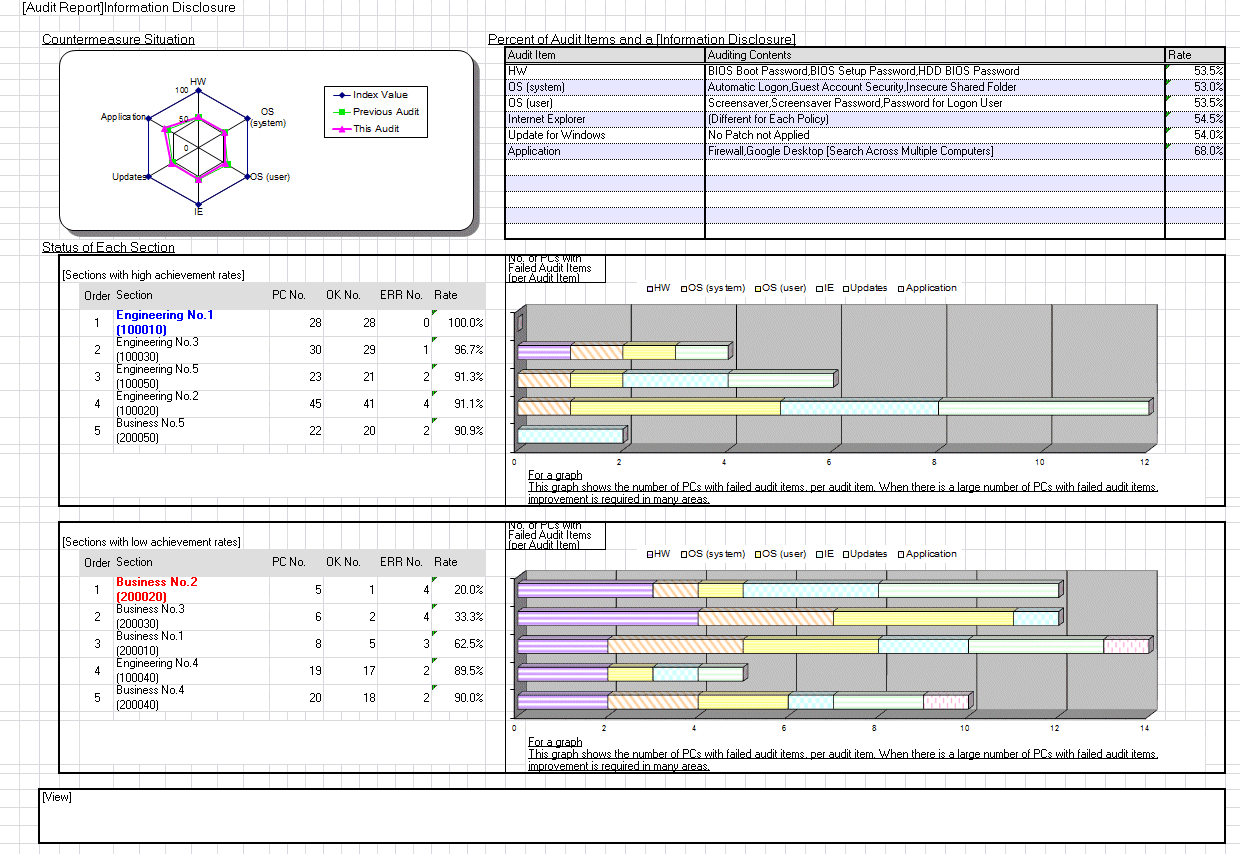
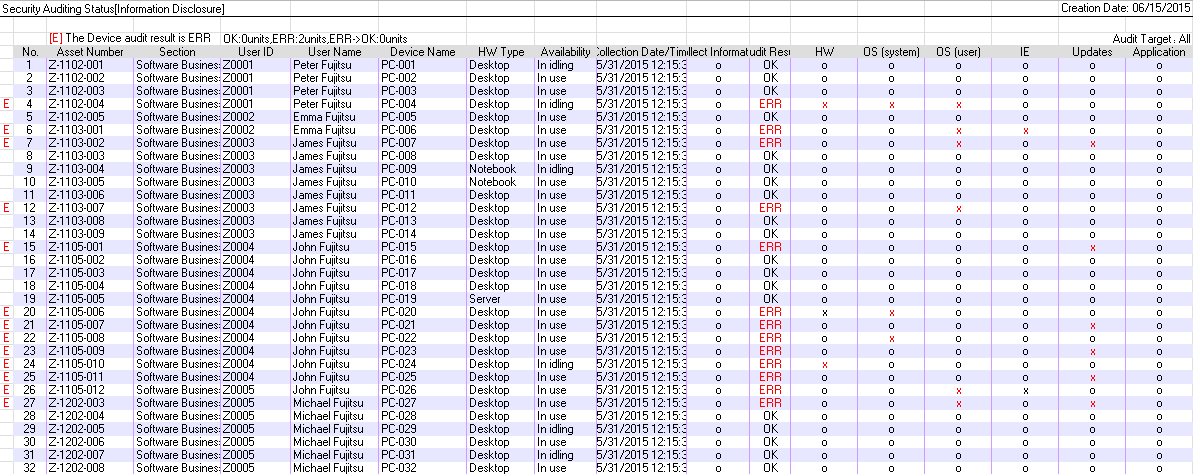
The following example is the detailed output of security auditing report, which displays security auditing result by device. According to the detailed output, you can find the devices to which insufficient security countermeasures are taken, and urge the system administrator to adjust security countermeasures.