NAS management of the ETERNUS Disk storage system will be explained.
Basic system configurations required when operating NAS of the ETERNUS Disk storage system will be explained.
Figure 6.1 Basic System Configuration Diagram
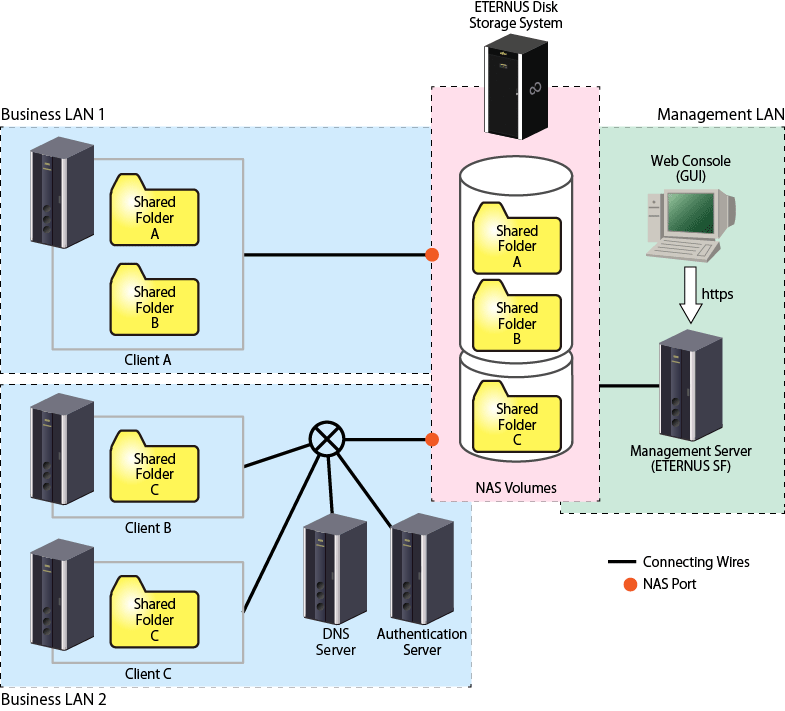
Configuration of NAS is performed from the Management Server.
Connect the Management Server and the ETERNUS Disk storage system with a management LAN. Access to the Management Server is performed from either the Management Server or the Web Console of a terminal within a network capable of HTTPS communication with the Management Server.
The NAS feature of the ETERNUS Disk storage system is accessed by a client through one or more business LANs. It is recommended that a business LAN include a DNS Server for name resolution and an Authentication Server for authenticating NAS accesses into the NAS file system.
Point
When an authentication system is not used for the NAS file system, it is unnecessary to setup an authentication server on the system.
If an authentication system is not implemented then the NAS file system can be accessed from any clients connected to the business LAN. It is strongly recommended that an authentication server is properly configured and implemented.
In order to perform NAS operation of the ETERNUS Disk storage system, this product is provided with the following features:
The "creating of a shared folder" and the "creating of a NAS interface" which are necessary when installing a NAS file system can be configured easily by using a wizard.
The configuration information resources being used for ETERNUS Disk Storage system NAS can be confirmed with the Web Console. In addition, when a failure occurs, the details of the failure will be displayed in the event log of the Web Console.
Capacity monitoring of NAS file system in ETERNUS Disk storage system is implemented at a level similar to that for block volumes.
This enables performance monitoring of resources with the ETERNUS Disk storage system below.
NAS volume
NAS system
Information
The performance monitoring and threshold monitoring functions cannot be used for NAS port.
The threshold monitoring function cannot be used for NAS volume and NAS system.
Backup and restoration of a NAS volume utilizes QuickOPC and a NAS backup volume. The use of the NAS backup volume provides protection against loss or corruption of the active NAS volume. In addition, the NAS backup volume can be accessed Read-Only for file level recovery.
This is a function that follows the specified schedule and automatically collects snapshots. The capture of the NAS volume snapshot is achieved using SnapOPC+. The NAS volume snapshot for the specified generation can be stored, and files and folders from the snapshot can be recovered without administrators.
This is a function for managing the upper limit of the quantity consumed by user or group. This prevents in advance the depletion of total resources due to large disk volume consumption by certain users or groups.
By registering the antivirus server provided by the antivirus security vendors, checking of access to files under the shared folder, detection of viruses and measures are performed automatically. This prevents data in the NAS environment being infected by viruses/illegal programs.
Configure the following with the Web Console in order to perform NAS operation of the ETERNUS Disk storage system.
The shared folder refers to a folder made public on the network as a NAS file system. With this product, by creating a shared folder and setting access controls, it is possible to capture a backup and snapshot.
When creating a shared folder from the Web Console, the following resources are also created simultaneously.
Resources | Explanation |
|---|---|
A volume where the shared folder will be created. | |
A volume for backup of the NAS volume. | |
This is a volume for the NAS volume snapshot. | |
System volumes are used to control NAS volumes. | |
Copy group used to back up NAS volume. | |
A copy pair of a NAS volume and a NAS backup volume. |
The shared folder that is created with this product can be accessed using the following protocols. As it is possible to use the following protocols simultaneously, it is possible to access a single shared folder from both UNIX and Windows clients.
A NAS interface refers to the definition information of a network interface that manages, over a business LAN, a public IP address for access to the shared folder and information of the port to which this IP address is assigned. When using the VLAN function, it is possible to configure multiple IP addresses for one port.
Information
There is no relation between the shared folder and the NAS interface. It is possible to reference the same shared folder from any NAS interface.
The NAS interface maybe assigned to a single port or 2 ports. The type of connections that can be configured are as follows:
A method where 2 ports are used, and an IP address is configured to each. Both ports are enabled, and it is possible to access the shared folder from either port. In addition, 2 IP addresses can be publicized for clients, and it is possible to distribute the bandwidth load. In the event that one port is down, as the IP address configuration can be passed on to the other port automatically, operation with the same IP address can be continued even after recovering from the down time.
Information
During the time one port is down, operation is limited to a single port. It is not possible to distribute the bandwidth load across 2 ports.
A method where 2 ports are used, and a single IP address is configured. Of the 2, only one port will be enabled (Active port), and the other port will be disabled (Standby port). When the Active port is down, the IP address configuration can be passed on to the Standby port which is automatically enabled, making it possible to continue operation with the same IP address even after recovering from the down time.
A method where 1 port is used, and a single IP address is configured. When the port goes down, it will not be possible to access the shared folder.
Information
In order to continue business when a port is down, it is recommended to configure either Active-Active or Active-Standby connection for redundancy.
Further, with the aim of increasing communication speed and becoming more fault-resilient, multiple physical ports can be bundled and handled as one logical port. Further, a NAS interface can be allocated for that logical port (bonding port). The method of determining communication ports of bonding port is to select an operating mode and hash policy.
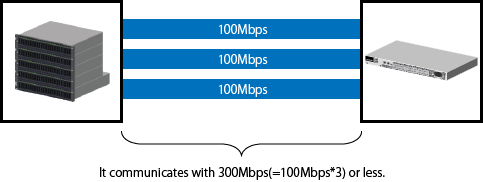
Networks are bundled to increase communication speed.
"Figure 6.2 Increase Communication Speed" is when three 100Mbps networks are bundled to communicate at maximum of 300Mbps.
Figure 6.2 Increase Communication Speed
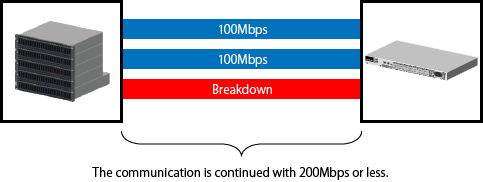
When a communication fault occurs in any one of the bundled networks, the remaining networks can continue communication.
"Figure 6.3 Improved Fault-Resilience" is when one of 3 networks has a fault so the remaining 2 networks continue at a maximum speed of 200Mbps.
Figure 6.3 Improved Fault-Resilience
NAS server name is a unique name set within the ETERNUS Disk storage system.
By registering the NAS server name set within the ETERNUS Disk storage system and the DNS server, it is possible to set the NAS server name and access the CIFS protocol shared folder.
Sets the DNS server to use when operating NAS.
It is possible to set a maximum of 2 DNS Severs for IPv4 and IPv6 respectively.
Authentication System
With this product, as access to the shared folder is controlled, an authentication system using a domain controller is provided.
The domain controller centrally manages the account information of individual clients on the network, and conducts authentication in relation to each of these clients or permits access.
In case an authentication server goes down, it is possible to register a maximum of 3 authentication servers for each authentication method.
The authentication methods supported by this product are as follows:
Kerberos Authentication Method with Active Directory
Kerberos is a network authentication protocol designed to provide strong authentication for client/server applications. A password received from a client is authenticated, and a ticket is issued. By utilizing the ticket, the client that has been authenticated is able to utilize the network service.
When accessing the shared folder with a CIFS protocol, and when managing access to directories and files, in order to perform authentication and access control using this authentication method, register an Active Directory domain controller.
Authentication Method using LDAP
LDAP is a protocol for accessing the directory service. With the directory service, it is possible to easily use features such as the search function by centrally managing the account information of network equipment and clients.
When accessing the shared folder with the NFS protocol, and when performing access management to directories and files, in order to perform authentication and access control using this authentication method, register an LDAP server.
An overview of backup of the NAS environment in the ETERNUS Disk storage system will be explained.
See
Refer to "Backup of NAS Environment" in the ETERNUS SF AdvancedCopy Manager Operation Guide for Copy Control Module for information on the backup operation for NAS environment.
It is possible to back up the entire NAS volume configured with the Web Console to a NAS backup volume. In addition, it is possible to restore the entire NAS volume from the NAS backup volume.
Figure 6.4 Backup/Restoration of NAS Volume
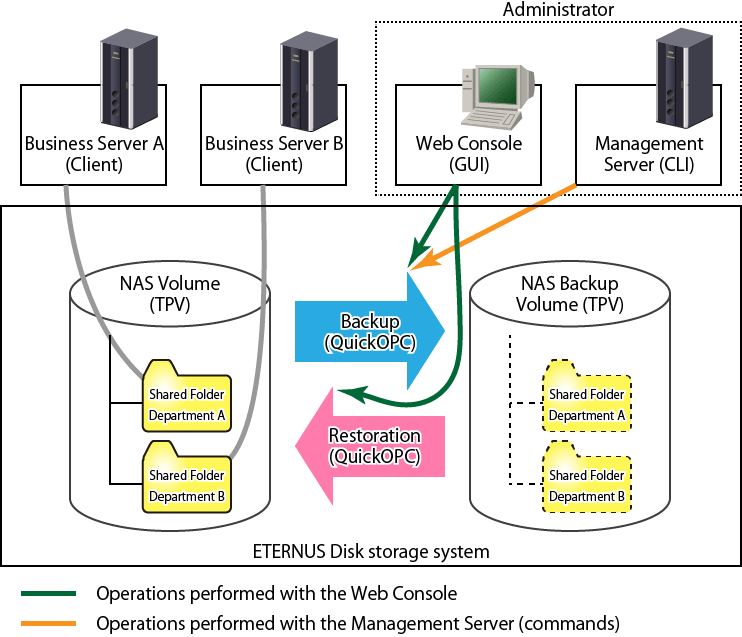
Information
Backup of the NAS volume can either be executed with the Web Console, or be executed with commands from the Management Server. Restoration of the NAS volume can only be executed with the Web Console.
When recovering individual files from the NAS backup volume, mount the NAS backup volume and manually copy the files.
The number of NAS volumes and NAS backup volumes creatable on one ETERNUS Disk storage system varies with the device model and its firmware version. Refer to the ETERNUS Disk storage system manuals for details.
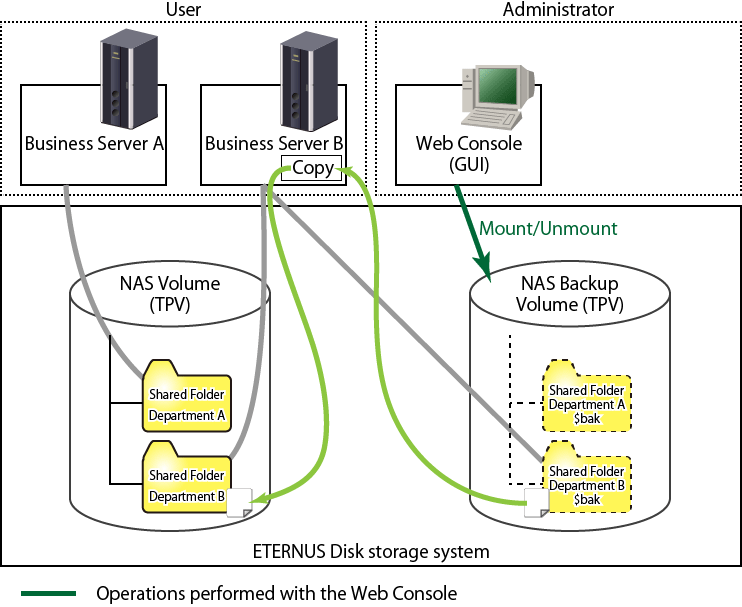
The NAS backup volume that is the backup destination of the NAS volume can be mounted onto the NAS environment as Read-Only. By mounting the NAS backup volume, users can recover files themselves. In addition, a mounted NAS backup volume can be unmounted when recovery has been completed.
Figure 6.5 Mounting/Unmounting the NAS Backup Volume
Information
Mounting and unmounting of the NAS backup volume can be done from the Web Console.
While the NAS backup volume is mounted, it is not possible to backup or restore the NAS volume.
The name of the shared folder on the NAS backup volume after being mounted is the name of the shared folder at the time of backup + "$bak". Furthermore, the name of the shared folder of the NAS backup volume will not be displayed on the Web Console.
This section provides an outline of the NAS environment snapshot function for the ETERNUS Disk storage system.
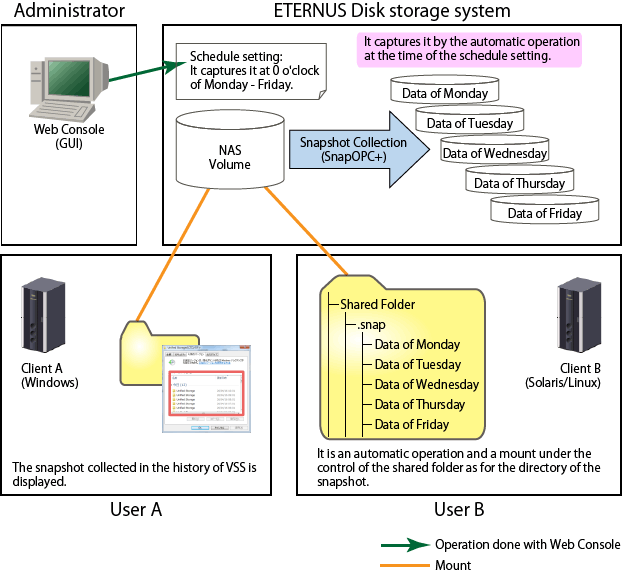
With the NAS snapshot, the snapshot can be captured regularly at the desired timing and that snapshot can be referenced from the client. The NAS volume snapshot is achieved using SnapOPC+. This is provided for the purposes of NAS volume generation management and to be able to recover files and folders deleted due to operating errors.
The NAS snapshot feature can be used by configuring the snapshot from the Web Console.
The following items are configured.
Snapshot generation number
Set the number of snapshot generations for the you want to own.
The number of configurable generations differs depending on the device model and firmware. See the manual accompanying the ETERNUS Disk storage system.
Schedule configuration
Sets the schedule for capturing the snapshots. A snapshot is taken on the day set every week or the hour set every day.
Figure 6.6 Outline of NAS Snapshot
Note
If a snapshot is collected while accessing a volume from an application, a snapshot at a point in time at which half-done data was written to the volume could be created. In this case, the data consistency in the snapshot is not ensured, so that the operation of the file in the snapshot is made impossible or the file content becomes incomplete.
Generally, to collect a snapshot whose data is consistent, the application accessing a volume must be stopped beforehand.
Configure a schedule for snapshot collection and the number of generations in a snapshot so that correct data can be traced back through generations when data inconsistency is found in the snapshot.
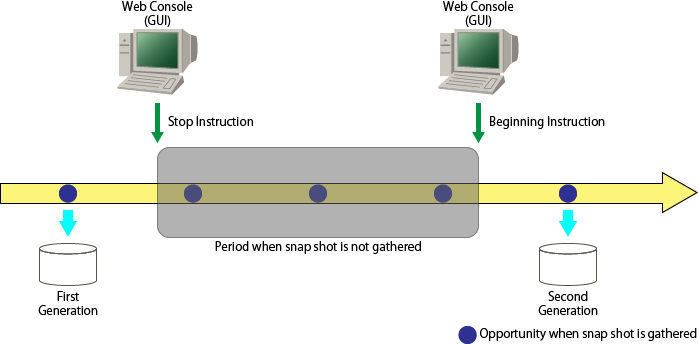
Where the NAS volume is temporarily not updated due to device maintenance period or long break, overwriting of past snapshots can be prevented by stopping the snapshot capture. When restarting the snapshot capture, execute snapshot capture start. Snapshot capture can be restarted carrying on with the snapshot before stopping.
Figure 6.7 Snapshot Capture Stop/Start
This section provides an outline of NAS environment quota management for the ETERNUS Disk storage system.
With quota management, the amount of usable resources can be limited. This prevents in advance the depletion of total resources due to certain users wasting disk capacity.
Restrictions on the disk usable volume and number of files for the user who is the owner of the shared folder and groups can be set using the following 2 values.
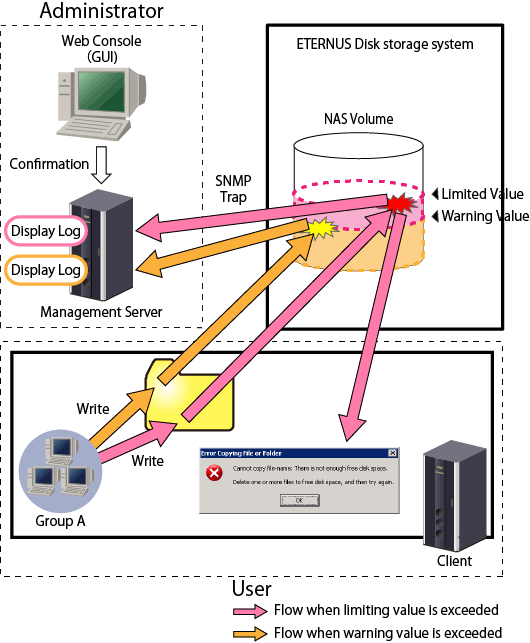
Limit value
This is the upper limit value actually used. When updating data that exceeds the limit value, there will be an error for the update.
Warning value
This is the value for providing pre-notification before reaching the limit value. When updating data that has exceeded the warning value, an SNMP Trap and event shall be notified to the operation management server.
Point
Even if a disk is used with a limit value exceeded, it may not cause any error. In this case, it is used up to disk use amount limitation value +2GB in the maximum.
When a NAS volume to which quota is set is backed up, its quota setting information is backed up at the same time. For this reason, when it is restored, its quota setting information backed up is applied.
Figure 6.8 Quota Management Outline
Information
Sets a quota for the users and groups registered on the authentication server set in "6.6.3.3 NAS File System Environment Settings".
By using mail notification and Systemwalker Centric Manager linkup feature, you are notified by E-mail when the quota management limit value or warning value are exceeded. Refer to "6.3 Event Display and Linkage" for details.
With quota management, an SNMP Trap is notified by the operation management server in the following cases.
Error occurred when data update or file creation was attempted with the limit value reached (Limit value exceeded)
Warning value exceeded (predicted)
Returned below warning value
The notified event can be confirmed on the quota management log screen on the Web Console. Logs are stored for 30 days.
See
Refer to "Display Quota Information" in the ETERNUS SF Web Console Guide for the procedure to display the Quota Management Log screen.
Point
Events are categorized by type; warning value exceeded, limit value exceeded, warning value removed, and notified every 10 minutes.
The limit value exceeded event is notified when an error occurred because data update or file creation was attempted with a limit value reached.
This section provides an outline of the antivirus for the NAS environment on an ETERNUS Disk storage system.
The antivirus function is linked to the antivirus server provided by the antivirus security vendor, and prevents data in the NAS environment being infected by viruses/illegal programs.
When the file is accessed from the client, the registered antivirus server checks the accessed file.
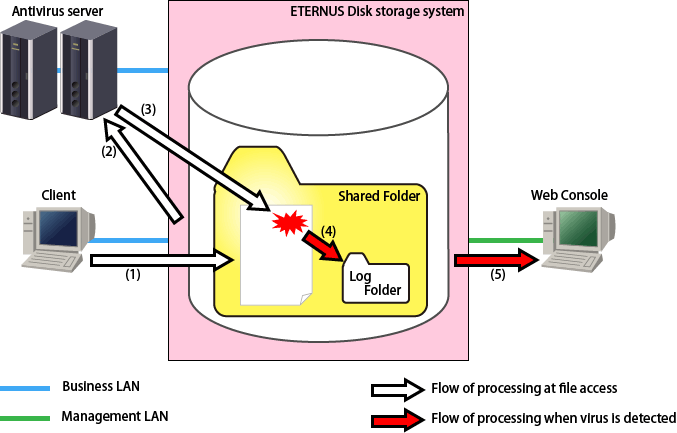
The client accesses files in the shared folder on the ETERNUS Disk storage system.
The ETERNUS Disk storage system instructs the antivirus server to perform a virus check on the accessed files.
The antivirus server checks the accessed files.
When it discovers a virus/illegal program, it outputs a detection log to the log folder.
When it discovers a virus/illegal program, the results of the detection are notified to the Web Console.
Point
The antivirus function only applies to shared folders using the CIFS protocol.
The NAS interface must be configured with the ETERNUS Disk storage system so that two CMs in the ETERNUS Disk storage system can communicate to the antivirus server.
We recommend establishing multiple antivirus servers. If the ETERNUS Disk storage system cannot communicate with the antivirus server, the client will not be able to access files in the NAS environment.
Refer to the ETERNUS Disk storage system manuals for the number of the antivirus server that can be registered in the ETERNUS Disk storage system.
Prepare an antivirus server activation code for each ETERNUS Disk storage system.
The antivirus function is available for shared folders that have writing authority.
The shared folders that have no writing authority are not scanned.
An IPv6 link local address is not available for the IP address of an antivirus server. When using IPv6, set an IPv6 global address.
When using FQDN, set it so that it is not converted to an IPv6 link local address.
If the antivirus server detects a virus it will deal with it automatically.
Please check the action taken by the antivirus server according to the following procedures:
Access the shared folder and check the logs are output to the following folder.
\\nasInterfaceIpAddress\sharedFolderName\.evscan\log
The log file names are as follows:
Latest logs
viruslog_YYYY_MM.txt
YYYY: year, MM: month(1~12)
Past logs
viruslog_YYYY_MM_partN.txt
YYYY: year, MM: month(1~12), N: control No.(decimal starting from 1)
See
Refer to the message output to the log for details of the log. Refer to the ETERNUS Disk storage system manuals for the action.
Check the action taken by the antivirus server from the content of the log.
If you want to check the detected content in detail, provide the log and relevant file to the vendor for confirmation.
Files quarantined by the antivirus server are in the following folder.
\\nasInterfaceIpAddress\sharedFolderName\.evscan\quarantine
Point
When the capacity of the log output destination is not sufficient, an SNMP Trap will be sent. When notified, perform the following to secure capacity.
Extend the NAS volume.
Delete unnecessary past logs and files in the .evscan\quarantine folder.
When quota management is set, raise the limit value.
Logs in the .evscan\log folder are stored for 90 days.
As an antivirus, in the following cases an SNMP Trap will be notified to the Management Server.
A virus is detected
Pattern files that exceed 2 days are not updated.
Scan engine is not up to date
Pattern files/scan engine have been updated
Unable to communicate with antivirus server
Communication recovered with antivirus server
The activation code expiry date is in the next 30 days.
The activation code expiry date has expired.
Notified events can be confirmed on the Web Console antivirus log screen. Logs are stored for 90 days.
See
Refer to "Display Antivirus Information" in the ETERNUS SF Web Console Guide for the procedure to display the Antivirus Log screen.
The functions of the NAS option of the ETERNUS Disk storage system can be used with the following environments.
Object | Environment |
|---|---|
Platform | Platforms on which the ETERNUS SF Manager can be operated. |
Required licenses (software) |
|
ETERNUS Disk storage system | ETERNUS DX100 S3/DX200 S3/DX500 S3/DX600 S3 |
Required options (hardware) | NAS Option |
Agent | Storage Cruiser's agent is not required. |
Authentication methods (*4) | [When accessing with the CIFS protocol] Active Directory [When accessing with the NFS protocol] LDAP |
Antivirus server | Trend Micro Storage Security for FUJITSU Storage ETERNUS DX S3 series |
*1: Required to construct the NAS file system.
*2: Required to back up the NAS volumes.
*3: Required to register either one.
*4: Required when performing access control using an authentication server for the NAS file system. When no authentication server is configured, all access will be permitted.