This describes the operation example when the file export and reading are performed using only the USB devices that are permitted by the administrator.
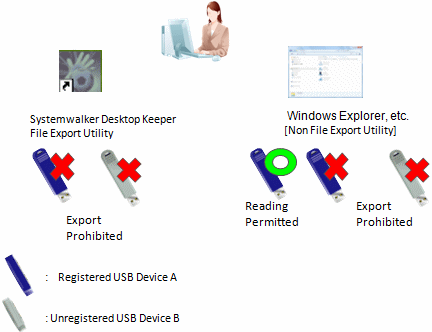
Exporting any file to the USB device is prohibited; Access can occur when files saved in the permitted USB device are expected to be viewed or imported as a business requirement.
This application can be achieved through the following settings:
Export using File Export Utility is prohibited. In addition, export by Explorer (Not Export Utility) is also prohibited. Only reading by Explorer (Not Export Utility) is permitted.
For policy setting, refer to "Policy setting of operation example 1".
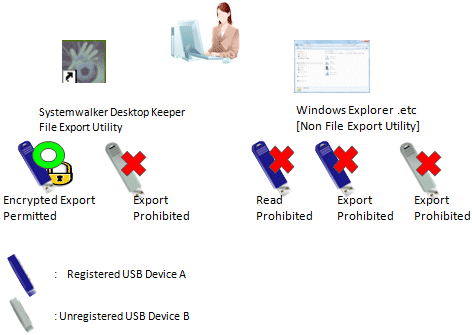
File export is allowed only after encryption using the Export Utility. In addition, exporting (copying) from the outside through the software (unless done by the administrator) is prohibited, while access to the USB device through Explorer (Not Export Utility) is also prohibited.
This application can be achieved through the following settings.
File export is allowed only after encryption using the Export Utility. Exporting and reading using Explorer (Not Export Utility) are prohibited.
Refer to "Policy setting of operation example 2" for policy setting.
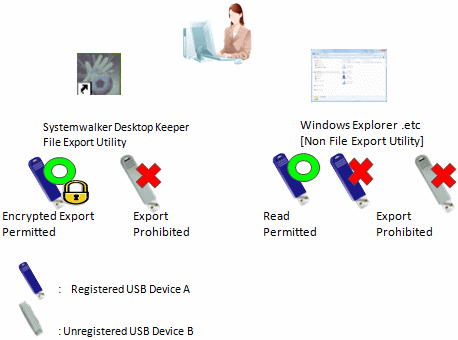
File export is allowed only after encryption using the Export Utility. At this time reading is only permitted by Explorer (Non-File Export Utility).
This application can be achieved through the following settings.
File export is allowed only after encryption using the Export Utility. Reading through Explorer (Not Export Utility) is permitted, but the export is prohibited.
Refer to "Policy setting of operation example 3" for policy setting.
As the USB device with lock and encryption function has security functions, considering the convenience, it is expected to export using Explorer (Not Export Utility) (the File Export Utility will not be used and the accompanied security function of USB device will be used).
In addition, it is expected to connect the permitted USB with an external HDD to obtain backup files.
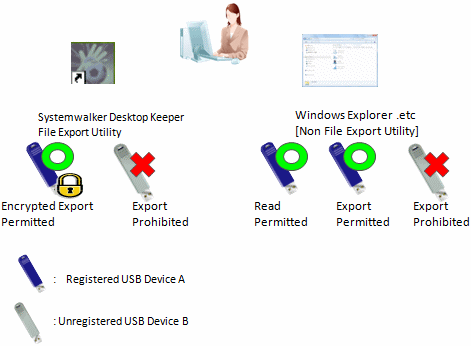
In the operation example 4, files can be copied to the USB device by Explorer (Not Export Utility) instead of File Export Utility. However, since File Export Utility is not used, the file export logs cannot be collected and the original of exported files cannot be backed up. Access to the USB device can be confirmed by collecting file operation logs.
When collecting the file export logs and backing up the original of export files, set File Export Utility and export files through File Export Utility.
This application can be achieved through the following settings.
Export and reading by Explorer (Not Export Utility) are permitted.
*Though related settings of File Export Utility are not needed, the condition of the file export log expected to be collected and the original file exported by the backup file also need to be considered, and become the set example in the above picture.
Refer to "Policy setting of operation example 4" for policy setting.
By setting the period for use of the USB device, the USB device is permitted to be used within a set time only. The USB device that exceeds the period of use cannot be used. By setting the period for using the USB device again, the USB device that exceeds period of use can continue to be used.
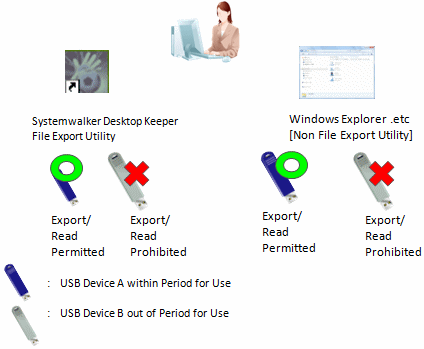
This application can be achieved through the following settings.
Set the period for use of the USB device, and permit exporting and reading.
Note: It can also be limited to use by File Export Utility only or set to read only.
For policy setting, refer to "Policy setting of operation example 5".
When a large number of USB devices exist, it is difficult to set permissions of USB devices for each client (CT) and user. In this case, the problem can be solved by using USB devices registered on the Management Server/Master Management Server.
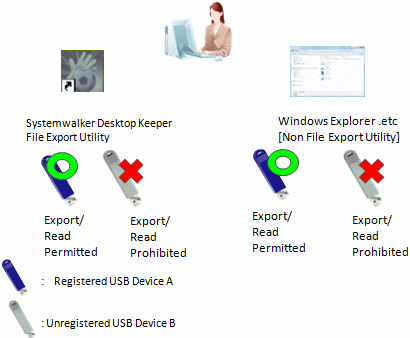
This application can be achieved through the following settings.
Permit the use of all USB devices registered on the Management Server/ Master Management Server, and permit exporting and reading.
It can also be limited to use by File Export Utility only or set to read only.
Refer to "Policy setting of operation example 6" for policy setting.
This example assumes that the USB devices have the same product ID and manufacturer ID, and that only some of them should be prohibited for use by a certain department.
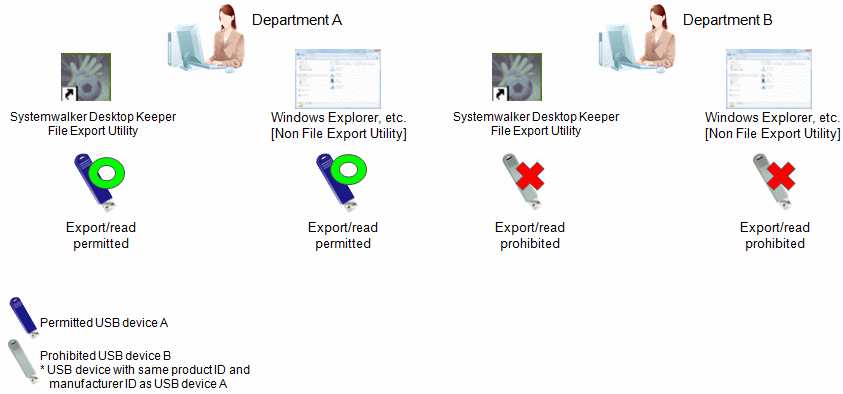
This operation can be achieved through the following settings.
In the USB Device Registration window, register "USB device A" in Product Match and "USB device B" as Not Available.
When the registration is performed, the product ID and manufacturer ID of "USB device A" and "USB device B" will become the same.
For the group policy for "Section A", permit the use, export, and read of all USB devices registered in the Management Server.
For "Section B", specify "USB device B" as its group policy.
Refer to "Policy setting of operation example 7" for details on policy settings.
This example assumes that the USB devices have the same product ID and manufacturer ID, and only some of them should be prohibited for use by a certain department.
In this example, the use of digital cameras is prohibited, in addition to the operation example 4. This will enable only permitted digital cameras to be used, and other digital cameras, scanners, digital voice recorders or similar will be prohibited.
Note that settings for read/write permission are not available for portable devices or imaging devices. Also, there is no operation exclusively designed for Export Utility.
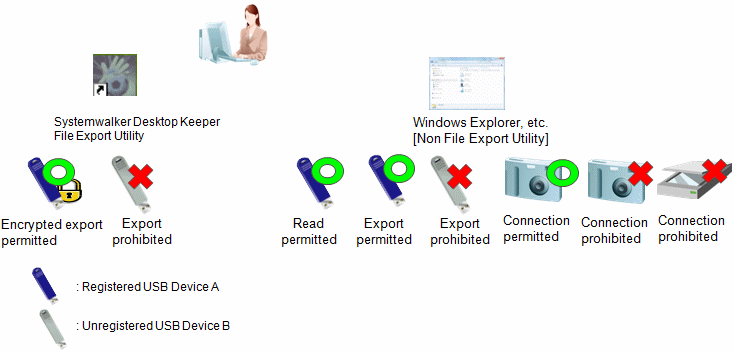
This operation can be achieved with the following settings.
Exporting and reading using Windows Explorer or similar (other than Export Utility) will also be authorized.
Settings related to Export Utility are optional.
Refer to "Policy setting of operation example 8" for details on policy settings.