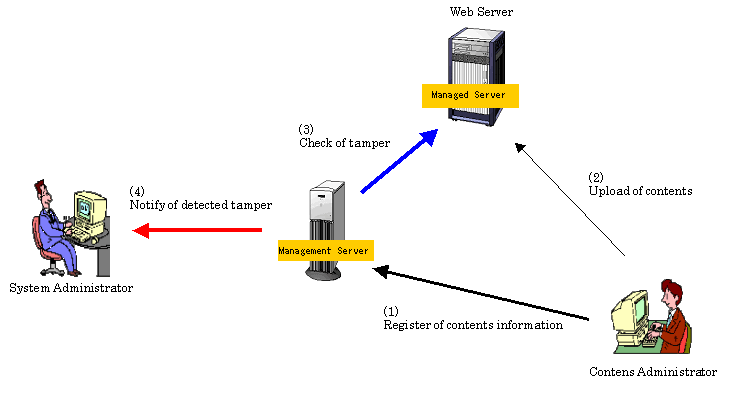
The figure below shows an overview of tamper monitoring. The Contents Administrator registers content information for the Management Server ((1) in the figure) and then uploads the contents to the Web Server ((2) in the figure). The Contents Tempering Monitor, based on the registered content information, checks the contents on the Managed Server ((3) in the figure) and, if tampering is detected, notifies the System Administrator of the event through e-mail ((4) in the figure).
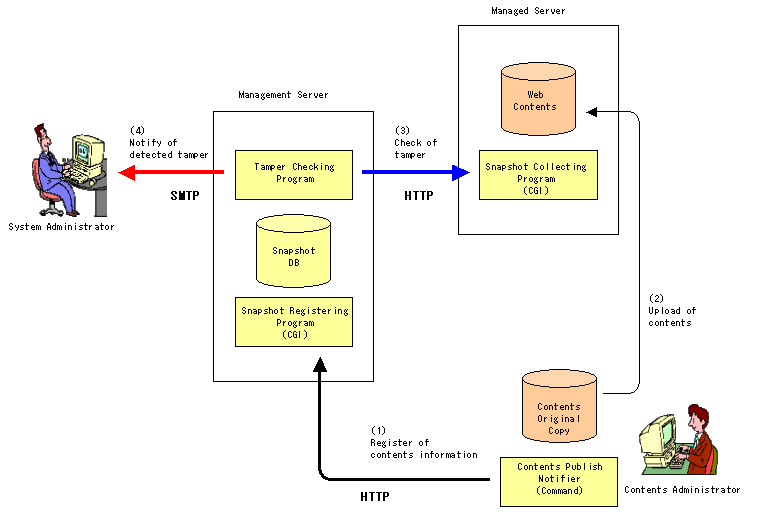
The figure below shows the internal operations of the Management Server, Managed Server and Contents Administrator's machine. The yellowish portions in the figure show the components of the Contents Tampering Monitor. The operation at (1) in the figure, which is caused when the Contents Administrator executes the Contents Publish Notifier, stores Contents Original Snapshot in the Snapshot DB. The operation at (3) in the figure, which is caused by periodical activation scheduled on the Management Server, compares the Web Contents (snapshot) and Contents Original Copy (snapshot in the Snapshot DB) for inspection. The operation at (4) in the figure is caused when tampering is detected in the operation at (3).
Note
The Snapshot Collecting Program (CGI) is a component installed together with Agent for Business. For this reason, Agent for Business must be installed on the Managed Server to be monitored.
Snapshots are generated based on the binary of the content, so if, for example, code conversion is performed using the operation in step 2 above, a discrepancy will arise between the registered binary for the content original and the binary for the public content, and tampering will be detected.
In order for tamper monitoring to operate correctly, take care during the operation in step 2 of the figure above to ensure that no discrepancy arises between the registered binary for the content original and the binary for the public content.
Point
"17.1.3 Tampering inspection program " are record and sent as follows:
The operating status is recorded in the Contents Tampering Monitor. The record can be referenced through the "13.1.6 Action Statement window"
Tamper detection is recorded in the Send Log Path
A tamper detection message is recorded in the system log (event log under the Windows version or syslog under the Solaris version).
A tamper detection message is sent to the Alert E-mail Address and CC
Point
The Contents Tampering Monitor has a function that can correctly distinguish negligence from tampering even if the Contents Administrator forgets to perform the operation at (2) in the figure after the operation at (1). However, the function cannot distinguish operations correctly if they are performed in reverse order (operation (1) after operation (2)). Also, the function cannot distinguish correctly if operation negligence continues.
The load on the Web Server is only snapshot collection for contents (minimum load).
Because of a configuration for remote monitoring from the Management Server, even multiple Web Servers can be monitored in a batch.
The following sections explain the tamper monitoring procedures based on the figure right above.