PRIMECLUSTER provides architectural patterns for taking over the network in cluster systems on public clouds. For smooth design of a cluster system, choose from these architectural patterns.
The following are the architectural patterns for taking over the network and the appropriate scenarios for each pattern.
Architectural pattern | Appropriate scenario | Note |
|---|---|---|
Network takeover by the virtual router | The cluster system of back-end servers used by the client in the VPC |
|
Network takeover by replacing the Elastic IP address | The cluster system of front-end servers |
|
Network takeover by rewriting DNS records | The cluster system of back-end servers used by the client on-premises or in any other VPC |
|
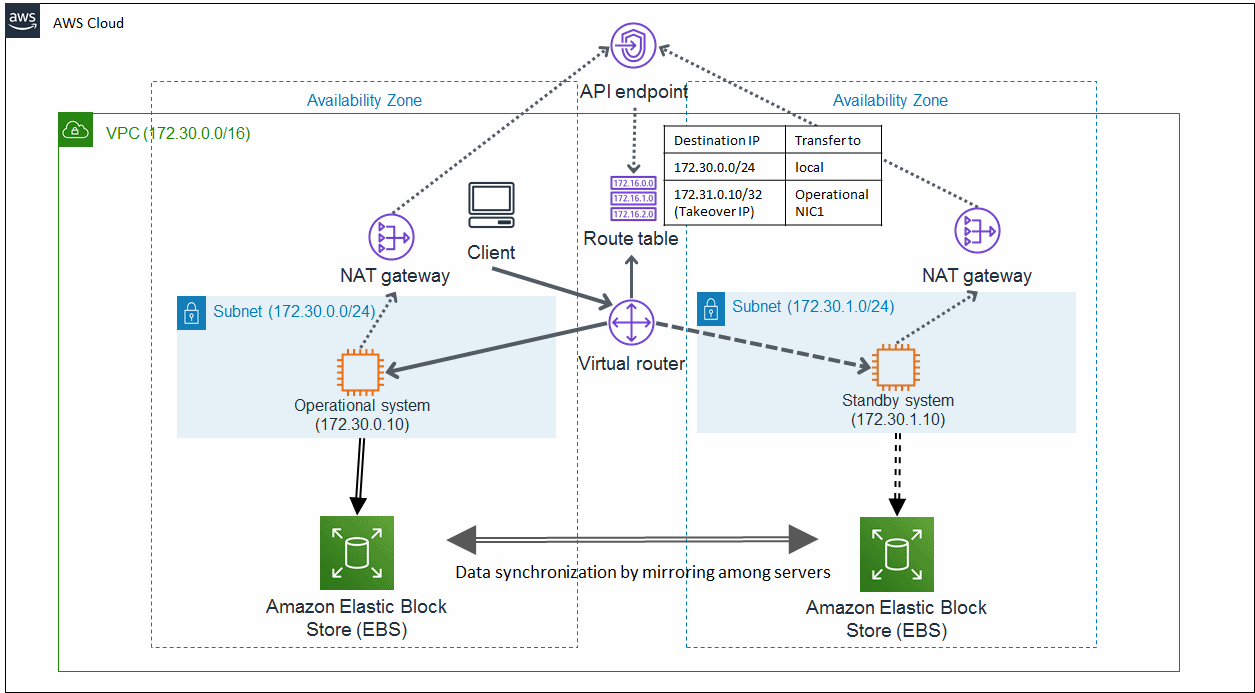
This is an architectural pattern using the cluster system from the client in the VPC. Select this architecture when building the cluster system in back-end servers used by the client in the VPC.
In this architectural pattern, the network takeover is enabled by rewriting the route table of the virtual router provided by AWS. In the event of a cluster node error, PRIMECLUSTER automatically rewrites the route table and switches to the standby system to take over the IP.
An access from public sites (clients outside of the VPC) is blocked and the cluster system is secured.
Figure 20.1 Taking over the network by the virtual router
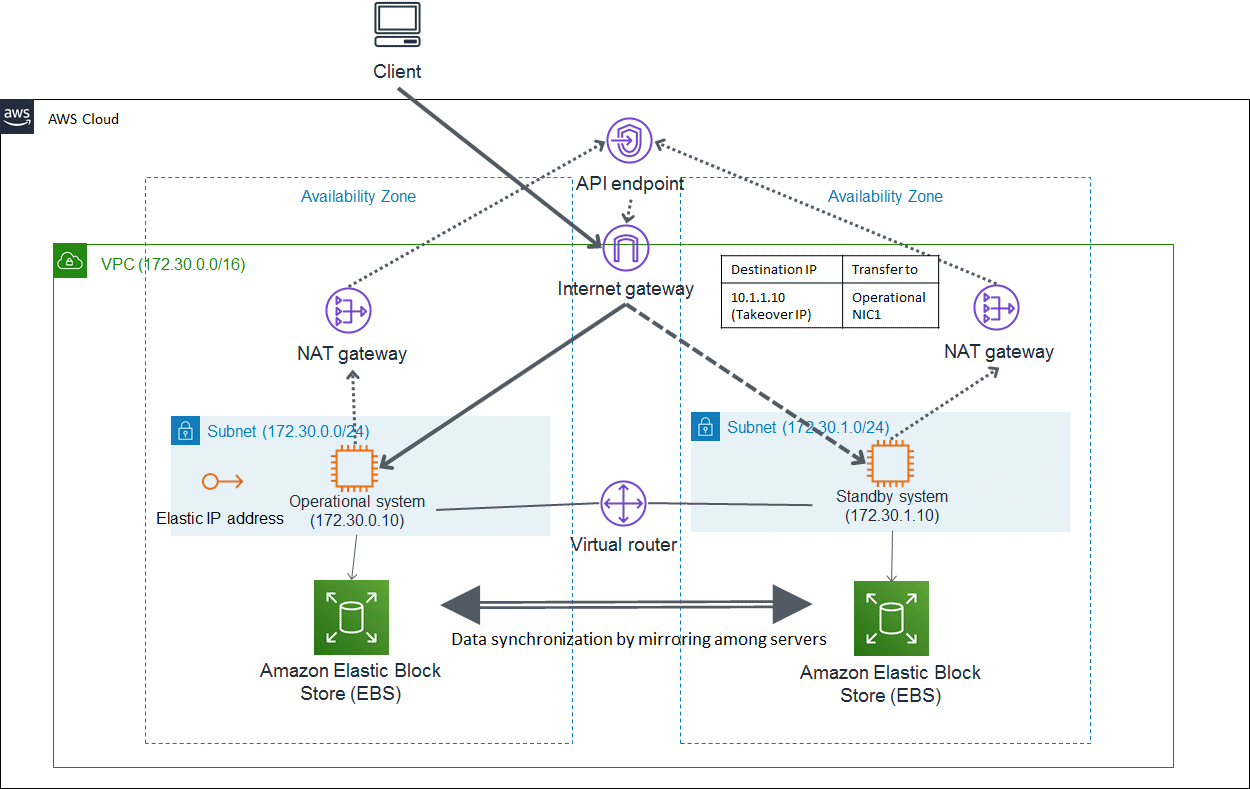
This is an architectural pattern that allows an access to the cluster node from public networks (the Internet). Select this architecture when building the cluster system in front-end servers.
In this architectural pattern, the network takeover is enabled by associating and controlling the operational network interface as a transfer destination for the Elastic IP obtained as the takeover IP. In the event of a cluster node error, PRIMECLUSTER changes the transfer destination of the takeover IP to the network interface of the takeover destination of the application and switches to the standby system to take over the IP.
The cluster system provides the client with the Elastic IP address as the takeover IP. The client accesses this Elastic IP address.
Note
To prevent unauthorized accesses from public sites with the administrator authority, do not co-use the administrative LAN and the public LAN.
Figure 20.2 Taking over the network by replacing the Elastic IP address
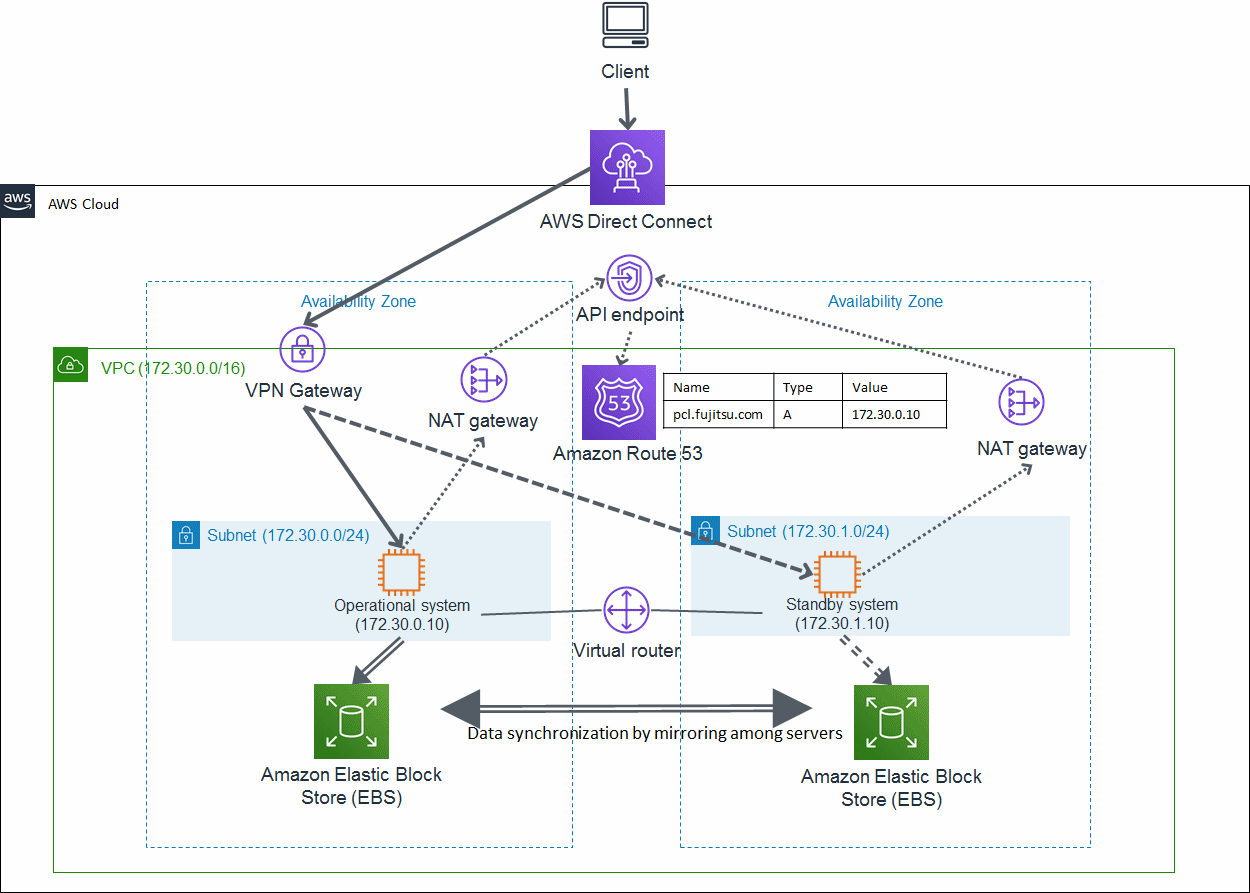
This is an architectural pattern using a VPN service from the client system on-premises to allow a direct access to the cluster node. Hybrid configurations such as on-premises for the application layer and cloud for the database access layer are possible. Select this architecture if the network takeover by rewriting the route table is unavailable when using a VPN service.
In this architectural pattern, the network takeover is enabled by rewriting records of a DNS service provided by AWS. In the event of a cluster node error, PRIMECLUSTER takes over the IP by replacing the related records held by a DNS service with the standby private IP.
Figure 20.3 Taking over the network by rewriting DNS records