For a built-in disk identified as a removable drive by the OS, logs will be collected and prohibition will be performed by considering the disk as a removable drive instead of a local drive.
When multiple logon is enabled on Windows Server 2008, Windows Server 2012 or Windows Server 2016, the email recipient confirmation window or the E-mail attachment prohibition window will not be displayed during the E-mail sending. The Systemwalker Desktop Keeper performs the following operations during the E-mail sending:
This does not apply when email is sent from Microsoft Outlook 2010, Microsoft Outlook 2013, or Microsoft Outlook 2016.
For the E-mail of which the recipient address is only the address of an exclusion domain, the information will not be displayed while the E-mail is sent, so there is no change.
For E-mails of which the recipient address contains addresses apart from the exclusion domain, execute judgment for the E-mail attachment prohibition. Perform the following operations according to the judgment result of the E-mail attachment prohibition:
When the prohibited file has been added, the E-mail sending will be terminated without showing the E-mail attachment prohibition window.
When the prohibited file is not added, the E-mail will be sent without showing the recipient prohibition window.
When multiple users are logged on, messages displayed during process control and service control will be sent to a specific user only. The display conditions are as follows:
When there is a locally logged-on user, messages will be displayed to that user.
When there is no locally logged-on user, messages will be displayed to one of the remotely logged-on users.
The policy status when multiple users are logged on is shown in the table below.
With smart devices (Android and iOS devices), only one user is logged on, so operation conforms to the CT policy.
"Multiple users logged on" means that at least two active users are logged on. For example, both local and remote users are logged on or at least two remote users are logged on. This does not apply to multiple local users logged on through switching, because in this case there will be only one active user.
Function | Valid Policy | |
|---|---|---|
Log (recording function) | Application startup/termination | User policy. |
Window title obtaining log | User policy. | |
E-mail sending | CT policy. | |
E-mail sending interruption | CT policy. | |
E-mail receiving | CT policy. | |
Command operation | User policy. | |
Device configuration change | (*1) | |
Printing operation | User policy. | |
File export | User policy. | |
PrintScreen key operation | User policy. | |
Web operation | User policy. | |
FTP operation | User policy. | |
File operation | CT policy. | |
Logon/Logoff | CT policy. | |
Clipboard operation | User policy. | |
Environment change | CT policy. | |
Linkage application | User policy. | |
Web access log (Android device) | CT policy | |
SD card mount/unmount log (Android device) | CT policy | |
SIM card mount/unmount log (Android device) | CT policy | |
Wi-Fi connection log (Android device) | CT policy | |
Bluetooth connection log (Android device) | CT policy | |
Incoming/outgoing calls log (Android device) | CT policy | |
Application usage log (Android device) | CT policy | |
Application configuration change log (Android device) | CT policy | |
Prohibition function | Application startup prohibition | User policy. |
Printing prohibition | User policy. | |
PrintScreen key prohibition | User policy. | |
Logon prohibition | CT policy. | |
E-mail attachment prohibition | CT policy. | |
File export prohibition | (*2) | |
File reading prohibition | (*2) | |
Device prohibition | (*3) | |
URL access prohibition | User policy. | |
FTP server connection prohibition | User policy. | |
Web download operation prohibition | User policy. | |
Web upload operation prohibition | User policy. | |
Clipboard operation prohibition | User policy. | |
Wi-Fi access prohibition (Android device) | CT policy | |
Bluetooth connection prohibition (Android device) | CT policy | |
Application usage prohibition (Android device) | CT policy | |
Device Functionality usage (iOS device) | CT policy | |
Application usage (iOS device) | CT policy | |
iCloud usage (iOS device) | CT policy | |
Security and privacy settings (iOS device) | CT policy | |
Content Ratings settings (iOS device) | CT policy | |
*1: The policy status for the device configuration change log depends on the settings in the File Export Prohibition - Individual Identification Feature - Detailed Settings window.
When operating according to the CT policy
When Allow to use all USB devices registered in Management Server is Yes
When operating according to the user policy
When Allow to use all USB devices registered in Management Server is No
In addition, the device configuration change log, which records the mounting of USB devices, operates according to the CT policy.
*2: File export prohibition/file read prohibition operates according to the CT policy, except the File Export Utility such as Windows Explorer. The File Export Utility operates according to the user policy.
*3: The policy status for device prohibition depends on the device.
When operating according to the CT policy
Wi-Fi connection prohibition
When operating according to the user policy
Bluetooth prohibition
PC card prohibition
PCI ExpressCard prohibition
Infrared communication prohibition
IEEE1394 prohibition
Serial port/parallel port prohibition
When the command prompt and File Export Utility are run by an administrator user, the message "Requested resource is in use" will be output sometimes and the application cannot be started. In this case, wait a moment and restart the application.
When using the Web console, do not click the Back button on the browser. If this button is used, errors may occur and it may not display properly.
Do not allow multiple users to log on the Windows OS at the same time using the same user ID. Otherwise, the logs cannot be differentiated.
In some cases the same log is sent by the client (CT) and smart device (agent) (Android) and stored in the Management Server. If this happens, the same log is displayed multiple times in the Log Viewer.
If you have logged on using the built-in Administrator account of the operating systems below, use Internet Explorer in the Desktop application on Web Console. Internet Explorer from Windows Store apps is not supported.
Windows 8.1 Pro
Windows 8.1 Enterprise
Windows 10 Home
Windows 10 Pro
Windows 10 Enterprise
Windows 10 Education
Microsoft Windows Server 2012 Datacenter
Microsoft Windows Server 2012 Standard
Microsoft Windows Server 2012 Essentials
Microsoft Windows Server 2012 Foundation
Microsoft Windows Server 2012 R2 Datacenter
Microsoft Windows Server 2012 R2 Standard
Microsoft Windows Server 2012 R2 Essentials
Microsoft Windows Server 2012 R2 Foundation
Microsoft Windows Server 2016 Datacenter
Microsoft Windows Server 2016 Standard
Microsoft Windows Server 2016 Essentials
Communication between the Management Server or Master Management Server and a client (CT) is encrypted.
Therefore, there are restrictions on unencrypted communications, such as communication with a client (CT) of V14.3.1 or earlier to which the communication encryption update has not been applied.
You must apply the urgent updates that were released in and after September 2014 to clients of V13.3.0 to V14.3.1, or upgrade to V15.1.0 or later.
You cannot use clients of V13.2.1 or earlier. Upgrade to V15.1.0 or later.
After you upgrade the Management Server to V15.1.0 or later, the clients that you can fresh install are V15.0.0 or later. However, client versions newer than the Management Server version cannot be installed.
After logging on using a Microsoft account, the Microsoft account information is stored in the user name and domain name of the log.
For example, if the Microsoft account is "fujitsu.tarou@example.com", the user name will show "fujitsu.tarou" and the domain name will show "example.com".
However, if you switch from an existing account to a Microsoft one, the existing account information may be stored in the user name and domain name of the log until the operating system is restarted.
The log user name recorded is the one used for logon. The user name used for domain logon is neither case- nor width-sensitive, so the user name recorded may differ from the one used during registration.
Policies that can be set on client (CT) and smart device (agent)
The Management Console allows setting all policies for clients (CTs) and smart devices (agents), but which ones will take effect depend on the device. If a policy is set but does not take effect on a specific device, the recording feature or prohibition feature will not operate.
Policy | Device | |||
|---|---|---|---|---|
Client (CT) | Smart device (agent) (Android) | Smart device (agent) (iOS) | ||
Log | Application startup | Y | N | N |
Application termination | Y | N | N | |
Window title obtaining | Y | N | N | |
E-Mail Sending/E-mail sending interruption | Y | N | N | |
E-mail receiving | Y | N | N | |
Command operation | Y | N | N | |
Device configuration change | Y | N | N | |
Printing operation | Y | N | N | |
File export | Y | N | N | |
PrintScreen key operation | Y | N | N | |
Web operation | Y | N | N | |
FTP operation | Y | N | N | |
File operation | Y | N | N | |
Logon,Logoff | Y | N | N | |
Clipboard operation | Y | N | N | |
Environment change | Y | N | N | |
Linkage application | Y | N | N | |
Web access | N | Y | N | |
SD card mount/unmount | N | Y | N | |
SIM card mount/unmount | N | Y | N | |
Wi-Fi connection | N | Y | N | |
Bluetooth connection | N | Y | N | |
Incoming/outgoing calls | N | Y | N | |
Application usage | N | Y | N | |
Application configuration change | N | Y | N | |
Prohibition feature | File access control | Y | N | N |
Device prohibition | Y | N | N | |
Application startup prohibition | Y | N | N | |
Print prohibition | Y | N | N | |
PrintScreen key prohibition | Y | N | N | |
Logon prohibition | Y | N | N | |
Attachment prohibition | Y | N | N | |
URL access prohibition | Y | N | N | |
FTP operation prohibition | Y | N | N | |
Web operation prohibition | Y | N | N | |
Clipboard operation prohibition | Y | N | N | |
Wi-Fi connection prohibition | N | Y | N | |
Bluetooth connection prohibition | N | Y | N | |
Application usage prohibition | N | Y | N | |
Device Functionality usage | N | N | Y | |
Application usage | N | N | Y | |
iCloud usage | N | N | Y | |
Security and privacy settings | N | N | Y | |
Content Ratings settings | N | N | Y | |
Y: The recording and prohibition features operate when this is set as a policy on Management Console.
N: The recording and prohibition features do not operate even when this is set as a policy on Management Console.
About character code that can be processed in Systemwalker Desktop Keeper
There are following two types of character code that can be processed in Systemwalker Desktop Keeper. Other character code will be converted to "?".
Local Character Code
It will be displayed correctly.
Unicode
It may be able to be displayed correctly or converted to "?".
Operation logs and prohibition logs collected by a client (CT) or smart device (agent) are stored using Unicode characters.
Any collected application log that cannot handle Unicode characters may be recorded as "?".
When performing the export operations below using the Export Utility, UNICODE characters cannot be specified in the export source or the export destination file and folder names.
Standard exports to DVD/CD
Entry and display operations in Management Console use Unicode characters.
However, if you have specified ShiftJIS for Encoding for I/O files in Server Settings Tool, any Unicode characters in an input file will not be displayed properly. If an output file contains Unicode characters, they will be converted to "?".
Entry and display operations in the Log Viewer use Unicode characters.
However, if you have specified ShiftJIS for Encoding for I/O files in Server Settings Tool, Unicode characters in the output file will be converted to "?".
Commands provided by Systemwalker Desktop Keeper and server-based tools such as Server Settings Tool do not support entry or display of Unicode characters.
Do not use the following tools and commands that are provided by Systemwalker Desktop Keeper because they may not operate properly:
Tools and commands that are installed in the Management Server or Master Management Server
Tools and commands that are installed in Relay Server
The Policy Application Tool
You cannot perform encryption export to a DVD or CD by using the Export Utility.
In Systemwalker Desktop Keeper, halfwidth character, fullwidth character, and character count are defined as follows:
Halfwidth character: A character with an ASCII code in the range 0x20 to 0x7E
Space
Symbols: ! " # $ % & ' ( ) * + , - . / : ; < = > ? @ [ \ ] ^ _ ` { | } ~
Numeric characters: 0-9
Alphabetic characters: A-Z, a-z
Fullwidth characters: Characters other than halfwidth characters
Halfwidth katakana characters (the width that is generally used) are treated as fullwidth characters.
Character count: Each halfwidth character is counted as 1 character.
Each UTF-16 2-byte fullwidth character is counted as 1 character.
Each surrogate pair character uses 4 bytes to represent 1 character, so it is counted as 2 characters.
Each combining character uses n bytes to represent 1 character, so it is counted as n/2 or less characters, depending on the combining character.
Operating system updates after installation of the client (CT)
Operating system updates after installation of the client (CT) are not supported.
If updates that do not change the operating system version (adding Windows 10 features, for example) are applied, CD/DVD devices cannot be referenced temporarily in some cases. In this case, recovery can be performed by restarting the operating system. If the issue persists, refer to "Considerations for Installation" > "Client (CT)" in the Installation Guide, and install the client (CT) again.
About monitoring methods for web communication
Monitoring operates using the hook method immediately after installation.
The differences between the local proxy method and hook method are as follows:
Item | Local proxy method | Hook method | |
|---|---|---|---|
Differences in operation logs that can be obtained | Web upload, Web download |
|
|
Mail send logs for Web email |
| Cannot be obtained | |
Window title logs (with URL) |
|
| |
Differences in operations that can be prohibited | Web upload and download prohibition |
|
|
URL access prohibition |
|
| |
Differences in items that can be retrieved | Application Name retrieved when using Internet Explorer | Internet Explorer | iexplore / iexplore.exe |
Application Name retrieved when using Microsoft Edge | Microsoft Edge | ApplicationFrameHost / ApplicationFrameHost.exe | |
Application Name retrieved when using Firefox | Firefox | firefox | |
Application Name retrieved when using Google Chrome | Google Chrome | chrome | |
File Name retrieved in Web upload operation logs | file name only | file name with full path | |
File Name retrieved in Web download operation logs | file name only | file name with full path | |
Differences in behavior after prohibition | An error message will be displayed in the tab where the prohibited URL was accessed. If a prohibited website is included inside a frame within a webpage, an error message will be displayed in that frame. | An error message will be displayed in a pop-up message. The tab where the prohibited URL was accessed will be forcibly closed. | |
Operations on virtual OS | Not supported | Supported | |
If using the local proxy method, refer to "8.16 Changing the Web Communication Monitoring Method" for details.
Web communication monitoring using the local proxy method
If using the local proxy method as the web communication monitoring method, note the following:
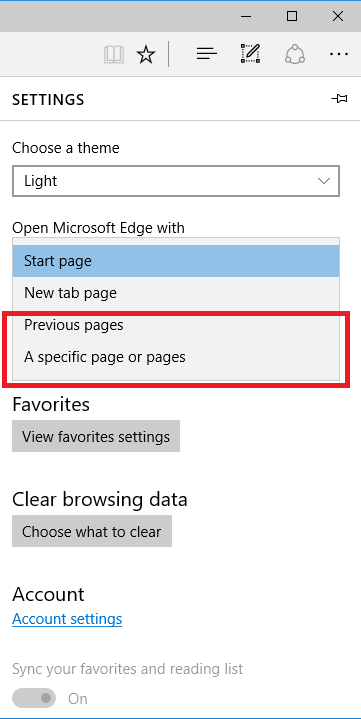
The start page may not be displayed correctly when Microsoft Edge is started.
The address can be entered directly into the address bar, or a bookmark can be used to display any website.
Also, this issue can be avoided by setting any option other than Start page or New tab page for the Open Microsoft Edge with item in the settings.
If access prohibition or upload/download prohibition have been configured, there is a possibility of errors occurring in applications other than the browser.
If using Firefox, the system proxy will be configured automatically regardless of the proxy configuration of Firefox.
The application name may be displayed as "Unknown".
The operation of the local proxy method is different depending on the start mode of the operating system. "Start in Normal Mode" and "Start in Safe Mode with Network Connection" work, but "Start in Safe Mode" (including the safe mode with command prompt) does not work.
Applications and websites may operate in the way that is equivalent to the following operations. In this case, logs may be obtained or prohibited by Web operation logs or Web upload/download prohibition.
Access to websites
Web upload
Web download
If a web browser is started immediately after Windows logon, the "Communication error" window may be displayed. Close the web browser and open it again after a few minutes. If the window is still displayed even after a few minutes, repeat this procedure until it is displayed properly.
If the proxy server settings of each device were changed after installing this product, the Automatically detect settings feature cannot be used. It is necessary to use the following procedure to change the proxy server settings.
Open the Control Panel or in Internet Explorer, open Internet Options.
In the Internet Properties window, click the Connections tab, and click LAN settings.
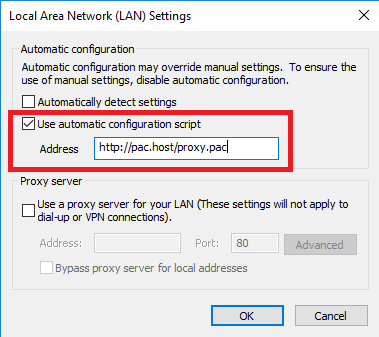
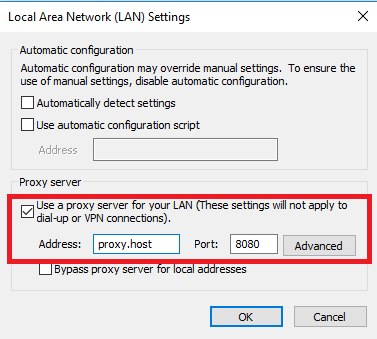
In the Local Area Network (LAN) Settings window, set either of the following.
Select Use automatic configuration script, enter the address, and click OK.
Clear Automatically detect settings.
Select Use a proxy server for your LAN, enter the address and port, and click OK.
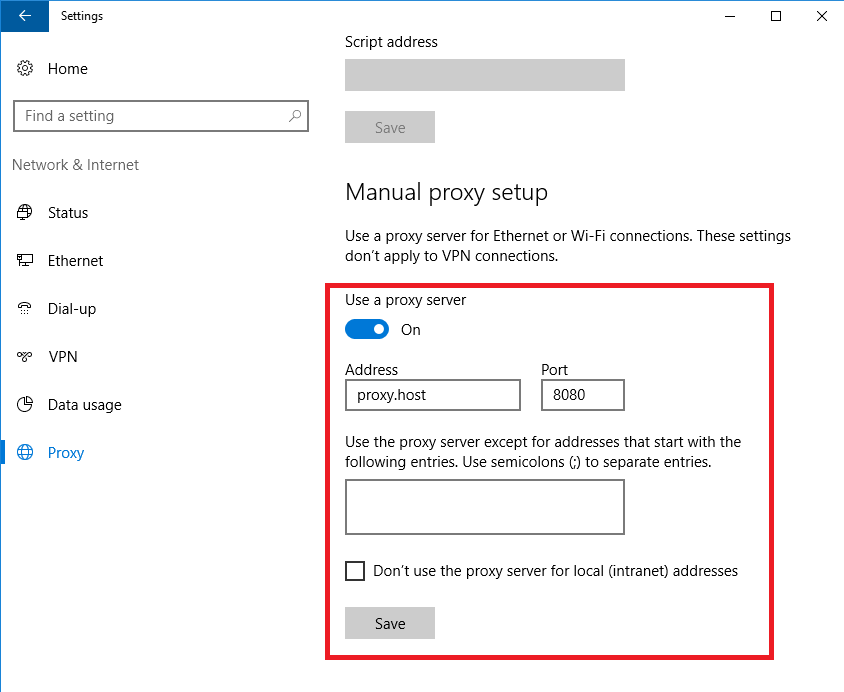
In the Start menu, open the Settings window.
Click Network & Internet.
Select Proxy, and set either of the following:
Set Use setup script to "On", enter the script address and click Save.
Set Automatically detect settings to "Off".
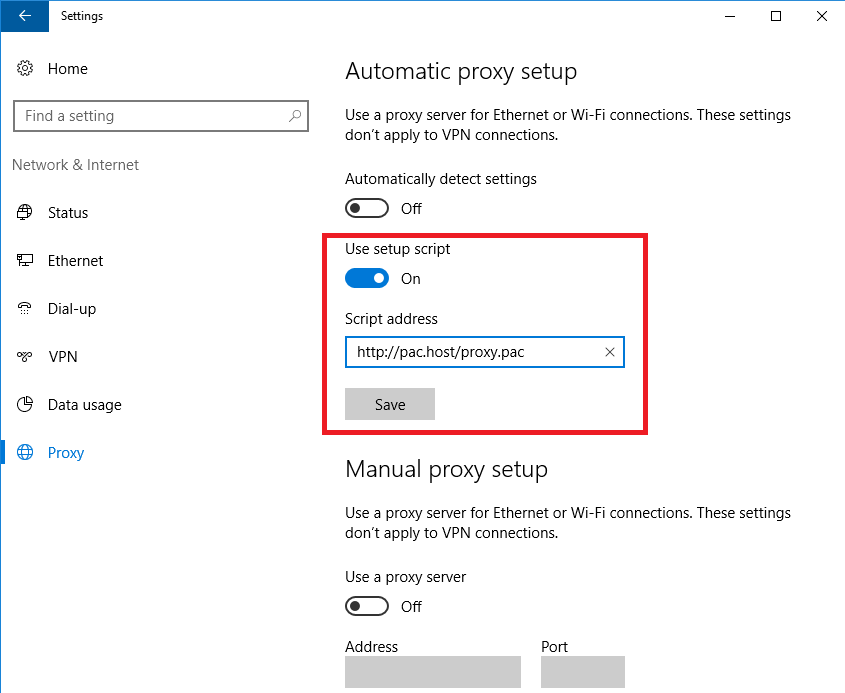
Set Use a proxy server to "On", enter the address and port, and click Save.
The supported web services and notes are as follows:
Web services | Notes |
|---|---|
Dropbox |
|
Dropbox Business | |
Google Drive |
|
Google Drive for Work | |
OneDrive | OneDrive (software that you install for use) is excluded as a target for monitoring. |
OneDrive for Business |
When some kind of specification changes are made to the web services provided by each company, it may no longer be possible to collect logs or prohibit web uploads or downloads.