Note
All IP configuration must be done prior to using CF over IP. The devices must be initialized with a unique IP address and a broadcast mask. IP must be configured to use these devices. If the configuration is not done, cfconfig(1M) will fail to load CF, and CF will not start.
The devices used for CF over IP must not be controlled by an RMS userApplication that could unconfigure a device due to Offline processing.
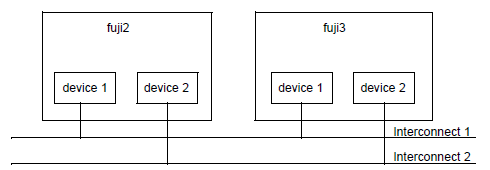
CF communications are based on the use of interconnects. An interconnect is a communications medium which can carry CF's link-level traffic between the CF nodes. A properly configured interconnect will have connections to all of the nodes in the cluster through some type of device. The figure below illustrates this configuration.
Figure 8.1 Conceptual view of CF interconnects
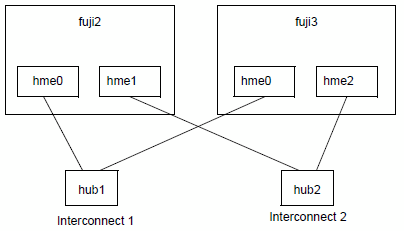
When CF is used over Ethernet, Ethernet devices are used as the interfaces to the interconnects. The interconnects themselves are typically Ethernet hubs or switches. An example of this is shown in the following figure.
Figure 8.2 CF with Ethernet interconnects
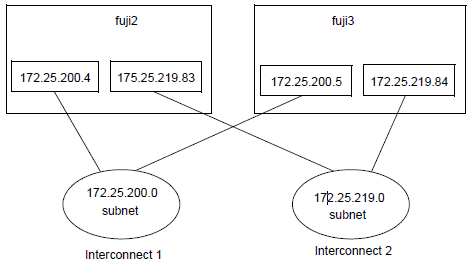
When using CF over IP, the IP interface is used as a device to connect to the interconnect and ensures redundancy using multiple IP subnetworks. The figure below illustrates the configuration of CF over IP.
Figure 8.3 CF with IP interconnects
It is also possible to use mixed configurations in which CF is run over both Ethernet devices and IP subnetworks.
When using CF over IP, you should make sure that each node in the cluster has an IP interface on each subnetwork used as an interconnect. You should also make sure that all the interfaces for a particular subnetwork use the same IP broadcast address and the same netmask on all cluster nodes. This is particularly important since CF depends on an IP broadcast on each subnet to do its initial cluster join processing.
Note
IPv4 address is used for CF over IP.
CF is not allowed to reach nodes that are on different subnets.
Note
When selecting a subnetwork to use for CF, you should use a private subnetwork that only cluster nodes can access. CF security is based on access to its interconnects. Any node that can access an interconnect can join the cluster and acquire root privileges on any cluster node. When CF over IP is used, this means that any node on the subnetworks used by CF must be trusted. You should not use the public interface to a cluster node for CF over IP traffic unless you trust every node on your public network.