The following figure shows how to use the Systemwalker Desktop Patrol client (security auditing and inventory collection) and the troubleshooting.
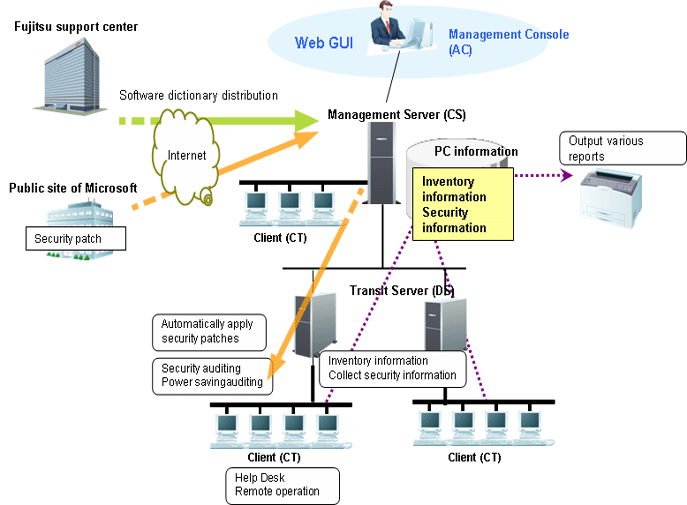
Receive the software dictionary
Receive and apply the software dictionary (used for detecting definition files of software and security patches) from manually download and apply.
Select management target software/security patches
Select the software that is used as the management target.
Besides, the software dictionary records security patch information that is automatically downloaded from Microsoft's public site. Select security patches that can be applied automatically.
Distribute/apply security patches
Automatic download the selected security patches from the public site of Microsoft.
Distribute and apply the downloaded security patches based on the operational configuration.
Collect inventory information
Software installation status and hardware information selected in the software dictionary can be collected automatically.
Besides, the application status of security patches can also be collected automatically.
Confirm
The administrator confirms the software installation status and hardware information.
The administrator can also determine whether the necessary security patches are applied.
Start the Live Help Client on the faulty PC.
The administrator uses the Live Help Expert function to connect to the client PC.
The administrator performs operations on the GUI of the client PC and rectifies faults.
The following figure shows the ICT assets management through Systemwalker Desktop Patrol.
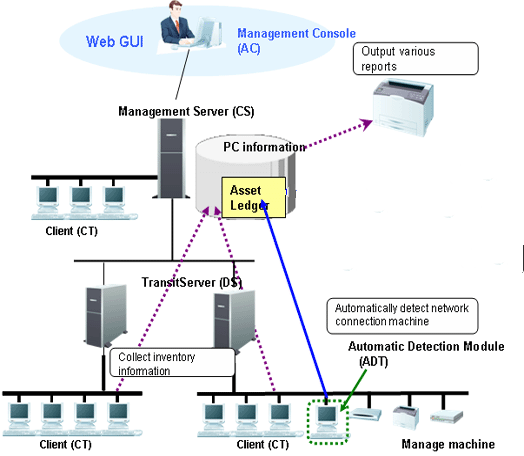
Register/ modify asset information
Perform either of the following methods to register/modify the asset information:
Register/ modify the inventory information
Register/ modify the inventory information collected by Systemwalker Desktop Patrol manually or automatically as the asset information managed by management ledger.
Register/ modify account
Register/ modify the asset information managed by management ledger (the asset information used to be considered as the account).
Register/ modify through device information auto-detected
The device information auto-detected by the ADT is notified to the CS automatically. The unregistered device information can be registered on the unregistered device management page, or you can enter all the registered device names and register them uniformly.
Register/ modify on the page
Register and modify the asset information respectively through the main menu.
Confirm the asset information
Perform either of the following methods to confirm the asset information:
Through the page
Confirm the device information, contract information, and checking status through the main menu.
Stocktaking Operation
Perform either of the following methods to check the asset information:
Collect the inventory information
Check the asset information through the inventory information collected from the PC.
Auto-Detect device information
Check the asset information through the device information detected automatically by ADT.
Set on the page
Set the stocktaking status (Checked/Not Checked) manually on the main menu.
Export reports
Export results of asset running status, contract status, and checking status in a report according to the asset information managed by management ledger, so that you can know and audit the usage.
Use the Virtual Private Network (VPN) to access the internal network of the company from outside. The following figure shows the system structure for mobile operation.
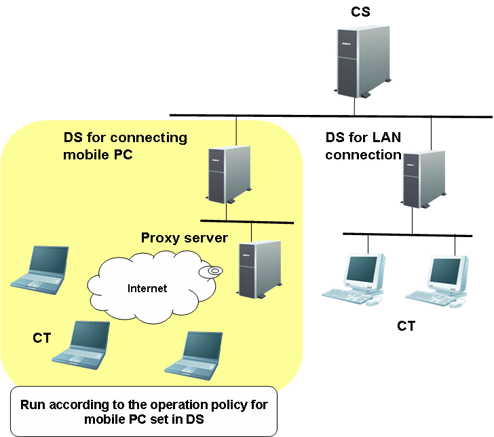
Set the DS for connecting to the PC for mobile operation, and set the running policy that the PC uses on the DS. Then the PC connects to the DS and runs according to the preset policy.
Assets management based on Systemwalker Desktop Patrol can also be performed in the mobile operating PCs which are not always connecting to the Internet.
System configuration for smart device assets management
To manage smart device assets, Systemwalker Desktop Patrol SS must be installed between the Systemwalker Desktop Patrol CS and smart device CT.
If collecting the smart device inventory information via the internet, install a reverse proxy server in the DMZ. The server must be operated in the recommended configuration shown below.
Smart device operation patterns
Smart devices are typically used on the company's intranet and in locations outside the company.
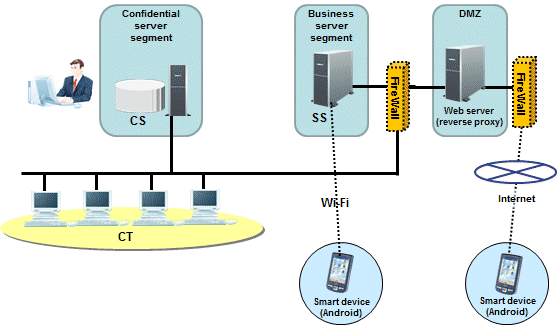
If the smart device assets are managed in an intranet environment only, then the Systemwalker Desktop Patrol SS and Systemwalker Desktop Patrol CS can coexist. To enable the SS and CS to coexist, the CS must be installed before the SS.
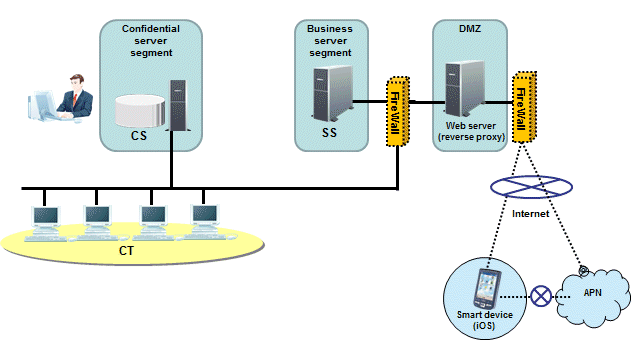
When using iOS devices to manage assets, it is necessary to have an environment in which Systemwalker Desktop Patrol SS and smart devices can connect to the APN (Apple Push Notification Service). Assets cannot be managed in an intranet environment.
System configuration supporting IPv6
IPv6 network configuration supported in Systemwalker Desktop Patrol is shown below.
Note
If the Systemwalker Desktop Patrol CS is in an IPv6-only environment, you will not be able to connect to the Systemwalker support center. For the CS, a dual stack environment must be built.
IPv6-only environment
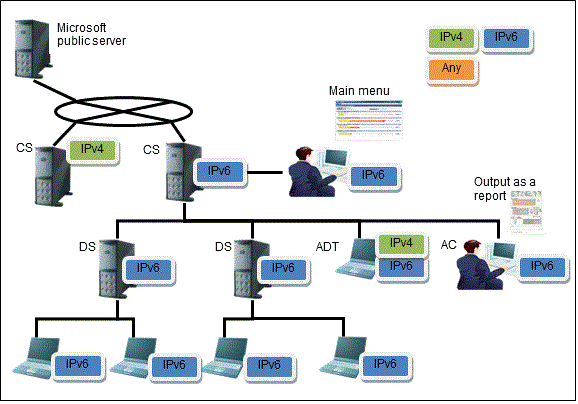
Function | Operation result |
|---|---|
Inventory information | IPv6 network information is collected in the CT, and IPv6 information can be viewed in the main menu. |
Network communication | Communication is performed using the IPv6 network environment. |
Unregistered device detection (ADT) | IPv6-only environment is not supported. |
Systemwalker support center | Only IPv4 is supported. |
CS | A dual stack environment must be built. |
IPv4 and IPv6 dual stack environment
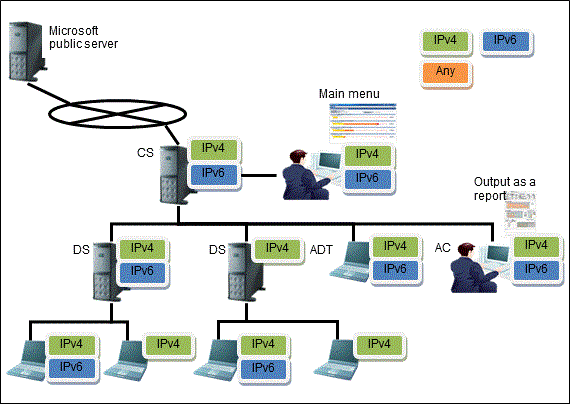
Function | Operation result | Note |
|---|---|---|
Inventory information | IPv4 and IPv6 network information is collected in the CS, and the IPv4 and IPv6 information can be viewed in the main menu. | If the collection target is V14.2.1 or earlier, then only the IPv4 information can be collected and viewed. |
Network communication | In a dual stack CT environment, communication is attempted with only the first IP address retrieved. |
Where IPv4 and IPv6 network environments coexist
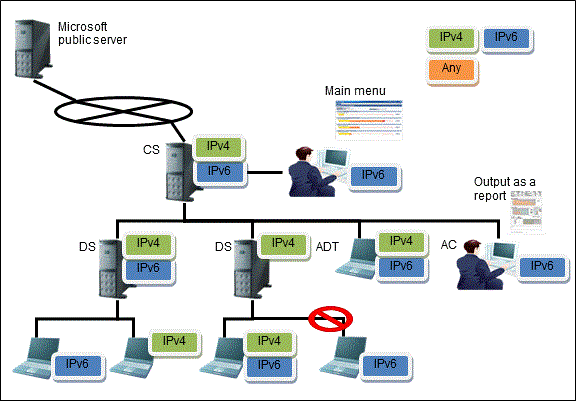
Function | Operation result | Note |
|---|---|---|
Inventory information | IPv4 and IPv6 network information is collected in the CT, and the IPv4 and IPv6 information can be viewed in the main menu.
| |
Network communication | Communication is performed as shown below:
| A downstream server in an IPv6-only environment cannot connect to an upstream server in an IPv4-only environment. Connection is possible only if the downstream server is also in an IPv4-only environment. |