Systemwalker Software Configuration Manager can manage the following resources managed by ServerView Resource Orchestrator or OpenStack server management software as server groups or servers by operating in coordination with the server management software. This enables management of patches, software parameters, and software configuration information for servers managed by server management software. For the procedure for linking to server management software, refer to "3.10 Setting up Related Software".
Server management software | Server group | Server |
|---|---|---|
ServerView Resource Orchestrator | L-Platform | L-Server |
OpenStack | Stack | Instance |
In Systemwalker Software Configuration Manager, the scope of the server groups and servers that are managed by the same server management software is called a site. It is possible to manage server groups and servers in the following three sites:
ServerView Resource Orchestrator
Server groups and servers managed using ServerView Resource Orchestrator
OpenStack
Server groups and servers managed using OpenStack
Manual registration
Server groups and servers that are not managed using ServerView Resource Orchestrator or OpenStack. They are registered using the command for defining environments for this product.
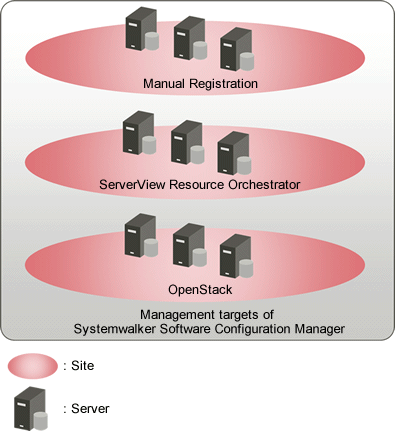
Server groups/server categories
The server groups and servers of Systemwalker Software Configuration Manager managed by each site are categorized into the following types. For how to manage the server groups and servers in each site, refer to "Server Group Management" and "Server Management" in the Operation Guide.
Manually registered server groups/servers
Server groups and servers managed using ServerView Resource Orchestrator
OpenStack server groups/servers
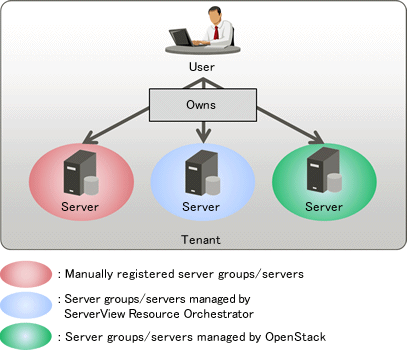
Decide the configuration of tenants, server groups, and servers keeping the following points in mind.
Server groups and servers in different sites can be managed in the same tenant.
The same user can own server groups in different sites.
A server group and all servers that belong to that server group must be in the same site.
This section explains design when the management target for this product is servers deployed on ServerView Resource Orchestrator, and this product is linked to ServerView Resource Orchestrator.
To link to ServerView Resource Orchestrator, install the admin server of this product on the same server as the admin server of ServerView Resource Orchestrator.
This section explains design when the management target for this product is servers deployed on OpenStack, and this product is linked to OpenStack.
To link to OpenStack, first install the admin server of this product separately from the admin server of OpenStack, and then configure the network that allows communication between OpenStack admin server and the deployed admin server.
Network configuration
In order to make OpenStack server groups and servers the management target of this product, an environment for performing communications with following OpenStack API services is necessary.
Keystone service
Nova service
Heat service
Connect the admin server of this product to the external OpenStack network so that the admin server of this product can communicate with the above API services.
In addition, to make the servers deployed on OpenStack the target of patch management, parameter management, and configuration management, install the business server of this product on the deployed servers, and then configure the environment so that the admin server and business servers of this product can communicate. Install the NIC for operation management on the controller node and the computing node and then connect it to the operation management network so the admin server and business servers of this product can communicate. On the controller node and the computing node, set a virtual switch for communication between the admin server and business servers of this product.
An example of the network configuration with an admin network and an operation management network configured is shown below.
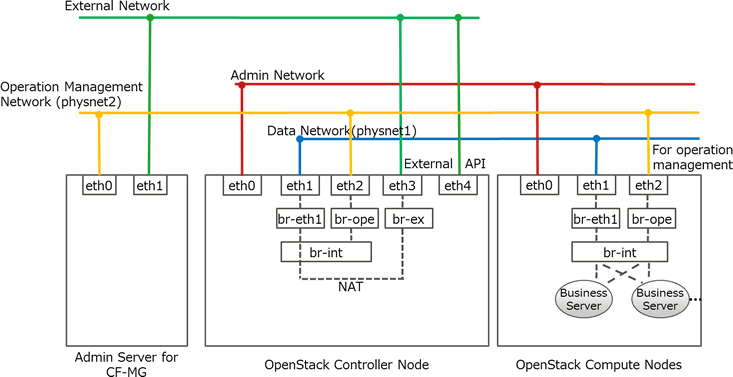
In this configuration, one NIC is connected to the external network of OpenStack so the admin server of this product can communicate with OpenStack API services. In addition, the NIC for operation management is installed on the controller node and the computing node, and connected to the operation management network so the admin server of this product can communicate with the business servers. On the controller node and the computing node, Open vSwitch is configured for enabling communication with business servers.
Note
Separate the network for communication between the admin server and business servers of this product from external networks and data networks in order to avoid affecting business traffic.
For security, configure the firewall correctly to prevent the business servers of this product from being accessed from external networks and data networks.