This section describes the procedures for installing CT to the virtual desktop.
According to the method for constructing the virtual desktop environment, method for installing CT need be modified.
It is described in this item according to the following order.
System structure of the virtual desktop environment
Install to virtual PC expanded on the virtual PC server
Install to the terminal server
Install to blade PC
System structure chart of virtual desktop environment (summary) is as follows:
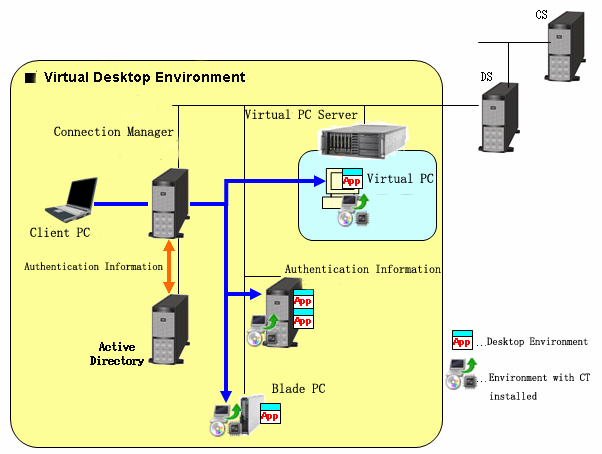
Virtual Desktop Environment
The user access "Desktop Environment" from Client PC via connection manager. Connection Management Server performs Active Directory authentication according to the requirements of Client PC and then distributes "Desktop Environment".
Desktop Environment
The desktop environment can be used in the following 3 cases
CT is installed to PC with license management software installed (virtual PC, terminal service, blade PC).
The virtual PC expanded on virtual PC server
Multiple virtual PCs in the virtual PC server are prepared and use this PC.
Terminal server
Physical PC is used.
Multiuser share the OS of the connection target and multiple desktop environments exist.
Blade PC
Physical PC is used.
The user uses the OS exclusively and single desktop environment exists.
When installing to the virtual PC expanded on the virtual PC server, the method for constructing desktop environment is divided to "when deployed automatically by system" and "when deployed manually by administrator".
Point
How to construct virtual desktop environment
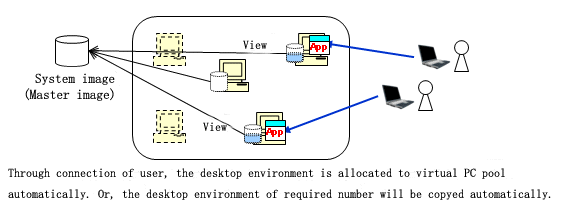
When deployed automatically by system (link clone and automatic desktop pool)
After the desktop environment is copied through system mapping, the desktop environment with the same content with system mapping will be created. Increment data of system mapping is accumulated on the virtual PC.
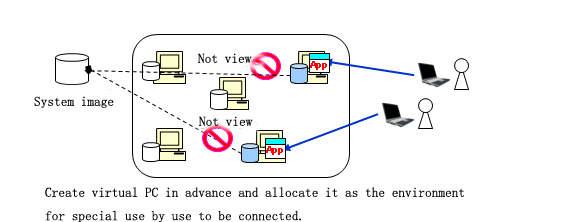
When deployed manually by the administrator (complete clone)
Create the desktop environment which has not viewed system mapping. Besides, create the dedicated virtual PC for connecting user and save all data containing OS to virtual PC.
The following describes CT installation procedures when using the following deployment method.
When deployed automatically by system (link clone and automatic desktop pool)
Create policy group and register the created Basic operation policy and PC.
After logging on to the main menu, click the Customize various policies button in the Environment Setup > Policy Groups window and click the link of policy name in the Basic Operation Policy tab, then the following window is displayed.
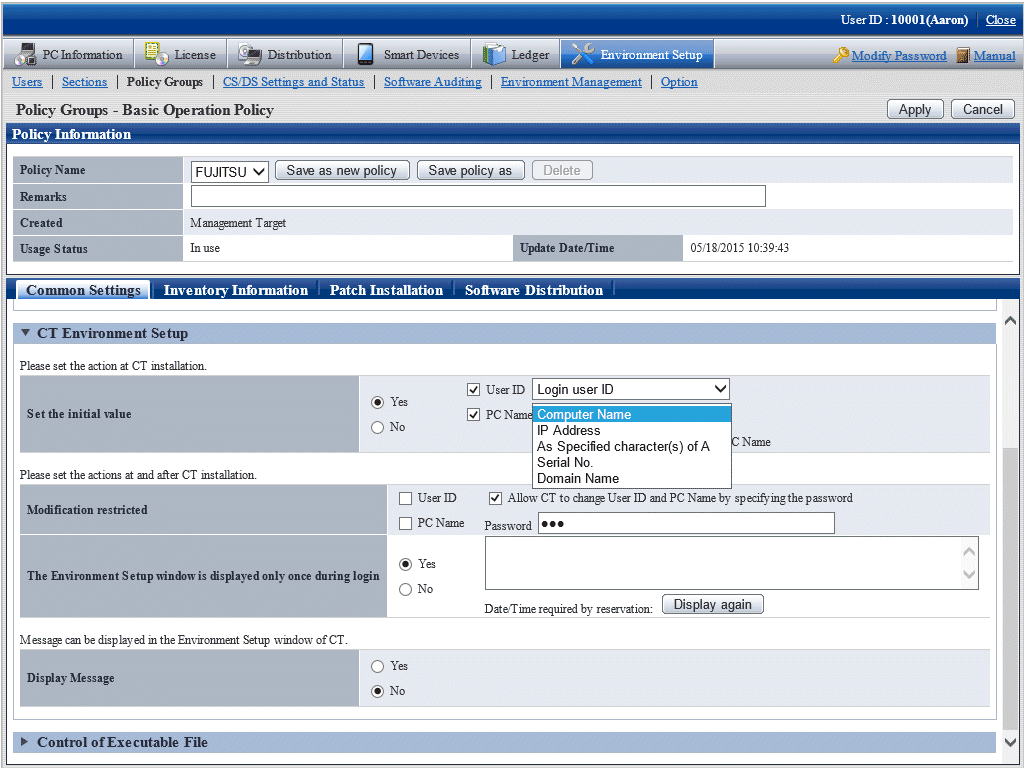
Perform CT Environment Setup > Set the initial value of the basic operation policy (Systemwalker Desktop Patrol Policy Setting).
Set "Logon user ID" in User ID. "Domain Name" is recommended in PC Name.
The administrator downloads CT Package through the download menu and installs CT Package in system mapping.
To deploy in the desktop pool, start the desktop environment through the virtual PC server.
CT detects the copying of the desktop and initializes user identification information.
Through the connection from Client PC, reset the user identification information.
CT judges the policy set in 1. and reset the user identification information based on the logon information.
If automatic resetting has not been set, define the user identification information through the environment setting window.
When deployed manually by the administrator (complete clone)
The administrator uses and installs Kitting CT Package in system mapping.
The administrator creates the virtual PC using system mapping and prepares the desktop environment.
The administrator uses DtpKitingCT.exe (CT operating environment change command) to define the user identification information (user ID, PC name, connection target server).
When installing to terminal server, install according to the procedures for installing common CT.
When installing to blade PC, install according to the procedures for installing common CT in case of not performing desktop copying (Master copying).
The procedures for installing CT if desktop copying (Master copying) between blades has been performed are as follows:
Create policy group and register the created Basic operation policy and PC.
After logging on to the main menu, click the Customize Various Policies button in the Environment Setup > Policy Groups window and click the link of policy name in the Basic Operation Policy tab, then the following window is displayed.

Perform CT Environment Setup > Set Initial Value of the basic operation policy (Systemwalker Desktop Patrol Policy Setting).
Set "Login user ID" in User ID and set "Computer Name" in PC Name.
The administrator downloads CT Package through the download menu and installs CT Package in system mapping.
The administrator or system performs desktop copying.
CT detects desktop copying and initializes the user identification information.
Through the connection from Client PC, reset the user identification information.
CT judges the policy set in 1., and reset the user identification information based on the logon information.
If automatic resetting has not been set, define the user identification information through environment setting window.