What is policy
Policy is the rules determined according to the guidelines for using the system.
It regulates the allowed operations, unallowed (prohibited) operations as well as information about which operation logs will be collected when the PC and smart device (Android device and iOS device) are being used.
Contents can be set in policy.
Policies of "Prohibited Operation" and "Log Collection Operation" can be set in Systemwalker Desktop Keeper.
The operations that can be prohibited by installing the client (CT) on the PC include those shown below. These policies are set in the Management Console by the system administrator or department administrator.
File Export Prohibition
File and folder export in drive, network drive, removable drive or DVD/CD can be prohibited conditionally.
According to the set condition, "File Export Utility" can be used to export files and folders from the prohibited drive.
Refer to Systemwalker Desktop Keeper User's Guide for Client for "File Export Utility".
Reading Prohibition
Reading of data on the removable drive, network drive or DVD/CD can be prohibited.
Printing Prohibition
Printing by non-specified applications can be prohibited.
PrintScreen Key Prohibition
The use of PrintScreen key for collecting the hard copy of screen can be prohibited. In this case, the type of screen hard copy to be collected becomes clear, and screen capture can be collected.
Logon Prohibition
Logon with the user name that belongs to a set group can be prohibited. The groups that can be prohibited are as follows:
Microsoft account
Application Startup Prohibition
Startup of the specified applications can be prohibited.
URL Access Prohibition
Access to the unauthorized URL can be prohibited.
FTP Server Connection Prohibition
Connection to the non-specified FTP server can be prohibited.
Web Upload and Download Prohibition
Upload and download to and from unauthorized websites can be prohibited.
Clipboard Operation Prohibition
Information transfer from the virtual environment to the physical environment or from the physical environment to the virtual environment via clipboard can be prohibited.
The operations that can collect logs by installing the client (CT) on the PC include those shown below. These policies are set in the Management Console by the system administrator or department administrator.
Application startup log
Application termination log
Application startup prohibition log
Window title obtaining log
E-mail sending log
Device configuration change log
Printing operation log
Printing prohibition log
Logon prohibition log
File export log
PrintScreen key operation log
PrintScreen key prohibition log
Web operation log
Web operation prohibition log
FTP operation log
FTP operation prohibition log
Clipboard operation log
Clipboard operation prohibition log
File operation log
Logon/Logoff log
Linkage log
The operations that can be prohibited by installing the smart device (agent) (Android) on the Android device include those shown below. These policies are set in the Management Console by the system administrator or department administrator.
Wi-Fi connection prohibition
Connection to the Wi-Fi access point set as a policy can be allowed or prohibited.
Bluetooth connection prohibition
Pairing with the Bluetooth device set as a policy can be allowed or prohibited.
Application usage prohibition
Use of application set as a policy can be allowed or prohibited.
The operations that can collect logs by installing the smart device (agent) (Android) on the Android device include those shown below. These policies are set in the Management Console by the system administrator or department administrator.
Wi-Fi connection log
Bluetooth connection log
Application usage log
Web access log
SD card mount/unmount log
SIM card mount/unmount log
Incoming/outgoing calls log
Application configuration change log
The operations that can be prohibited by installing the smart device (agent) (iOS) on the iOS device include those shown below. These policies are set in the Management Console by the system administrator or department administrator.
Device feature usage
Device feature usage, such as use of camera, screen capture, and Siri, set as a policy can be allowed or prohibited.
Application usage
Use of application such as YouTube, iTunes Store, and Safari set as a policy can be allowed or prohibited.
iCloud usage
iCloud usage such as backup to iCloud and document sync set as a policy can be allowed or prohibited.
Security and privacy settings
Data transfer to Apple, forced encryption backup and similar can be set as a policy.
Content ratings settings
Viewing of contents (movies, TV programs, Apps) can be set as a policy.
Policy Settings Targets
The name of policy varies according to the settings of the defined policy.
The policy set for the "client (CT)" and "smart device (agent)" is called "CT policy".
When setting policy for the "User", it is called "User Policy". The "user policy" cannot be set for the "smart device (agent)".
The policy set for the "client (CT)" and "smart device (agent)" is called "CT policy". During the client (CT) and smart device (agent) operation, when the CT policy is valid, the prohibition and log collection will be implemented according to the policies set in the client (CT) and smart device (agent), no matter which user performs operation. Different policies can be set for each client (CT) and smart device (agent).
In addition, the clients (CTs) and smart devices (agents) can be grouped by department or purpose, and the policy set for the group is called a CT group policy. Different policies can be set for each group.
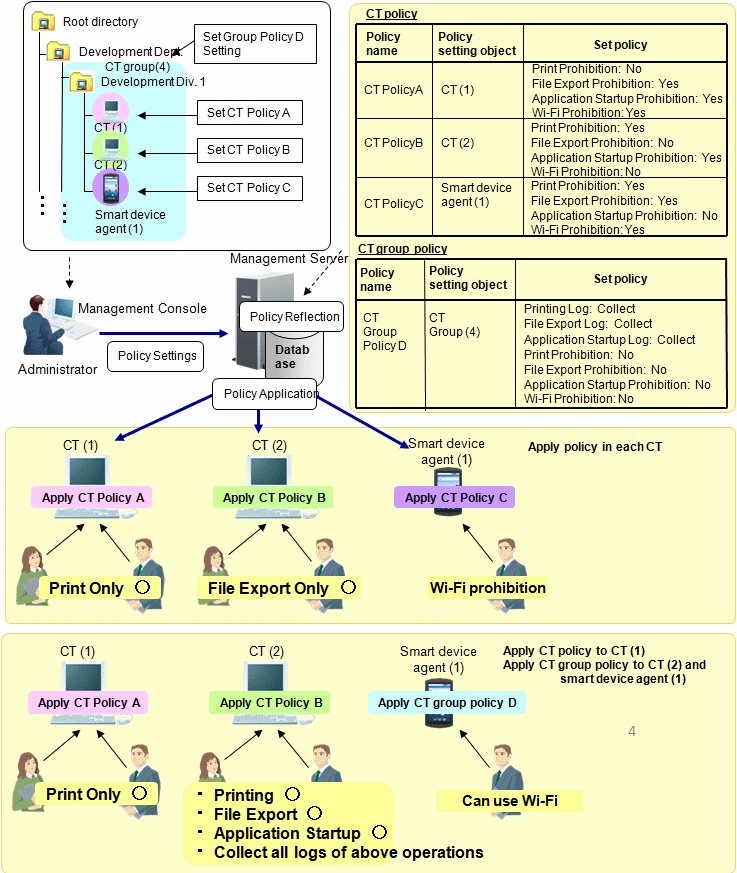
In the above image, the following settings can be performed for the client (CT), smart device (agent), and CT group through the Management Console.
The following policies can be set for each client (CT) and smart device (agent).
Settings for both the client (CT) (such as print prohibition and file export prohibition) and smart device (agent) (such as Wi-Fi prohibition and Bluetooth connection prohibition) can be configured for one CT policy.
If the CT policy is applied to the client (CT), the settings for the client (CT) will be enabled, and likewise if the CT policy is applied to the smart device (agent), the settings for the smart device (agent) will be enabled.
CT (1) Printing only.
Printing prohibition: No (Enabled)
File export prohibition: Yes (Enabled)
Application startup prohibition: Yes (Enabled)
Wi-Fi connection prohibition: Yes (Disabled)
CT (2) File export only.
Printing prohibition: Yes (Enabled)
File export prohibition: No (Enabled)
Application startup prohibition: Yes (Enabled)
Wi-Fi connection prohibition: No (Disabled)
Wi-Fi cannot be used on the smart device (1).
Application usage prohibition: No (Disabled)
Wi-Fi connection prohibition: Yes (Enabled)
Group the clients (CTs) and smart devices (agents) and set the group policy to allow printing, file export, and application startup, and also collect all the logs.
CT policy will be applied to each client and smart device (agent) immediately or at the next startup. After policy has been applied, the client (CT) and smart device (agent) will run according to the applied policy.
CT (1) No matter who operates, only printing is allowed.
CT (2) No matter who operates, only file export is allowed.
Wi-Fi usage is prohibited on the smart device agent (1).
CT (1) No matter who operates, only printing is allowed .
CT (2) No matter who operates, printing, file export, application startup can be performed, and the logs of each operation will be collected.
Wi-Fi usage is allowed on the smart device agent (1).
The policy set for the user name that is input during logon to Windows in the PC with the client (CT) installed is called User Policy. During the client (CT) operation, when the user policy is valid, the prohibition and log collection can be implemented according to the policies set for the logon user name regardless of the PC on which the operation is performed. Different policies can be set for each user.
In addition, the users can be grouped by department, and after the clients (CTs) with same operation content can be divided into one group, and the policy set for this group is called user group policy. Different policies can be set for each group.
Note that the user policy and user group policy cannot be set for the smart device (agent).
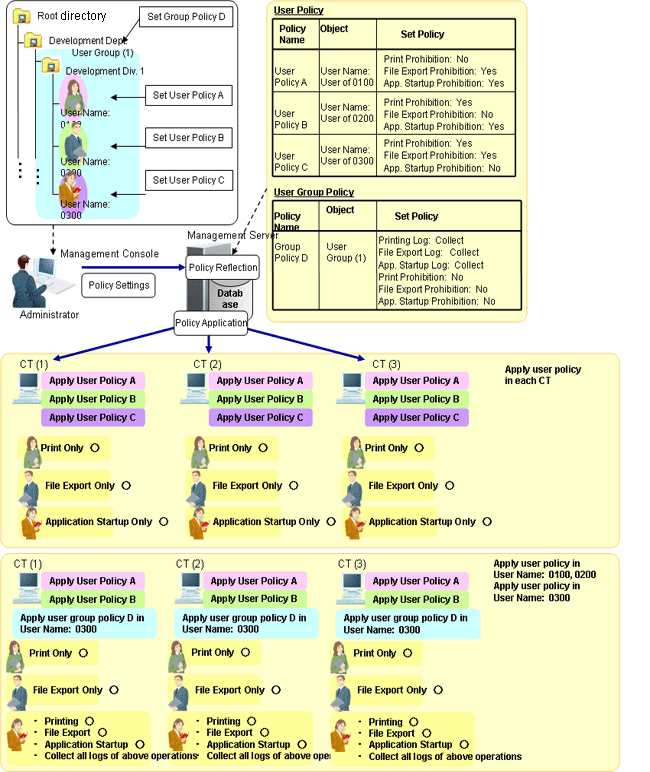
In the above image, the following settings can be performed for the user and user group through the Management Console.
The following policies can be set for each user name:
User name: 0100 user can only print.
Printing prohibition: No
File export prohibition: Yes
Application startup prohibition: Yes
User name: 0200 user can only export files.
Printing prohibition: Yes
File export prohibition: No
Application startup prohibition: Yes
User name: 0300 user can only start applications.
Printing prohibition: Yes
File export prohibition: Yes
Application startup prohibition: No
Group the users and set the group policy to "Allow Printing, File Export and Application Startup" and "Collect All Logs".
After logon to Windows by each user name, correspondent user policy can be applied. After the policy is applied, it has nothing to do with the CT policy of the client (CT). Instead, operation will be performed according to user policy only.
Regardless of the client (CT) on which logon occurs, all operations that can be performed by the user have been determined.
User name: 0100 user can only print.
User name: 0200 user can only export files.
User name: 0300 user can only start applications.
Regardless of the client (CT) on which logon occurs, all operations that can be performed by the user have been determined.
User name: 0100 user can only print.
User name: 0200 user can only export the file.
User name: 0300 user can print, export files and start applications, and logs of each operation will be collected.
CT Policy/User Policy and Items can be Set
The items that can be set in the CT policy are different from those can be set in user policy. The items that can be set are as follows:
Settings Items | CT Policy | User Policy | |||
|---|---|---|---|---|---|
Client | Smart device (agent) (Android) | Smart device (agent) (iOS) | Client | ||
Prohibition Function | File export prohibition | Y | N | N | Y |
Reading prohibition | Y | N | N | Y | |
Printing prohibition | Y | N | N | Y | |
PrintScreen key prohibition | Y | N | N | Y | |
Logon prohibition | Y | N | N | N (Note) | |
Application startup prohibition | Y | N | N | Y | |
E-mail attachment prohibition | Y | N | N | Y | |
URL access prohibition | Y | N | N | Y | |
FTP server connection prohibition | Y | N | N | Y | |
Web upload and download prohibition | Y | N | N | Y | |
Clipboard operation prohibition | Y | N | N | Y | |
Wi-Fi connection prohibition | N | Y | N | N | |
Bluetooth connection prohibition | N | Y | N | N | |
Application usage prohibition | N | Y | N | N | |
Device feature usage | N | N | Y | N | |
Application usage | N | N | Y | N | |
iCloud usage | N | N | Y | N | |
Security and privacy settings | N | N | Y | N | |
Content ratings settings | N | N | Y | N | |
Record Function | Application startup log | Y | N | N | Y |
Application termination log | Y | N | N | Y | |
Application startup prohibition log | Y | N | N | Y | |
Window title obtaining log | Y | N | N | Y | |
E-mail sending log | Y | N | N | Y | |
E-mail sending interruption log | Y | N | N | Y | |
E-mail attachment prohibition log | Y | N | N | Y | |
Command log | Y | N | N | Y | |
Device configuration change log | Y | N | N | Y | |
Printing operation log | Y | N | N | Y | |
Printing prohibition log | Y | N | N | Y | |
Logon prohibition log | Y | N | N | N (Note) | |
File export log | Y | N | N | Y | |
PrintScreen key operation log | Y | N | N | Y | |
PrintScreen key prohibition log | Y | N | N | Y | |
Web operation log | Y | N | N | Y | |
Web operation prohibition log | Y | N | N | Y | |
FTP operation log | Y | N | N | Y | |
FTP operation prohibition log | Y | N | N | Y | |
Clipboard operation | Y | N | N | Y | |
Clipboard operation prohibition log | Y | N | N | Y | |
File operation log | Y | N | N | N (Note) | |
Logon/Logoff log | Y | N | N | N (Note) | |
Linkage log | Y | N | N | N (Note) | |
Screen capture | Y | N | N | Y | |
Wi-Fi connection log | N | Y | N | N | |
Wi-Fi connection prohibition log | N | Y | N | N | |
Bluetooth connection log | N | Y | N | N | |
Bluetooth connection prohibition log | N | Y | N | N | |
Application usage log | N | Y | N | N | |
Application usage prohibition log | N | Y | N | N | |
Web access log | N | Y | N | N | |
SD card mount/unmount log | N | Y | N | N | |
SIM card mount/unmount log | N | Y | N | N | |
Incoming/outgoing calls log | N | Y | N | N | |
Application configuration change log | N | Y | N | N | |
Y: can be set
N: cannot be set
Note: During the client (CT) operation, when the user policy is valid, for the items that cannot be set as user policy, the configuration value of CT policy in the operated the client (CT) is valid.
Form of Operation and Valid Prohibition/Log Collection
After the CT policy and user policy have been set and updated to the client (CT), though operation prohibition and log collection can be performed in the client (CT), the valid prohibition is different from the collected logs according to the form of operation.
The valid items are shown as follows:
In addition, functions may be restricted due to the operating environment. Refer to "1.2 Notes Relating to Functions " for details.
Form of operation | When recording the operations of the client (CT) of Systemwalker Desktop Keeper | ||
|---|---|---|---|
OS Startup Mode | At normal startup (Logon to Windows after OS has started) | When starting in safe mode or the safe mode with network (Note 2) (Note 3) | |
Windows Vista(R) | |||
Prohibition Function | File export prohibition | Y | Y |
Printing prohibition | Y | N | |
PrintScreen key prohibition | Y | Y | |
Logon prohibition | Y | Y | |
Application startup prohibition | Y | Y | |
E-mail attachment prohibition | Y | N | |
URL access prohibition | Y | Y | |
FTP server connection prohibition | Y | Y | |
Web upload and download prohibition | Y | Y | |
Clipboard prohibition | Y | Y | |
Record Function | Application startup log | Y | Y |
Application termination log | Y | Y | |
Application startup prohibition log | Y | Y | |
Window title obtaining log | Y | Y | |
Window title obtaining log (with URL) | Y | Y | |
E-mail sending log | Y | N | |
E-mail sending interruption log | Y | Y | |
E-mail attachment prohibition log | Y | N | |
Command log | Y | Y | |
Device configuration change log | Y | Y | |
Printing operation log | Y | N | |
Printing prohibition log | Y | N | |
Logon prohibition log | Y | Y | |
File export log | Y | Y | |
PrintScreen key operation log | Y | Y | |
PrintScreen key prohibition log | Y | Y | |
Web operation log | Y | Y | |
Web upload prohibition log | Y | Y | |
Web download prohibition log | Y | Y | |
FTP operation log | Y | Y | |
FTP operation prohibition log | Y | Y | |
Clipboard operation log | Y | Y | |
Clipboard operation prohibition log | Y | Y | |
File operation log | Y | Y | |
Logon/Logoff log | Y | Y (Note 1) | |
Linkage log | Y | Y | |
Screen capture | Y | Y | |
Y: Valid
N: Invalid.
Note 1: PC sleep logs and PC restoration logs are not collected.
Note 2: When starting in safe mode or if the network is in safe mode, only the CT policy will be running while the user policy will not be applied.
Note 3: When starting in safe mode or safe mode with network, sometimes the operation logs will not be sent to the Management Server before the next normal startup.
Setting policy on personal devices
For personal devices for business use, protection of the owner's privacy and business data integrity must both be achieved. Determine the policy based on the example shown below:
Do not retrieve the operation logs
From the perspective of privacy protection, retrieval of the operation logs from personal devices should be avoided.
Ensure that the operation logs are "not retrieved" for the settings on personal devices.
Avoid unnecessary prohibition settings
Personal devices can be used for private use also, and therefore care should be taken for setting prohibition features.
Set prohibition features carefully so that the devices in private use will not be affected.
Manage applications to be used for business
Use the feature to prohibit application usage outside business hours to restrict the business application usage on personal devices to within business hours only. By prohibiting the use of business applications during private time, information leakage can be prevented.
Prohibit the use of applications that trigger off information leakage
Create a blacklist of applications which clearly should not be used (because they may trigger information leakage) on personal devices also, and prohibit the use of such applications. By prohibiting the use of applications on devices that can also be used for business, information leakage can be prevented.
Note that, for Android devices on which Systemwalker Desktop Patrol V15.1 or later is installed, personal devices can be identified as such by referring to Systemwalker Desktop Patrol. Refer to the Systemwalker Desktop Patrol Operation Guide: for Administrators for details.