In Systemwalker Operation Manager, encrypted communication (SSL: Secure Socket Layer) is used for communication between the Web server and the Web Console. This section explains the certificate and key management environment required to use SSL.
Certificates and private keys
To use SSL, the Certificate Authority (CA) certificate, site certificate, and the corresponding private keys are required. Also, a CRL (Certificate Revocation List) is used to check the certificate validity.
A certificate and CRL that conforms to either X.509 or RFC2459, and uses the RSA cipher algorithm to generate keys, can be used.
CA certificates
This is the certificate of the CA itself. This certificate guarantees certificates issued by the CA.
The CA can issue a certificate to a subordinate CA. In this case, the CA's certificate and the subordinate CA's certificate are both called CA certificates. However the subordinate CA's certificate is also called an intermediate CA certificate.
Site certificates
This is a certificate issued by the CA that guarantees the identify of a server. It contains information related to the server and the CA. The site certificate must be used in combination with the CA's certificate. A certificate's validity period is contained in the certificate itself, and cannot be used once it has expired. The certificate must be updated and a new one obtained before it expires. Refer to "Updating Certificates (When Certificates Expire" in the Systemwalker Operation Manager Installation Guide for more information.
The private key that corresponds to the site certificate
This is the key that is paired with the public key contained in the site certificate.
Note
If the private key is lost, the corresponding site certificate cannot be used. For this reason, it must always be backed up.
CRL (Certificate Revocation List)
The CA issues the CRL, which includes a list of invalid certificates that were issued by that CA. Examples of events that will expire or invalidate a certificate are the theft of a private key or the loss of user credentials.
If this is used in SSL communication, it will be referenced when the destination server's certificate is checked for validity.
The CRL is issued periodically, and is released to each Web server or directory server that is managed by the CA. The release method is different depending on the CA system, so check with the CA. Note that the release location might be described in the certificate.
Certificate Authority (CA)
A CA is required to obtain a certificate.
In certificate and key management environments, certificates and CRLs are supported when they are issued by one of the following:
VeriSign, Inc.
Supports the Secure Site and Secure Site with EV (EV SSL Certificates).
Cybertrust, Inc.
Supports SureServer for SSL Certificates.
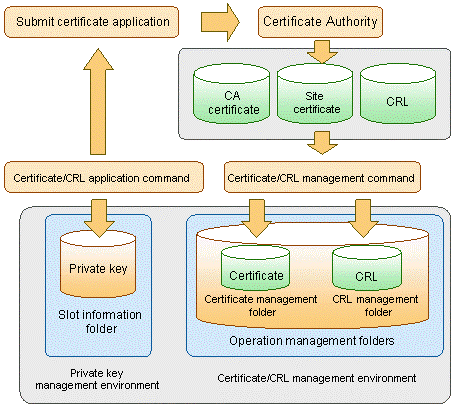
Image of the certificate/key management environment
An image of the certificate and key management environment is shown below:
Method used to manage private keys
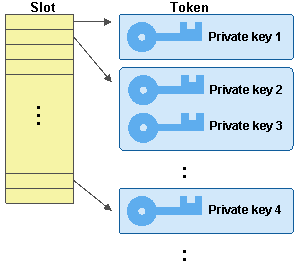
In private key management, the private key is handled according to the concept of slot and token.
Slot is an abstraction for a physical device which can load encryption equipment, and a token is an abstraction for the encryption equipment.
Only one token can be assigned to a slot, however multiple private keys can be registered in a token.
The relationship between the slots, tokens, and private keys is shown below:
The slot password is required for operations to process the slot information. SO-PIN, or the user PIN, is required for operations to process the token information. The respective passwords are set when the slots and tokens are generated. Note that SO-PIN is only a setting, and is not used in normal operations.
The user PIN is the information required for authentication when the private key in the token is accessed (when the private key is generated using the cmmakecsr command). Since the user PIN exists in each token, if multiple private keys have been registered in one token, information about the private keys can be accessed using a single user PIN.
The relationship between the password and PIN for the slot and token is shown in the table below:
Type | Number | Main use |
|---|---|---|
Slot password | One per slot | Generation of the token |
SO-PIN | One per token | - |
User PIN | One per token | Private key access |