Design virtual systems for users.
When designing virtual systems, the following information needs to be defined beforehand:
Resource requirements
Whether to use firewalls
If security must be maintained for each virtual system, deploy firewalls.
Firewalls should also be deployed when using a hierarchical configuration that establishes an intranet connected with a DMZ.
Whether to use server load balancers
If server load balancing needs to be performed for each virtual system, deploy server load balancers.
Server type (physical L-Server or virtual L-Server)
Whether to use iSCSI (Storage)
Information
When deploying both a firewall and a server load balancer, an L2 switch may be necessary between the firewall and server load balancer depending on device specifications. Therefore, check the specifications of the firewall and server load balancer beforehand.
Communication route configuration
It is normal to use a redundant configuration for communication routes.
Communication performance assumption (throughput)
Define the assumed communication performance for each system.
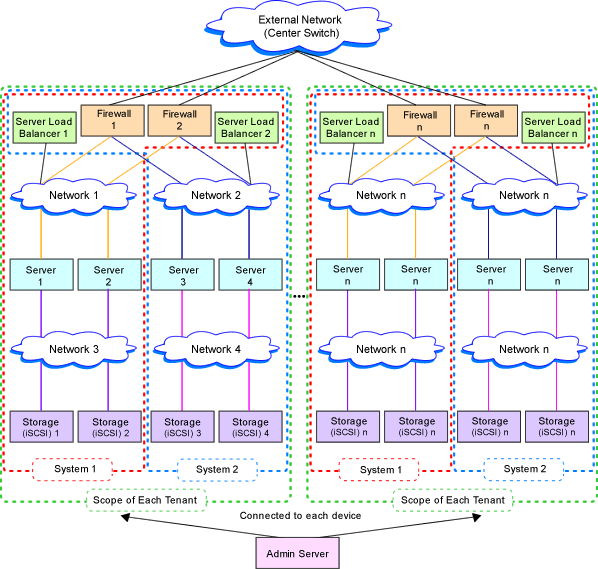
Figure 9.5 Example of Virtual System Configuration Elements
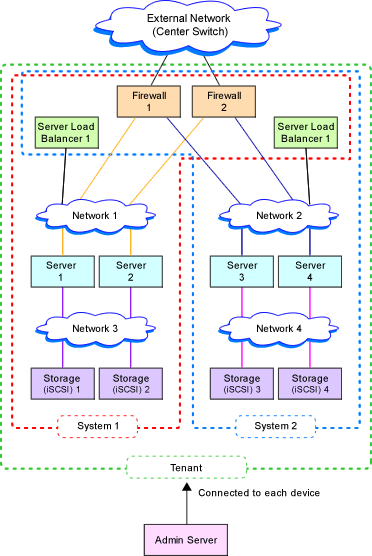
Figure 9.6 Example of Overall Configuration of a Virtual System (A Collective of Virtual System Configuration Elements)